Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CTBL file extension Ransomware?
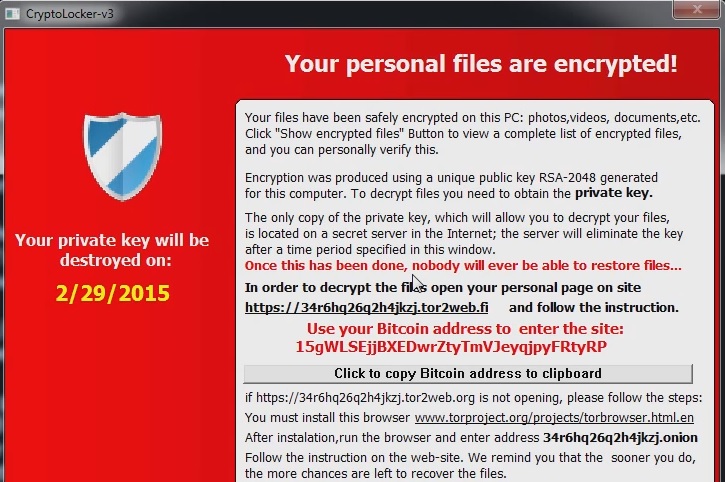
If you come across CTBL, know that a cyber infection has invaded your system. And, not just any infection, but arguably the worst one you can catch. CTBL is linked to a ransomware tool. And, in case you don’t know, ransomware is quite the disastrous application. After it slithers into your system, it proceeds to mess everything up and expose you to various threats. The pesky program encrypts every single file you have stored on your PC and demands you pay ransom if you wish to reclaim it. Make no mistake! The tool doesn’t steal your data in the sense of relocating it somewhere to an unknown location. Oh, no. The files are right where you left them. You just cannot access them in any way. You can see them, but cannot open them. They seem the same apart from one detail. Suddenly, you’ll find each file was renamed, and now has an added CTBL extension. For example, if you had a video, named ‘awesome,’ you’ll see it as ‘awesome.CTBL.’ The malicious ransomware encrypts everything and leaves nothing untouched. All of your data – videos, pictures, music, documents, etc., are now under its control. Nothing is safe. Nothing is beyond its grasp. When it’s finished with the encryption process, it reveals its demands. The infection asks you to pay up if you wish to get them back. Supposedly, it should go down like this: you pay, you receive a decryption key, apply it, take back your files, and all is fine and dandy. But life is rarely that simple. Whatever the pesky program wants from you, don’t go through with it! Don’t comply with its demands for you WILL regret it! If you do, you’ll only dig yourself further into the abyss of hazards, and cause further damages. Avoid that! Cut your losses, and forsake your files. Yes, it may seem harsh, but it’s the best course of action you can take. You cannot win a fight with a ransomware tool. Accept it early on, and move on. Data is replaceable.
How did I get infected with?
Ransomware doesn’t just show up on your PC out of the blue. For it to slither into your system, you have to permit its installation first. If you don’t consent to install it, it cannot enter. It’s as simple as that. So, with that in mind, you are the main reason for your current predicament. Because, at some point, the tool asked whether you agree to install it or not, and you, evidently, gave an affirmative response. Otherwise, your files and privacy wouldn’t be in jeopardy right now. But how do you suppose you permitted the install of such a hazardous tool, and not even realize it? Well, ransomware tools are notoriously sneaky. They resort to all kinds of trickery and deceit to dupe you into allowing them in while keeping you oblivious to it. Some of the most commonly used means of invasion include hiding behind spam email attachments, freeware, corrupted links, or sites. The nasty application can also pretend to be a bogus update, like Java or Adobe Flash Player. If you wish to prevent ransomware from slithering its way into your computer, try to be more careful. Don’t throw caution to the wind, and don’t give into distraction and gullibility. Be extra vigilant, and always do your due diligence. Even a little extra attention can go a long way, and save you a ton of troubles.
Why is this dangerous?
After your PC has fallen victim to the ransomware infection, affiliated with CTBL, you’re in for a pretty bad time. Everything you have on your computer – every picture, document, video, etc., will no longer be accessible. The infection will encrypt it by adding the CTBL extension at the end of it. And, even if you try to rename it, and delete the extension, it won’t work. The files will still be encrypted. The only way to get them back, and be able to open them, is to receive and apply the decryption key. That’s the ransomware’s game plan. ‘Kidnap’ your data, demand ransom, and promise a decryption key if you comply. But can its promises be trusted? The answer is ‘No.’ It’s a nasty, hazardous, harmful infection, which only seeks to exploit you for gains with no interest in your well-being. Do NOT place your faith in the ransomware for you will come to regret that decision. To pay up is ill-advised, to say the least. There are plenty of ways, the ‘exchange’ can go wrong, and every one of them ends with you, full of regrets. You need to understand that there are no guarantees when it comes to the ‘kidnappers’ and them keeping their promises. Imagine the following situation. You go through with their requirements, and they give you the decryption key you need to release the files. So far, so good, right? Well, what if it doesn’t work? What if your files remain encrypted? You not only still have no access to your data, but you also allowed malicious strangers into your private life. You gave these people access to your personal and financial information since you chose to pay their ransom. Do you think that will end well for you? Hardly. Don’t be impulsive and give into their scare tactics. Don’t panic and fold. Make the wiser choice, and choose you! As was already stated, files can be replaced. Your privacy cannot.
