Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Xdata Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
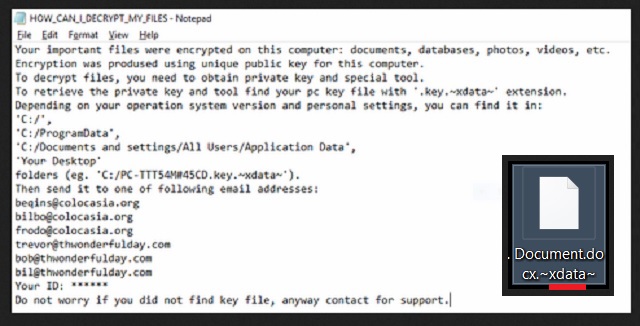
Your important files were encrypted on this computer: documents, databases, photos, videos, etc.
Encryption was prodused using unique public key for this computer.
To decrypt files, you need to obtain private key and special tool.
To retrieve the private key and tool find your pc key file with ‘.key.~xdata~’ extension.
Depending on your operation system version and personal settings, you can find it in:
‘C:/’,
‘C:/ProgramData’,
‘C:/Documents and settings/All Users/Application Data’,
‘Your Desktop’
folders (eg. ‘C:/PC-TTT54M#45CD.key.~xdata~’).
Then send it to one of following email addresses:
beqins@colocasia.org
bilbo@colocasia.org
frodo@colocasia.org
trevor@thwonderfulday.com
bob@thwonderfulday.com
bil@thwonderfulday.com
Your ID: ******
Do not worry if you did not find key file, anyway contact for support.
Xdata is yet another ransomware. This parasite, in particular, targets PC users in Ukraine mostly. Yet, Xdata infections have been detected in other countries as well. No one is safe. The hackers behind this virus have no scruples. They programmed Xdata to use both RSA and AES cryptic algorithms. To lock your files, the virus will use an asymmetric cryptography. Hence, the virus generates public and private keys. It will also add the “.~xdata~” extension at the end of all encrypted files. You will be able to see your pictures, documents, and archives, but you wouldn’t be able to open or use them. An RSA cipher is used to secure the only decryption key. It is also stored on a remote server. To obtain their private key and a decryption tool, the victims are supposed to contact the hackers via one of the following email addresses: bilbo@colocasia.org, begins@colocasia.org, frodo@colocasia.org, bil@thwonderfulday.com, trevor@thwonderfulday.com or bob@thwonderfulday.com. The hackers are supposed to send you further instructions. We recommend against such actions. Don’t forget that you are dealing with criminals. Those people cannot be trusted. They will double-cross you for sure. They will blackmail you. All they want is money. No one can guarantee you that they will keep their promises. The crooks usually demand between $200 and $2000 in Bitcoin. In most cases, once the ransom is paid, the hackers ignore the victims. You cannot receive a refund if this event occurs. Authorities can’t help you either. Xdata is reported to use over twenty IP addresses to hide its tracks. The Bitcoin currency is also untraceable. This ransomware is highly dangerous. You should not underestimate it. Your files are already locked. There are no decryption tools yet. Take a moment to consider the situation. Fear is a powerful weapon. Don’t fall victim of it. Make up your mind and act!
How did I get infected with?
To enter your computer, Xdata used trickery. The scammers tend to write emails on behalf of well-known organizations. The scheme is simple. They would attach the malicious virus as a file. Once you download it, hell will rise. It is hard to distinguish the spam from the legit mail. Therefore, before even opening a letter from a stranger, check the sender’s contacts. It is not that hard. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone might have complained. Yet, new email addresses are created all the time. If you are part of the first wave of spam emails, there will be no evidence online. Therefore, double-check the sender. Let’s say that you have received a message from an organization. Go to their official website. You can find their authorized email addresses there. Compare them with the one you have received an email from. You know what to do if they don’t match. Delete the spam email immediately. Remember that institutions and the trustworthy companies will use your real name. Thus, when you receive a letter starting with “Dear Customer” or “Dear Friend”, proceed with caution. Be always vigilant! To spread their virus, the hackers behind Xdata must have more than one distribution methods. The most common virus distribution techniques involve torrents, corrupted links, and fake software updates. Only your caution can prevent infections. Download your software from legitimate websites only. And don’t forget to keep your anti-virus program up to date.
Why is Xdata dangerous?
Xdata is highly dangerous ransomware infection. It should never be underestimated. The hackers behind it demand a hefty ransom for your own files. Yet, there is no power in this world that can guarantee you that those criminals will keep their part of the deal. Be reasonable. Paying the ransom may not deliver positive results. You will lose your money. Even if the crooks send you a key with the decryption tool, what will you do if they don’t work? Furthermore, removing the lock will not delete the virus. There are many cases when the victims paid and restored their files, just to have them re-encrypted hours later. How many times are you willing to pay? Whatever you do, get rid of the virus firs. Use a trustworthy anti-malware program. One more thing. When you use your PC to pay the ransom, the virus may record your paying details. The hackers can use them to steal even more money from you. It is not worth the risk. Discard your data. Clean your computer and start backing up your system regularly. This way you will be prepared if a ransomware strikes again.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Xdata Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Xdata Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Xdata encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Xdata encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



