Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Admin@stex777.com Ransomware?
There’s a new ransomware, plaguing users. It goes by the name Admin@stex777.com, because that’s the contact, you’re given. Let’s elaborate on your predicament. The Admin@stex777.com infection uses trickery to invade your system. Then, it uses encryption algorithms to lock your data. It encrypts every single file, you have on your PC. And, proceeds to demand a ransom for their release. Supposedly, if you pay up, you’ll get the means, needed for the files’ release. The ransomware makes that quite clear in the ransom note it leaves for you. It’s usually a README.txt file. And, you can find it on your Desktop, as well as in each folder that contains locked data. It’s pretty standard. It explains your situation, and offers you a way out of it. That way, being compliance. The cyber kidnappers promise that if you follow their demands, you’ll regain control over your files. Don’t fall for their web of lies. They’re feeding you falsehoods, and hope you’re naive enough to believe them. These are cyber criminals, you’re dealing with. They prey on your fear and naivety, and hope to profit off of them. Don’t let yourself turn into a paycheck for atrocious extortionists. Don’t comply! Don’t waste your time, energy and money. Don’t deal with the people, behind the Admin@stex777.com threat.
How did I get infected with?
Tools, like the Admin@stex777.com one, are sneaky. They resort to all manner of trickery, when it comes to invasion. More often than not, the usual suspects come into play. The tool lurks behind corrupted links, sites or torrents. Or, uses spam emails as a way in. It can also pretend to be a bogus system or program update. Like, Adobe Flash Player or Java. And, of course, the ransomware can turn to freeware. It offers, arguably, the easiest entry point. That’s because, most users are pretty careless during freeware installs. They don’t do any due diligence, but leave their fate to chance. Instead of reading terms and conditions, they rely on luck. And, they agree to everything, in blind faith. That’s a mistake! That’s how you end up with atrocious infections, like the Admin@stex777.com one. Don’t discard the importance of vigilance. If infections prey on your carelessness, make sure not to provide. Instead, be extra careful and always take the time to be thorough. Even a little extra attention van save you a ton of issues. Don’t forget that.
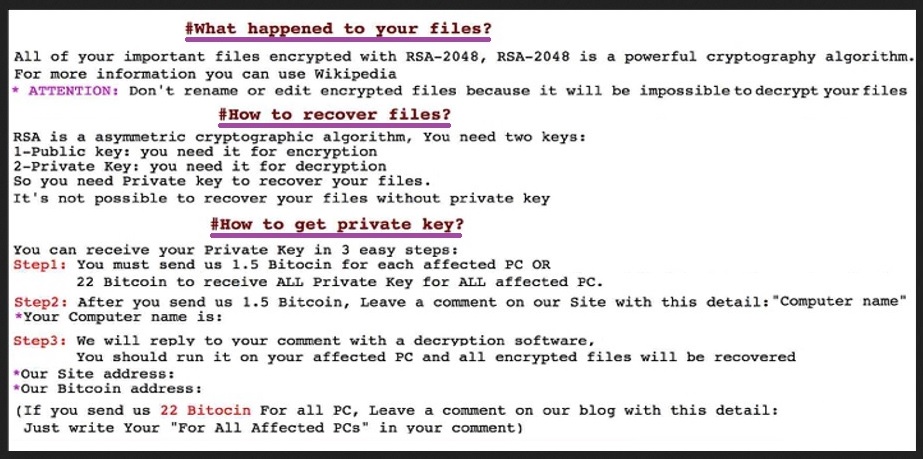
Why is Admin@stex777.com dangerous?
The Admin@stex777.com menace uses RSA-2048 cryptography algorithm to lock your files. Documents, archives, pictures, videos, music. All, that you have on your PC, falls victim to the cyber threat. It adds a special extension at the end of each one, to solidify its grip. Once the extension is in place, that’s it. You can no longer access them. You can try to rename or move them, but it’s pointless. The only way to remove the encryption, and escape the ransomware’s clutches, is to pay. Once you pay, you receive a unique decryption key. Apply it, and you free your files of the infection’s influences. But does that happen, or are these, nothing more than pretty words that fall short? Well, remember that you’re dealing with cyber criminals. Strangers with malicious intentions. People, who wish nothing more than to exploit you from monetary gain. Don’t let them succeed. The requested ransom amount is 1.5 Bitcoins. Do you know how much money that is? Currently, 1.5 Bitcoins equal a little over 12 400 US Dollars. That’s no small amount. But even if you could look past the large sum, payment is still not advised. Understand that you have only the promise of the extortionists to go on. They give you no guarantees that, once you pay, you’ll get the key. You’re left to hang on their word. And, you can’t trust the word of data kidnappers, who extort you for money. They can get your money, but send you nothing. Or, send a key that doesn’t work. They have plenty of ways to double-cross you. Pay them nothing. Don’t contact them. Don’t reach out to them. It’s a tough call to make, but it’s the right one.
Admin@stex777.com Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Admin@stex777.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Admin@stex777.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Admin@stex777.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


