Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Obamausa7@aol.com Ransomware?
Reader recently start to report the following message being displayed when they boot their computer: “all of your files were protected by a strong encryption with Obamausa7@aol.com ” message.
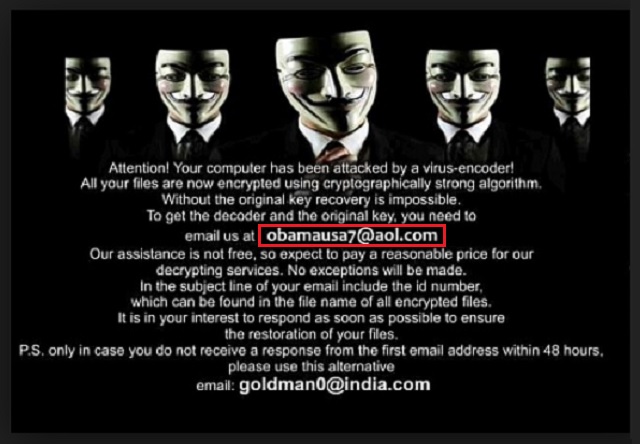
“Attention! Your computer has been attacked by a virus-encoder! All your files are now encrypted using cryptographically strong algorithm. Without the original key recovery is impossible. To get the decoder and the original key, you need to email us at obamausa7@aol.com
Our assistance is not free, so expect to pay a reasonable price for our decrypting services. No exceptions will be made.
In the subject line of your email include the id number, which can be found in the file name of all encrypted files.
It is in your interest to respond as soon as possible to ensure the restoration of your files.
P.S. Only in case you do not receive a response from the first email address withing 48 hours, please use this alternative
email: goldman0@india.com”
One particularly nasty pest currently on the Web is called Obamausa7@aol.com. And, if you were unfortunate enough to stumble across it, you’re in for trouble. This is a classic ransomware infection. It’s virulent, aggressive, resourceful and incredibly unfair. The Obamausa7@aol.com virus doesn’t differ from the classic ransomware pattern so we wouldn’t call its manipulations unexpected. Having said that, there’s no denying the fact they are effective. Ransomware starts causing damage the very minute it gets installed. Therefore, it’s rightfully considered to be the most dangerous type of cyber parasite out there. Or least one of the most dangerous types. Which means you have to take adequate measures as soon as possible. The Obamausa7@aol.com parasite gets installed completely behind your back and wreaks havoc all over your PC. Once it gets activated, it performs a thorough scan on your machine searching for files with specific extensions to encrypt. Then, using a complicated encrypting algorithm, the parasite infects your data. Once this is complete, you can no longer use your files. Consider your pictures, favorite music, your videos, all of your Microsoft documents, presentations, etc. locked and inaccessible. What the virus does is, it adds a malicious Obamausa7@aol.com extension to the target data. You computer can’t recognize this random file format and, logically, the machine can’t read your modified files. That leads us to the upsetting conclusion that you’re unable to use your very own personal information. Unfortunately, this parasite is extremely harmful and malicious. Do you know why it was developed in the first place? For one very simple reason – money. Hackers’ money, to be exact. Ransomware exists in order to scam gullible computer users and, ultimately, to provide easy illegal profit for cyber criminals. That is why this malicious program poses a direct threat to your bank account. Once the parasite has successfully locked your files, it puts some random .txt files on your desktop as well as in every single folder that contains infected files. Those are a lot of folders. The .txt file is actually an aggravating ransom note which you will be seeing practically everywhere. As you probably figured out already, this is yet another part of the ransomware online scam. The one purpose those ransom messages have is to scare you into paying a large sum of money in exchange for some highly questionable decryption key. You’re supposed to receive a unique combination of symbols which allows you to regain access to your locked data. The problem is, you’re most likely to receive nothing. Could you trust hackers? They have absolutely no reason to play by the rules so paying the ransom is not an option. You only have one reasonable thing to do is this situation – uninstall the parasite. Obamausa7@aol.com also installs .exe files on board and disables some programs; it slows down the PC speed considerably and causes an overall mess on your machine. Why would you tolerate this?
How did I get infected with?
There are many plausible explanations why your computer is now compromised. However, one thing is for sure – you didn’t install the virus voluntarily. Ransomware is notoriously sneaky so it managed to bypass your security. Sometimes a single moment of negligence online is enough to infect your machine with a bunch of parasites; therefore, you always have to keep an eye our for potential viruses. Don’t hesitate to deselect any piece of software you don’t trust and pay attention to the program you give green light to. Ransomware-type infections usually travel the Web via spam email-attachments and spam messages from unknown/known senders. That means avoiding those is a must if you want to protect your PC from malware in the future. Also, stay away from suspicious executable files and questionable websites. Keep in mind that it’s much easier to prevent virus infiltration than it is to uninstall a malicious parasite later on. Caution pays off in the long run; make sure you remember that and make sure you remember it well.
Why is Obamausa7@aol.com dangerous?
Obamausa7@aol.com and its harmful file extensions are definitely not a pleasant sign on any machine. Especially yours. The virus not only effectively demolishes your Internet experience but also denies you access to your own personal files. How dishonest is that? Furthermore, hackers attempt to blackmail you by relying on your panic and anxiety. No matter how nervous those sudden modifications have made you feel, keep in mind that this whole thing is a scam. Ransomware is deceptive so you cannot afford to believe absolutely ANYTHING you see on your PC screen. Paying the money demanded will not guarantee you any decryption key and it will not make your situation better. On the other hand, it might drastically worsen it. Following crooks’ instructions will only put you in a much more vulnerable position than your current one – with your computer still compromised, your files still encrypted and unreadable, and your money gone. We assume that doesn’t really sound like a good scenario. Therefore, don’t become a sponsor of hackers and don’t allow them to make money at your expense. Instead, get rid of their parasite. To remove Obamausa7@aol.com manually, please follow the detailed removal guide that you will find down below.
Obamausa7@aol.com Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Obamausa7@aol.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Obamausa7@aol.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Obamausa7@aol.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



