Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Sage 2.2 Ransomware?
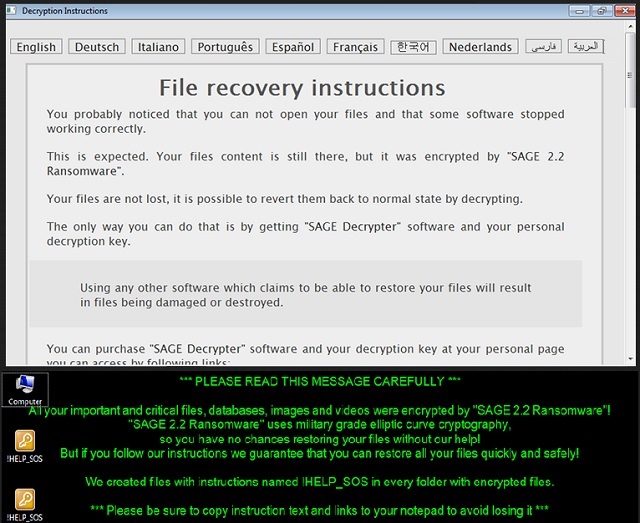
Readers recently started to report the following message being displayed when they boot their computer:
*** PLEASE READ THIS MESSAGE CAREFULLY ***
All your important and critical files, databases, images and videos were encrypted by “SAGE 2.2 Ransomware”!
“SAGE 2.2 Ransomware” uses military grade elliptic curve cryptography,
so you have no chances restoring your files without our help!
But if you follow our instructions we guarantee that you can restore all your files quickly and safely!
…
The Sage 2.2 virus is part of the ransomware family. It’s a dreaded infection that brings nothing but grievances and headaches your way. Ransomware programs are among the worst cyber threats out there. That’s because their attack is personal. The infection targets your files, everything you keep on your computer. Pictures, documents, videos, music, all of it. It uses an encryption algorithm to lock your data. And, places only one option before you. Pay a ransom to regain control over your files. Or, don’t pay and lose everything. The ultimatum may seem like quite the conundrum, but it’s not. Here’s the solution. Do NOT pay! Do NOT comply with the demands of cyber criminals! If you follow their instructions, you only bury yourself into a bigger mess. Cut your losses! Compliance means you’re risking your private life. And, it’s better to lose your files than your privacy. Don’t place your privacy on the line by complying. Heed experts’ advice, and do NOT pay the ransom. Say goodbye to your data, so that you may keep your private life private. It’s the better alternative.
How did I get infected with?
Ransomware does not pop up on your PC one day. Not unless you invite it in. In fact, you don’t only open the door for the tool. You also hold it open, and watch it as it parades through. You look straight at it, but not see it. That same scenario occurred with the Sage 2.2 tool. Odds are, it slipped by you only because you weren’t careful enough to catch it in the act. Infections prey on carelessness. And, ransomware are no exception. They use every sly maneuver there is to slither their way into your system. The most common methods include spam email attachments and freeware. They can also pretend to be fake system or program updates. Say, you’re led to believe, you’re installing a Java update. If you don’t do your due diligence, you won’t realize that, in reality, you’re not. But you are, in fact, installing a dreaded cyber menace. Always be thorough when allowing tools or updates into your system. Check the fine print, and read the terms and conditions. Attention goes a long way, and it can save you countless headaches. As sly and deceitful as ransomware tools can be, they cannot succeed without your carelessness. So, don’t grant it. Don’t rush or give into gullibility. Don’t make it easy for a hazardous program to invade your system. Due diligence is a far better companion than distraction. One prevents tools like Sage 2.2 from sneaking in. The other opens up your system to them.
Why is Sage 2.2 dangerous?
The Sage 2.2 tool is a more aggressive version of the Cerber ransomware. But it isn’t particularly original when it comes to encryption tactics. The tool follows the usual programming. Once it gains access to your system, it takes over, and locks your files. It then displays its ransom note that comes either in an HTML or TXT file. Sometimes, both. And, the demands are pretty standard, as well. Pay a ransom in Bitcoin, and when you do, you’ll receive a decryption key. Apply said key, and you’ll free your files from the clutches of Sage 2.2. It all seems rather straightforward, doesn’t it? Well, it’s not. There are so many ways the exchange can go wrong. You can get swindled out of thousands of dollars, and still have no key. Or, you can receive one, but it’s the wrong one and it does nothing. And, what’s your best-case scenario? You get the right one and it works. But then what? By transferring the sum of money to these people, you give them access to private information. Your personal and financial details will fall in their hands. Do you think that ends well for you? Don’t kid yourself. Don’t wait for extortionists to keep their end of the bargain. They won’t. And, even if they do, you still lose. It’s a game, you can’t win as the odds are stacked against you. So, do yourself a favor. Don’t play at all. You’re NOT dealing with people, who you can trust to keep their word. Pick the lesser evil, and forsake your files for the sake of your privacy. It’s much more precious.
Sage 2.2 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Sage 2.2 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Sage 2.2 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Sage 2.2 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



