Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
What is Zepto File Virus and How to Remove The Ransomware?
This article is created to help you remove Zepto file virus. Here you can find detailed removal instructions which work with all versions of Windows. That is important because the virus you’re now stuck with infects all of them. Yes, this pest causes an immense headache. Coming across any ransomware-type parasite is a terrible experience so you’re in for trouble. As you could imagine, hackers constantly work on new infections of this kind. The number of ransomware-type viruses online is raising at an alarming speed for one very simple reason. Money. These parasites offer crooks an easy way to gain illegitimate profit. Obviously, that makes them extremely dangerous. The parasite currently on your PC system is a classic ransomware. It was discovered just a couple of days ago; however, it already managed to cause many people damage. That’s actually a new version of Locky – a ransomware we’ve tackled in previous articles. If you’ve come across Locky Ransomware, you’re perfectly aware how devastating this new program is. One significant difference between the two is the file extension they add. While Locky leaves infected files with .locky appendix, this virus adds .Zepto. They both create a 16-symbol ID that gets added to the file name as well. The encrypted data looks like this – [first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].zepto. 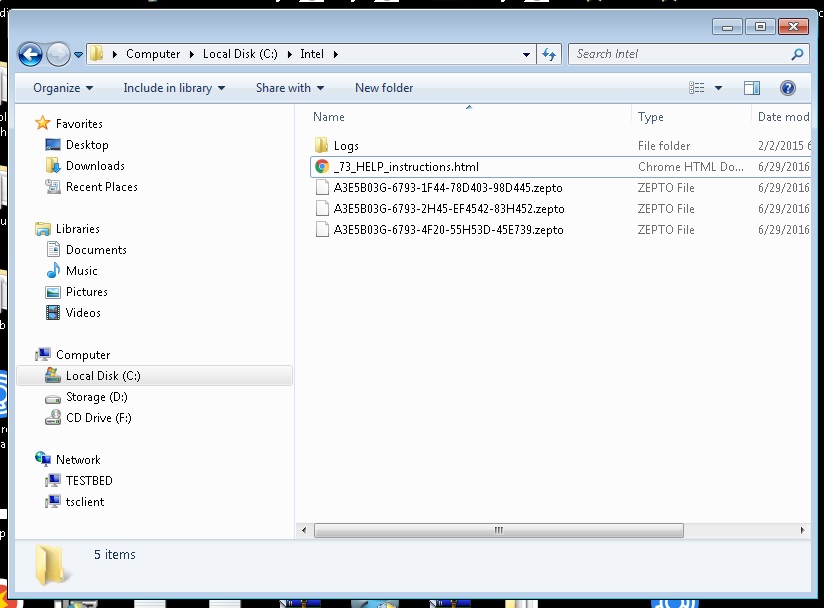 Once your files get renamed, consider them gone. The virus uses a highly complicated encrypting algorithm. Thanks to this cipher, your personal data is no longer accessible. We’re talking favorite music, important Microsoft Office documents, presentations, videos, pictures, etc. Do you now see why ransomware is so dreaded? This is the type of program nobody wants to deal with. After encrypting your files, this pest holds it hostage. You can no longer open or use your data. That happens because your infected files have a brand new file format that the PC is unable to read. Thus, your entire private information gets locked and is now inaccessible and practically useless. Being very aggressive, the parasite takes down a huge variety of file formats. It encrypts .mp3, .mp4, .rar, .png, .txt, .map, .pdf, .jpeg, .jpg, .ppt, .crw, .xls, .doc, .docx files and many more. Anything of value you might have stored on the PC falls victim to the ransomware. In addition, this program drops payment instructions named _72_HELP_instructions.html.
