Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
550 This Message Contains Malware just keeps popping up and you cannot remove it?
550 This Message Contains Malware – the minute you notice this pop-up, know you’re in trouble. It’s a crystal clear indication for malware. Yes, something went very wrong with your safety not a long time ago. And, unfortunately, the source of your trouble is a Trojan horse. Let us tell you a couple of things about Trojans. These programs are among the most problematic infections currently on the Web. You see, you’re dealing with quite a pest over here. As you could imagine, the sooner you take measures, the better. This virus must be deleted before it unleashes its entire malicious potential. We’ve seen enough examples of what a Trojan can do once it gets out of hand. Don’t let this parasite cause you damage. Now, the reason you’re seeing 550 This Message Contains Malware is very simple. It’s also aggravating. Your machine has been compromised with win.exploit.cve_2016_3316-1. As already mentioned, this is a Trojan. It’s a relatively new infection. And it’s just as harmful and problematic as all other Trojans out there. You see, this program must be deleted as quickly as possible. The more time it spends on board, the more havoc it wreaks. Troajns are generally quite secretive and sneaky. That means they’re able to remain unnoticed for a while. If you spot 550 This Message Contains Malware pop-ups, don’t hesitate. You’re dealing with a particularly dangerous PC virus. Its shenanigans starts as soon as the parasite gets installed. First of all, this pest messes with your default PC settings. Again, all these modifications happen completely behind your back. The Trojan changes your system registry and might even damage important system files. Logically, some programs won’t run. Furthermore, the virus could modify your browser settings and hijack your browsers. Of course, that is just the beginning of a long, long list of malicious traits. This pest jeopardizes your privacy. Since the minute it gets downloaded, It begins to spy on your personal data. Passwords and usernames and IP addresses and browsing history. What’s even worse is that your personally identifiable data is unsafe too. The Trojan aims at your bank account, online credentials and other sensitive information. You wouldn’t feel good knowing hackers have access to this data, would you? Crooks have various monetizing platforms online to choose from. They will probably sell your data for marketing purposes to third parties. However, your private data may easily end up in the wrong hands. Before you know it, you might fall victim to various financial frauds. In the worst case scenario, the Trojan will lead to identity theft.