CTBL file extension Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
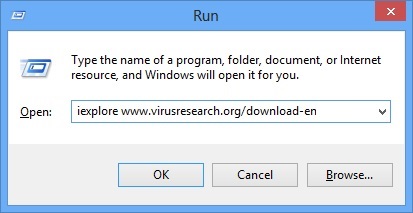
- A dialog box should open. Type iexplore www.virusresearch.org/download-en
- Internet Explorer will open and a professional scanner will prompt to be downloaded
- Run the installer
- Follow the instruction and use the professional malware removal tool to detect the files of the virus.
- After performing a full scan you will be asked to register the software. You can do that or perform a manual removal.
Remove CTBL file extension malware Manually
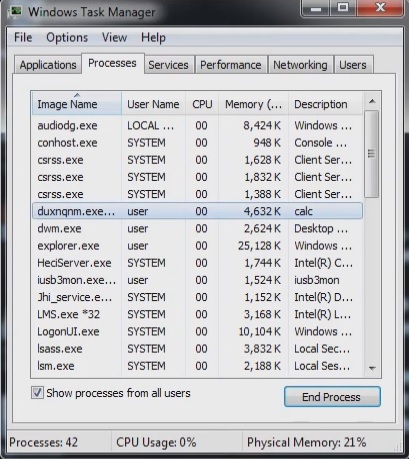
Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
Locate the process of the Ransomware. Have in mind that this is usually a random generated file.
Before you kill the process, type the name on a text document for later reference.
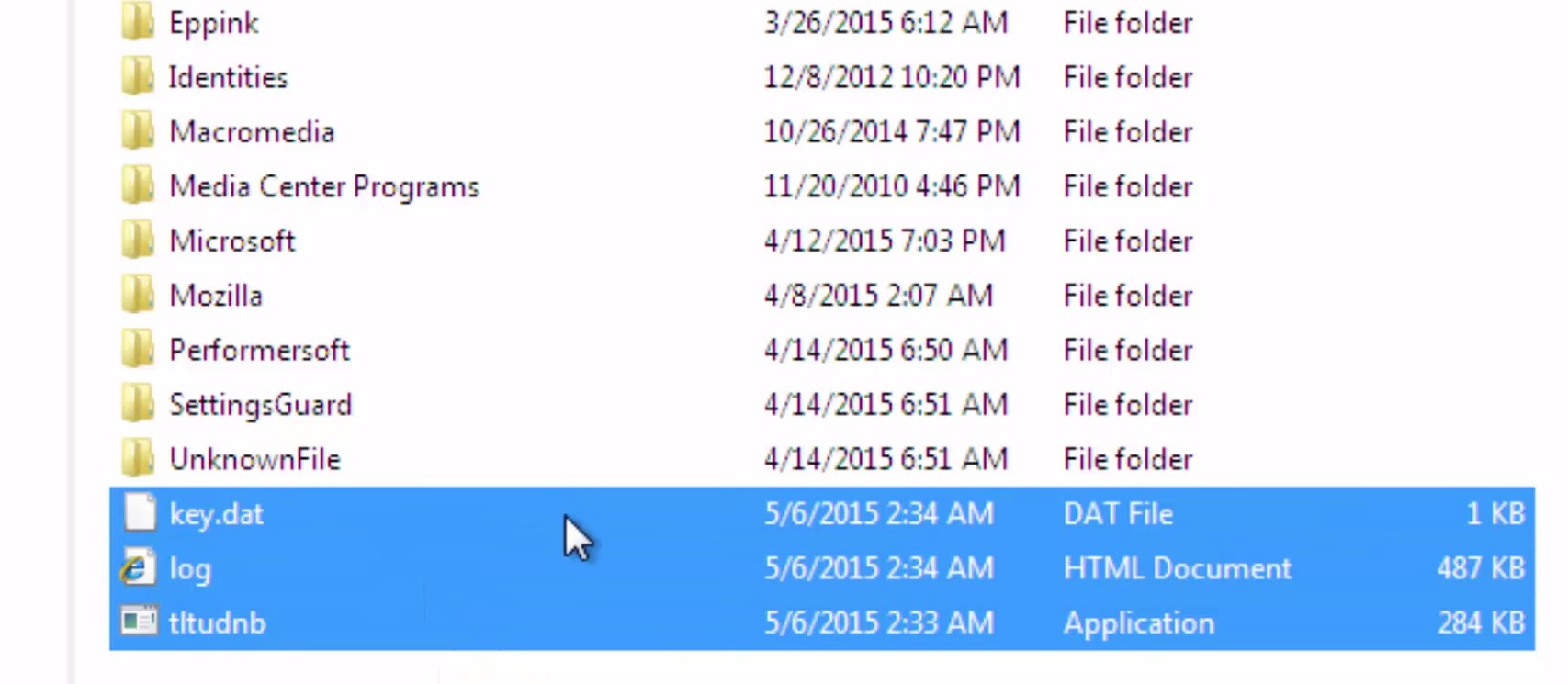
Navigate to your %appdata%/roaming folder and delete the executable.
Open your Windows Registry Editor and navigate to
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\
and
HKLM\Software\Microsoft\Windows\CurrentVersion\Run\
delete the name crypto13
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you run the professional scanner to identify the files.
How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.
- Method 2: File Recovery Software – When TeslaCrypt and Alpha Crypt encrypt a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you can use file recovery software to try recovering some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies.
It is always a good idea to use a reputable anti-malware program after manual removal, to prevent this from happening again.