Once your files get renamed, consider them gone. The virus uses a highly complicated encrypting algorithm. Thanks to this cipher, your personal data is no longer accessible. We’re talking favorite music, important Microsoft Office documents, presentations, videos, pictures, etc. Do you now see why ransomware is so dreaded? This is the type of program nobody wants to deal with. After encrypting your files, this pest holds it hostage. You can no longer open or use your data. That happens because your infected files have a brand new file format that the PC is unable to read. Thus, your entire private information gets locked and is now inaccessible and practically useless. Being very aggressive, the parasite takes down a huge variety of file formats. It encrypts .mp3, .mp4, .rar, .png, .txt, .map, .pdf, .jpeg, .jpg, .ppt, .crw, .xls, .doc, .docx files and many more. Anything of value you might have stored on the PC falls victim to the ransomware. In addition, this program drops payment instructions named _72_HELP_instructions.html.
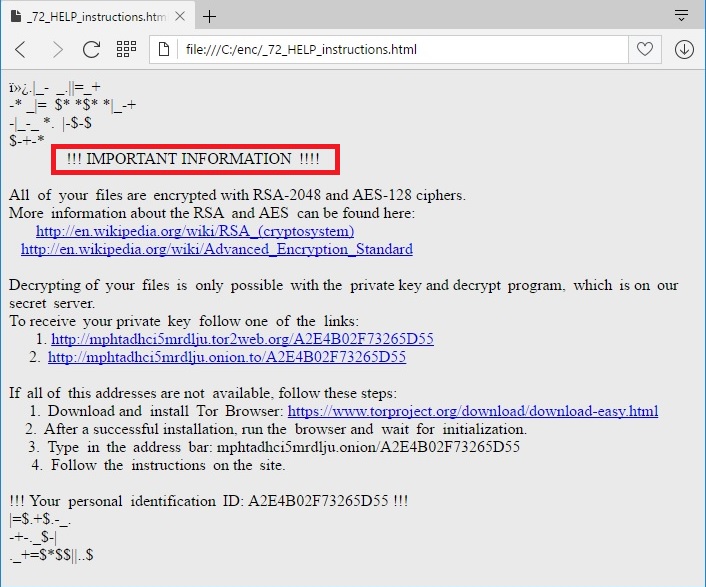
The ransom note reads the following:
!!! IMPORTANT INFORMATION !!!
All of your files are encrypted with RSA-2048 and AES-128 ciphers.
More information about the RSA and AES can be found here:
https://en.wikipedia.org/wiki/RSA_(cryptosystem)
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
Decrypting of your files is only possible with the private key and decrypt program, All which is on our secret server.
To receive your private key follow one of the links:
1. http://mphtadhci5mrdlju.tor2web(.)org/
2. http://mphtadhci5mrdlju.onion(.)to/
If all of this addresses are not available, follow synthesis steps:
1. Download and install Tor Browser: https://www.torproject.org/download/download-easy(.)html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar: mphtadhci5mrdlju(.)onion/
4. Follow the instructions on the site.
!!! Your personal identification ID: !!!
Yes, you’re supposed to PAY hackers in order to restore your very own data. Crooks demand a large sum of money in bitcoin (online currency amounting around 300 USD) and promise a decryption key in exchange. The problem is, you should never make a deal with criminals. And if you pay, you’re falling straight into crooks’ trap.
How did I get infected with?
The most likely scenario is that this virus was attached to a malicious email/ message. You should be extra careful when you notice anything suspicious in your inbox. Delete what you don’t trust and make sure you protect your safety. Keeping the device virus-free should always be your number one priority online. Apart from messages and email-attachments, ransomware travels the Web in freeware/shareware bundles. Therefore, avoid unverified pages and the illegitimate bundles they offer. It’s crystal clear that infections apply many techniques to get spread on the Web. That makes it so much harder for PC users to prevent virus infiltration. You also have to stay away from unreliable torrents and third-party pop-ups. Pay attention to your machine before it’s too late. Remember, uninstalling a virus takes much more time and energy (and nerves) than keeping the computer safe in the first place.
Why is Zepto dangerous?