How did I get infected with?
No, you didn’t download the Trojan voluntarily. Not a lot of people compromise their own computers. Thus, the virus has sneaked in without your active cooperation. It tricked you. For instance, Trojans travel the Web via spam emails. All you need to do is click some corrupted message you came across in your inbox. That’s it. The parasite gets activated immediately and starts harassing you. Our advise is to avoid anything suspicious-looking. Preventing installation is much easier than having to remove a parasite. Make no mistake. Other virus distribution methods are corrupted ads and software bundles. In addition, the parasite might have gotten installed as a fake program update. There are so many opportunities for hackers to cause you harm. It’s your responsibility and yours only to outwit them. Next time you surf the Web, keep an eye out for potential infections. You might accidentally infect your PC just by being careless. Hence, don’t be gullible to think hackers cannot get to you. They can and, if you allow it, they will.
Why is this dangerous?
Trojans are extremely stealthy. Apart from the fact they get installed in silence, they also wreak havoc in silence. This program’s rich bouquet of tricks could cause you serious, irreversible damage. The virus makes several unauthorized system changes. It might even lead to data loss or other similar issues. Your machine underperfoms due to high usage of CPU memory. The PC now crashes and freezes on a daily basis. The Internet connection is unstable as well. As if that wasn’t enough, you might often see The Blue Screen of Death. To top it all, the Trojan could grant its developers remote control over your PC. As we mentioned, your browsers might get modified too. That means you get redirected, bombarded with pop-ups, irritated and exposed to malware. It’s quite obvious how devastating this whole thing is for your safety, right? Your machine is now stuck with an extremely pesky infection. Do the right thing and don’t procrastinate. To delete the virus manually, please follow our detailed removal guide down below.
Manual 550 This Message Contains Malware Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 2: Windows 7/XP/Vista Removal
STEP 1: Start Your Computer into Safe Mode with Networking in Windows 8
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Move the mouse to the upper right corner until the windows 8 charm menu appears
- Click on the magnifying glass
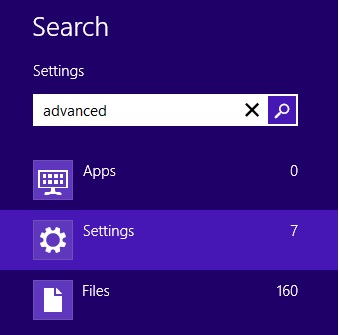
- select Settings
- in the search box type Advanced
- On the left the following should appear
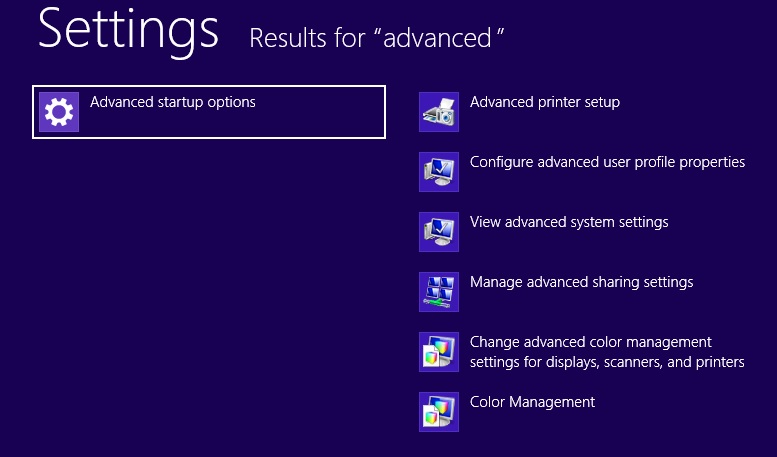
- Click on Advanced Startup Options
- Scroll down a little bit and click on Restart Now
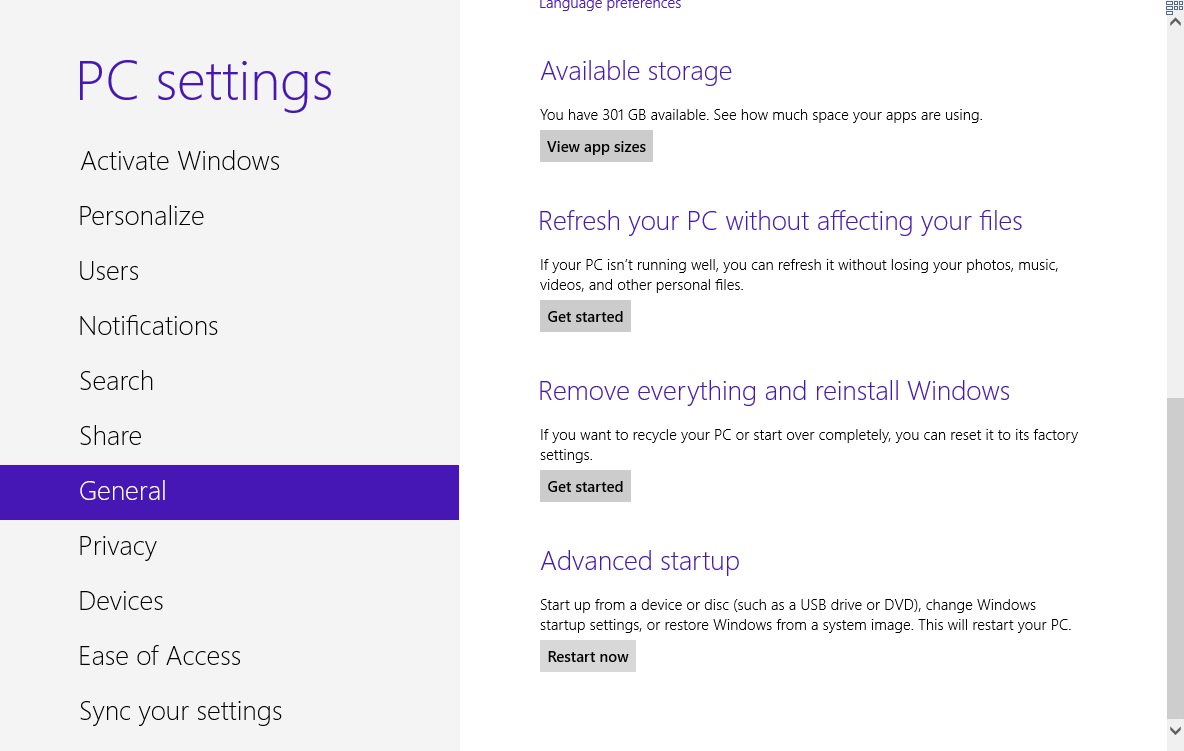
- Click on Troubleshoot
- Then Advanced options

