Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Win.exploit.cve_2016_3316-1 just keeps popping up and you cannot remove it?
Win.exploit.cve_2016_3316-1 is a Trojan. And, Trojans are a menace. They jeopardize your privacy and threaten your system’s well-being. They throw you into a whirlpool of disasters. So, it should come as no surprise that experts advise towards their immediate removal. As soon as you realize you’re dealing with a Trojan, act! Locate where on your computer it’s lurking. And, when you find it – delete it! Don’t delay The longer you allow it to stay, the worse your situation will get. That’s because every chance you grant the cyber threat to wreak havoc, it WILL take! It will take advantage of the time and opportunities you give it, and it WILL make a mess. It can open your computer to more unwanted threats. Like, ransomware, hijackers, adware, anything. You name it. The Trojan can release it upon your PC like a plague if it so chooses. Imagine turning on your PC, and finding it overrun with malware. It’ll hardly be a pleasant experience. And, it might even lead to The Blue Screen of Death. Yes, if your system gets too overwhelmed with cyber infections, it can simply give up. And, then you’ll see the dreaded blue. Granted, it’s a minuscule possibility that this may occur. But ‘minuscule’ does not equal ‘non-existent.’ So, don’t discard the threat! Also, take into account that it’s not the only one you’ll face. And, then deleting the Trojan immediately should be an easy decision to make. It won’t even be the worst problem, which Win.exploit.cve_2016_3316-1 will force upon you. Make the wiser choice. Delete the infection the first chance you get. You’ll save yourself a ton of troubles, and your future self will thank you for it.

How did I get infected with?
The infection didn’t just pop up on your computer one day. Most cyber threats (if not all) cannot install themselves on your PC unless you permit them to do so. Yes, you have to agree to their installation. In fact, malware of its kind has to ask whether you agree to allow them access to your system. And, if you deny them – no entry. It’s as simple as that. But, looking at the mess you’re stuck in right now, you must have complied. If you hadn’t, you wouldn’t be in your current predicament. And, odds are, you don’t even remember giving the Trojan the green light. That’s because it didn’t pop up and ask for your consent. Oh, yes. It may be bound to seek permission, but it doesn’t have to do it openly. Instead, it turns to trickery and deceit. It duped you. Through slyness and subtlety, it fooled you into agreeing to install it. Infections like it, usually succeed in their deception with the help of the old but gold means of infiltration. More often than not, by pretending to be an update. For example, you may be convinced you’re updating your Java or Adobe Flash Player, but you’d be wrong. In actuality, you’ll be installing a concealed Trojan. If you wish to avoid such, let’s call them ‘mishaps,’ be more cautious! Don’t give into distraction, naivety, and haste. Be more vigilant and thorough, and do your due diligence. Remember that even a little extra attention goes a long, long way.
Why is this dangerous?
Win.exploit.cve_2016_3316-1 is a dreaded infection that overwhelms you with troubles. It begins to bombard you with issues and grievances from the moment it enters your PC. And, doesn’t cease its bombardment until you delete it. So, from beginning to end, you’ll suffer from intrusions. The Trojan will meddle constantly. It will redirect you to unreliable websites. It will shower you with pop-up advertisements. Imagine. Every time you surf the web, the infection will interrupt you with redirects and ads. And, don’t think that goes unnoticed. The never-ending disruptions cause your system to crash frequently. Also, your computer’s performance slows down to a crawl. And, when you add the malware threat to these issues, the decision to delete the Trojan is pretty much made for you. But if you’re still unsure of the infection’s harmfulness, there’s one more severe issue we’re yet to mention. And, that’s the security threat. Consider the fact that Trojans, like the one on your PC, jeopardize your privacy. They’re designed to spy on you. As soon as they invade your system, they start to keep track of your online activities. They catalog every move you make while browsing. Once they deem they have gathered enough data, they send it to the third parties behind them. Win.exploit.cve_2016_3316-1 is no exception. If you let it, it WILL steal your private information, and it WILL hand it off to these people. Are you prepared to trust strangers with your personal and financial details? Think long and hard before you answer as both your and your system’s future rest on your response.
Manual Win.exploit.cve_2016_3316-1 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
WARNING! Stopping the wrong file or deleting the wrong registry key may damage your system irreversibly.
If you are feeling not technical enough you may use Spyhunter Professional Removal Tool. However, only the Scanner is FREE, in order to remove the VIRUS completely you need to purchase full version. >>Download SpyHunter – a professional Exploit scanner and remover.
>>Download SpyHunter – a professional Exploit scanner and remover.
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the virus.
- Before you kill the process, type the name on a text document for later reference and to be able to delete it.

- Locate any suspicious processes associated with the exploit Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\[random] “%AppData%\[random].exe” HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\[random] “%AppData%\{2ED2A2FE-872C-D4A0-17AC-E301404F1CBA}\[random].exe”
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the malicious executable.
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
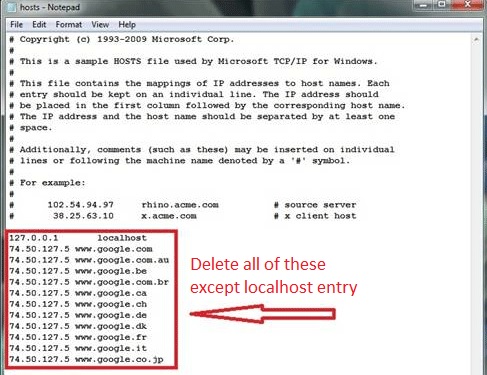
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files. Keep Your software always Up to date!