Immediately after installation, the virus performs a scan on your PC. This way it locates all your files in order to encrypt them. As mentioned, this parasite adds a .Zepto extension to the target data. By doing so, this pest effectively locks out your access to all the information you’ve stored on board. While encrypting your data, the parasite also creates .txt and .html files which contain a ransom message. This message’s role in the ransomware scheme is particularly unpleasant. By preying on the fact many people would give into panic and anxiety, hackers are aiming for revenue. However, their profit would come solely at your expense. Restrain yourself from paying hackers anything because that is how you get scammed. Cyber criminals may promise a decryption key but there’s no guarantee they will keep their end of the bargain. You may end up with your PC still compromised, your files still encrypted, your money gone and your private details exposed. Does that sound like fun? It isn’t. In order to delete the virus manually, please follow the removal guide you’ll find down below.
Zepto Ransowamre Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Identify and Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zepto Encrypted Files
WARNING! Stopping the wrong file or deleting the wrong registry key may damage your system irreversibly.
If you are feeling not technical enough you may use Spyhunter professional Zepto Removal Tool. However, only the Scanner is free, in order to remove the ZEPTO Files virus completely you need to purchase full version. >>Download SpyHunter – a professional .Zepto scanner and remover.
>>Download SpyHunter – a professional .Zepto scanner and remover.
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware.
- Before you kill the process, type the name on a text document for later reference and to be able to delete it.

- Locate any suspicious processes associated with Zepto encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zepto encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
HKCU\Control Panel\Desktop\SCRNSAVE.EXE “%AppData%\[random].exe”
HKCU\Software\Microsoft\Command Processor\AutoRun “%AppData%\[random].exe”
HKCU\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run “%AppData%\[random].exe”
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] “%AppData%\\[random].exe”
HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] “%AppData%\\[random].exe”
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
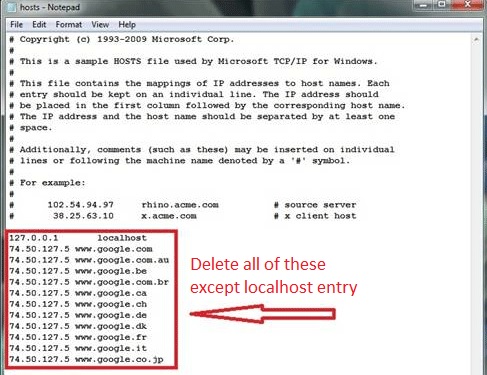
If you are uncertain about the IPs below “Localhost” contact us in out google+ profile and we will try to help you.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

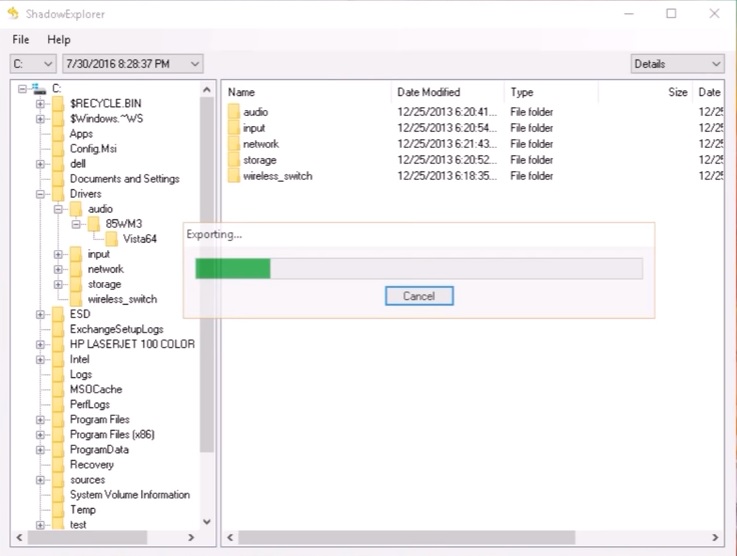
- Method 2: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.
- Method 3: Network Sniffer – Another way to mitigate the damage is to intercept the encryption key via Network Sniffer. This is a program that is capable of monitoring data traveling over the network. However this is quite complicated and the data within the network packet might be also encrypted.
- Method 4: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.