- Then Startup settings

- Then Restart
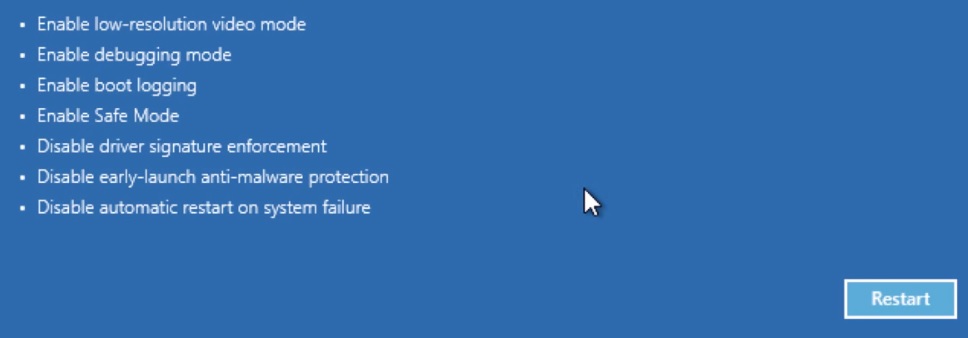
- When you see this screen press F5 – Enable Safe Mode with Networking

STEP 2: Start Your Computer into Safe Mode with Networking in Windows 7/XP/Vista
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.

STEP 3: Locate the startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: backgroundcontainer

- Then open your explorer and navigate to:
%LocalAppData%\uqgtmedia
where %LocalAppData% refers to:
C:\Users\{username}\AppData\Local
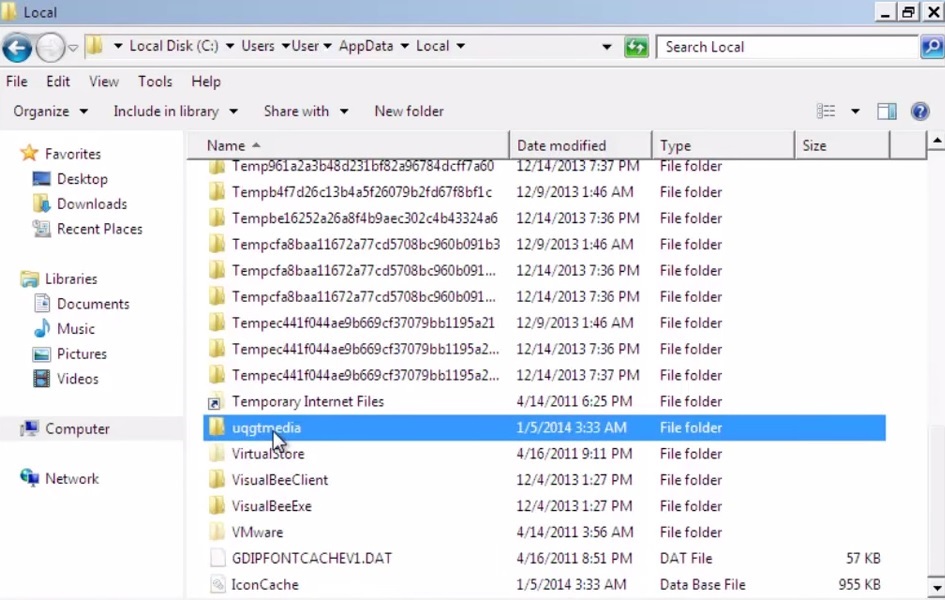
- delete the whole folder
Double check with any antimalware program for any leftovers. Keep your software up-to date.



