Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Reaper Virus. The step by step removal works for every version of Microsoft Windows.
If you suspect that your PC or another Internet-connected device of yours is turned into a part of a botnet, you have a reason to worry. Such illegal networks are never beneficial to the user. On the contrary — they can drain your device’s resources. It is the owner of the botnet that is in control of the infected machines. Such people are criminals. They would use your device for nefarious purposes. Such as sending spam emails and phishing messages, cyber attacks, etc. At the beginning of October 2017, the Chinese security giant Qihoo 360, discovered and started tracking a new IoT Botnet — IoT_Reaper Botnet. The new parasite has borrowed code from the infamous Mirai Botnet. However, unlike Mirai, IoT_Reaper does not carry out attacks. For now, at least. IoT_Reaper, or just Reaper attacks all sorts of Internet gadgets: routers, cameras, digital receivers, etc. The extent of the new attack is shocking. Just in the last two weeks, the Reaper malware has infected over 2 million gadgets. The infection is spreading like wildfire. Reaper is exploiting vulnerabilities in Internet-connected devices made by D-Link, AVTech, Linksys, Netgear, Vacron, GoAhead, and JAWS. However, security experts warn that the list is growing rapidly. The malware is actively developed. Reaper is actively communicating with its creators. It is daily updated. Even though IoT_Reaper Botnet is not carrying out any nefarious attacks yet, it is just a matter of time before this happens. We cannot know what the creators of the infection have in mind. The researchers at Qihoo 360 believe that the attacker is currently focused on the distribution of the virus. Yet, Reaper supports DDoS attacks in the source file. It is advisable that all companies and organizations take immediate measures. Private uses also should not neglect the problem.

How did I get infected with?
IoT_Reaper is distributed by exploiting vulnerabilities in Internet-connected devices. The parasite uses the infected devices to “scan” the Internet for other vulnerable gadgets. Of course, the “closest” devices will be the first victims. If you have an infected router, for example, it is quite likely that the malware will infect your all devices connected to it, such as Wi-Fi printers, cameras, storage boxes, etc. Now, you must be wondering how the first device got infected. There are numerous ways. Peer-to-peer networks should be avoided. Especially with a Botnet on the loose. The torrents are such networks. Torrent networks are extremely dangerous. One infected device is all it takes. In no time, the virus will infect all vulnerable devices in the network. The good old spam emails should not be neglected either. Do not open messages from strangers. Verify the sender’s contacts first. You can do so by entering the questionable address into some search engine. If it was used for shady business, someone might have complained online. The crooks tend to write on behalf of well-known organizations and companies, banks, post offices, police departments, etc. If you receive such a message, go to the company’s official website. Compare the email addresses listed there with the one you have received a message from. If they don’t match, delete the pretender immediately. Other malware distribution techniques include malvertising, corrupted or fake software updates, infected websites and software bundling. A little extra caution can prevent most of these techniques from succeeding. Leave the rest to your trustworthy anti-virus program.
Why is this dangerous?
Currently, IoT_Reaper is only spreading. Its owners haven’t taken any actions yet. However, when they do, anything may happen. Botnets are usually used for spreading spam and phishing emails. However, as IoT_Reaper was designed after the infamous Mirai Botnet, it is quite likely that Reaper will follow its steps. We are talking about distributed denial-of-service (DDoS) attacks. Such attacks make your device’s resources unavailable. Usually, DDoS attacks are aimed at servers, yet, it is not unheard-of personal computers getting attacked. Reaper can use your machine for various nefarious purposes, such as generating web traffic to third party websites, to expose you to fake and misleading advertisements, etc. Once your device gets infected, you are no longer in control. The owners of the botnet are the masters. They can do whatever they please. Do not trust a word you read online while your device is infected! The crooks can manipulate what is being displayed on your screen. You are in a dangerous situation. Your best and only course of action is the immediate removal of the infection. IoT_Reaper is a sophisticated parasite. Use a powerful and trustworthy anti-malware program to remove it.
Manual Reaper Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Reaper infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Reaper infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down Reaper related processes in the computer memory
STEP 2: Locate Reaper startup location
STEP 3: Undo the damage done by the virus
STEP 1: Track down Reaper related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Reaper startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Reaper virus from the windows registry
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
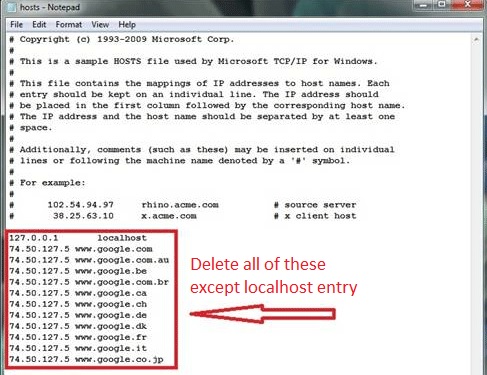
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 3: Undo the possible damage done by Reaper
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Reaper, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Reaper Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.