Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CrypMIC Ransomware?
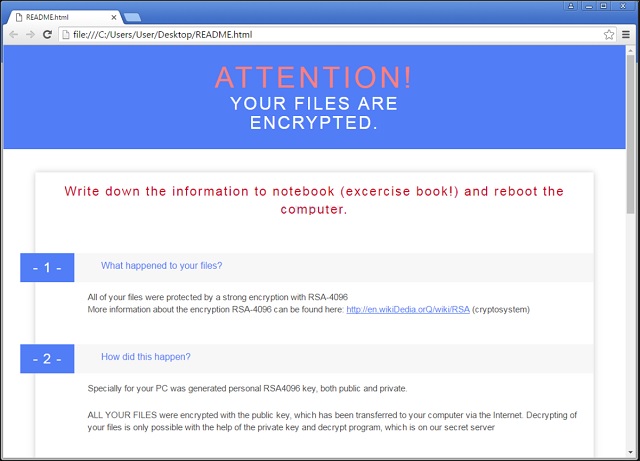
Reader recently start to report the following message being displayed when they boot their computer:
What happened to your files?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: [link to Wikipedia]
How did this happen?
!!! Specially for your PC was generated personal RSA4096 Key, both public and private/
!!! ALL YOUR FILES were encrypted with the public key which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decryption program, which is on our Secret Server
What do I do?
So, there are two ways you can choose: wait for a miracle and get your PRICE DOUBLED! Or start obtaining *BITCOIN NOW!, and restore YOUR FILES
If you have really valuable DATA, you better NOT WASTE YOUR TIME, because there is NO other way to get your files except make a payment.
Your personal ID: [random string of characters]
CrypMIC Ransomware gives you one more reason to be careful online. Nobody wants to deal with ransomware, that’s a given. CrypMIC is quite similar to CryptXXX and UltraCrypter. It uses the complicated RSA-4096 encrypting algorithm and locks your data. All your pictures, music, Microsoft Office documents, videos, presentation. All private data you’ve stored on your computer falls victim to the ransomware. This virus locks a rich variety of file formats – .mp3, .mp4, .txt, .xls, pdf, png, .odt, .map, .mdf, etc. Obviously, some incredibly important information might get encrypted as well. Before you know it, CrypMIC Ransomware might cause you serious, irreversible damage. Ransomware is a particularly dreaded type of infection. It’s on the rise right now and we constantly stumble across new parasites of that kind. CrypMIC overall follows the classic ransomware pattern with one difference. This infection doesn’t rename the target files. Most ransomware-type viruses replace the original file extension with a malicious one. You could easily tell which file is encrypted and which one is not. However, CrypMIC doesn’t do that. This pest of a program leaves the data it locks with its original extension. As soon as the virus gets installed, it performs a thorough scan on your computer system. This way it locates all your personal files. As we mentioned, CrypMIC takes down all information you have on board. After encryption is complete, your files are useless. Your computer is unable to read them. Hence, you’re unable to view your very own private data. And that’s not even the worst part. While locking your information, CrypMIC Ransomware also drops payment instructions. It creates README.HTML, README.TXT and README.BMP files. You will find them in all folders that contain locked data. Hackers provide you detailed instructions about both the encryption and the payment. Yes, you’re supposed to pay a certain sum of money in Bitcoins to free your files. How impudent is that? CrypMIC Ransomware’s developers demand 1.2 Bitcoin which equals about 700 USD. What kind of pictures and music costs 700 dollars, though? As you could clearly see, this is a scam. Ransomware’s only goal is to extort money from gullible and panicked PC users. Do not become one of them. Instead of giving your money away, be cautious. Making a deal with cyber criminals would be, to put it mildly, not your brightest idea.
How did I get infected with?
Hackers apply numerous techniques to spread malware online. Ransomware mainly travels the Web in spam messages and spam email-attachments. Despite being the oldest methods out there, those two are still the most effective ones. Watch out for potential parasites every single time you receive a suspicious mail. Some sneaky infection might get sent straight into your inbox. One careless click and you set it free. Are you willing to take that risk? Delete what you don’t trust and be attentive online. The virus might have gotten installed with the help of a Trojan horse, for example. Check out the computer for more infections because CrypMIC may not be the only virus on board. In addition, stay away from illegitimate websites, torrents, executables, etc. Avoid unverified software updates as well; they are equally unreliable. Hackers could be very creative when it comes to spreading infections so watch out. CrypMIC Ransomware is very problematic and harmful. Hence, preventing infiltration is much easier than dealing with the virus later on.
Why is CrypMIC dangerous?
Being typical ransomware, CrypMIC locks your data. It turns all your precious information into unreadable gibberish. This is a complete and utter pest that simply doesn’t belong on board. The sooner you get rid of it, the better. CrypMIC Ransomware also plays mind games with you. It creates a highly aggravating ransom message which you could even find on the PC desktop. As mentioned already, this ransom note is trying to get you to panic. CrypMIC Ransomware uses an asymmetric encrypting algorithm. In order to regain access to your files, you need a decryption key – a unique combination of symbols. Hackers are kind enough to offer you that key but could you trust them? They are the ones who locked your data in the first place. Furthermore, crooks have no reason whatsoever to provide you a decryptor. They are only interested in the illegitimate profit they gain. Remember, you don’t have to participate in hackers’ cyber fraud. What you need to do is ignore the ransom message, keep your Bitcoins and delete the ransomware. You will find our comprehensive removal guide down below.
CrypMIC Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover CrypMIC Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with CrypMIC encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate CrypMIC encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



