Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zixer2 Ransomware?
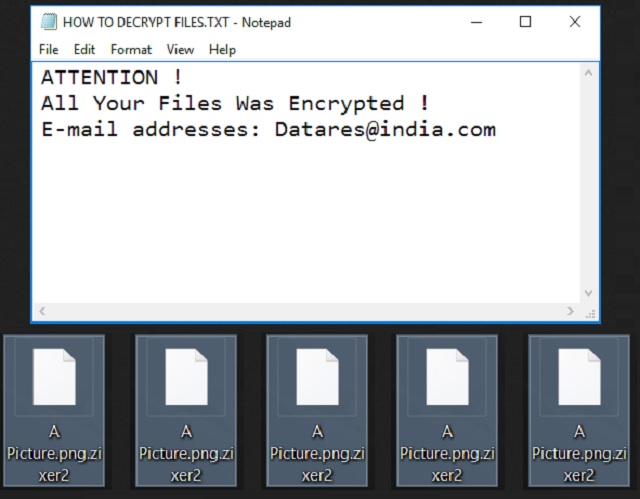
Readers recently started to report the following message being displayed when they boot their computer:
ATTENTION !
All Your Files Was Encrypted !
E-mail addresses: Datares@india.com
Zixer2 seems to be an improved variant of the Xorist Ransomware. In other words, you’re stuck with a particularly worrisome infection. Nobody wants to be dealing with ransomware and its malicious glory is well-deserved. Unfortunately, these programs are currently a complete plague on the Web. We practically come across brand new ransomware viruses every day. Now that you see for yourself just how dangerous Zixer2 is, be careful in the future. Make sure you never again have to tackle such a pest. The parasite’s trickery begins immediately after installation. Unlike most ransomware-type programs, this one uses a TEA cipher. TEA (Tiny Encryption Algorithm) is famous for being rather easy to operate with. This block cipher successfully locks your private files. After all, this is what ransomware is aiming at. There is a reason why file-encrypting infections are on the rise right now. Every hacker’s dream is to gain effortless profit online. By blackmailing gullible PC users, ransomware allows crooks to make money. The parasite’s scheme is actually very simple. Once Zixer2 lands on board, it performs a thorough scan of your computer system. Eventually, the ransomware locates all your files. We’re talking a huge variety of formats including some of the most popular ones. Zixer2 encrypts pictures, music, videos, documents, presentations. It targets every single bit of information stored on your device. Chances are, you keep some extremely important files on board. That is why we’d recommend having backups of your precious data. You have to think in advance in order to protect yourself. Zixer2 uses the 128-bit algorithm and the 64-bit data block schedule. When the encrypting process is complete, you will notice a brand new appendix added to your files. As the name of the virus implies, this program adds the .Zixer2 file extension. It also creates detailed payment instructions. At the end of the day, ransomware’s goal is to steal your money. If you trust the parasite’s ransom notes, hackers will succeed. Note that Zixer2 is now on board to trick you into buying a decryption key. The ransomware drops messages in all folders that contain locked files. It even modifies your desktop wallpaper. To sum up, hackers force their ransom notes on you about as much as possible. This is all part of the scam so don’t give into your anxiety. Panicking could cost you money.
How did I get infected with?
Malicious torrents, fake program updates, third-party ads, illegitimate websites… The list of infiltration methods is very impressive. That makes it almost impossible to determine what method Zixer2 used. However, there are a couple of particularly popular techniques. Hackers’ favorites, if you will. Number one tactic when it comes to ransomware are spam emails and messages. Have you recently received something questionable in your inbox? Hackers could send malware directly and disguise it as perfectly safe emails. You should know better than to click open such messages or email-attachments, though. Delete what you don’t find reliable. This could save you a headache. Ransomware might also get attached to some freeware or shareware bundle. In this case, you download the virus along with the safe programs in the bundle. To protect your PC (which, as you can see, is a must), take your time. Opt for the Custom or Advanced option in the Setup Wizard instead of the Basic one. Check out all programs one by one and don’t overlook any potential threat. It is your responsibility to prevent virus infiltration. Make sure you outwit hackers every time they attempt to cause you harm.
Why is Zixer2 dangerous?
Zixer2 renames your data. As mentioned, it works with all your files and inevitably creates a mess on your computer. This virus adds the .Zixer2 extension and turns your files into unreadable gibberish. You’re no longer able to open or view any of your own files on your own device. Furthermore, you’re supposed to PAY in order to receive a decryptor and free your data. Crooks provide you the datares@india.com email address. Don’t even consider contacting hackers, though. There’s nothing to gain out of such negotiations and you know it. You might significantly worsen your situation. Paying the ransom doesn’t guarantee you that hackers will keep their end of the bargain. More often than not, crooks focus on stealing the victim’s Bitcoins. Ransomware is trying to scam you so ignore its empty promises and bogus threats. To delete the virus manually, please follow our removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Zixer2 Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Zixer2 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zixer2 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zixer2 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



