Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wana Decryptor Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
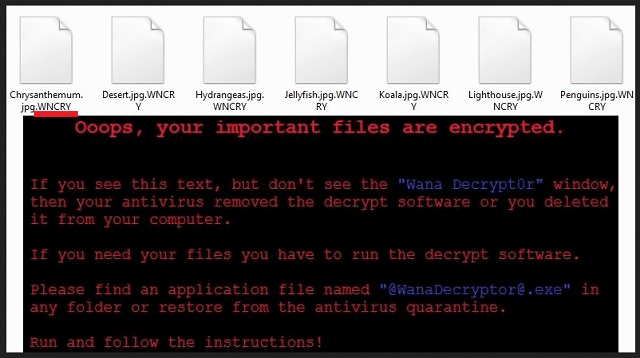
Ooops, your important files are encrypted.
If you see this text, but don’t see the ”Wana Decrypt0r” window,
then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files you have to run the decrypt software.
Please find an application file named “@WanaDecryptor@.exe” in any folder or restore from the antivirus quarantine.
Run and follow the instructions!
It seems that hackers are not wasting their time. They are releasing new ransomware every other day. Wana Decryptor is one of the newest ransomware viruses. And this one is deadly. Wana Decryptor is a new variant of the infamous WannaCry ransomware. Both viruses are part of the ongoing ransomware cyber-attack. You can distinguish the two viruses by the file extensions they add at the end of all encrypted files. Wana Decryptor adds the .WNCRY file suffix. Thus, if you have a file named example.jpeg, the virus will rename it to example.jpeg.WNCRY. The ransomware exploits a vulnerability in your operating system. Microsoft issued an emergency patch which was supposed to prevent such infections. However, not many users installed it. Otherwise, Wana Decryptor acts as a typical virus of its class. It sneaks into your computer unnoticed and initiates an HDD scan. The virus will locate your files and encrypt them in complete silence. You will not notice any symptoms. Maybe, just maybe, your PC will perform a bit more sluggish, but that is all. Once the encryption process is complete, the ransomware will display its ransom note, as well as, change your desktop background. Typically, the hackers demand Bitcoins. This currency cannot be tacked down. Even authorities won’t be able to help you get your money back. Wana Decryptor is using psychological tricks to make its victims act impulsively. It limits your time. The victims have only three days to pay the demanded ransom. If they don’t, the sum will double. However, if you don’t pay within seven days, the virus will lock your files “forever”. Be rational. Don’t contact the hackers. And most importantly don’t pay the ransom. You are dealing with criminals. You can’t expect them to play fair.
How did I get infected with?
Wana Decryptor is using spam email to spread its payload file. The scheme is simple. You receive an email from a well-known organization or company. The letter has logos and stamps. Everything looks legit. It urges you to download an attached file. This file is corrupted. Once you open it, it will connect your PC to a control server and download the ransomware itself. Your vigilance could have prevented this. Nowadays, it hard to distinguish the junk mail from the legit one. Yet, a trustworthy company will use your real name. If you receive a letter starting with “Dear Customer” or “Dear Friend”, proceed with caution. You are the one who is responsible for your computer’s health. Before opening an email, check the sender’s contacts. There are two simple and fast ways to do so. Enter the questionable email into some search engine. If it was used for shady business, there will be evidence online. Yet, if you are part of the first wave of spam emails, nobody had the chance to complain yet. Therefore, double-check the sender. Let’s say that the email is from an organization. Go to their official website. There, under the contact section, you can find their authorized email addresses. Compare them with the one you have received a message from. If they don’t match, you know what to do. Delete the spam email immediately.
Why is Wana Decryptor dangerous?
Wana Decryptor uses both AES and RSA ciphers to lock your files. These two algorithms are the strongest known. Unless the criminals make a mistake, there is no way to decrypt them. The ransomware targets your most precious files: pictures, documents, databases, etc. To restore them, you must pay a hefty ransom. We recommend against such actions. The hackers may promise a lot, yet, there are no guarantees that they will carry out their part of the deal. If they don’t contact you, or if the decryption tools do not work, you will lose your money. Furthermore, you should not forget that your computer is infected. When you use it to pay the ransom, the virus can record your payment details. Hackers can use that information to further terrorize you and even steal your money. The virus deletes the shadow copies of your system, however, if you have backups saved on an external memory, you can use them to restore your files for free. However, don’t forget to remove the virus first. If you don’t clean your machine, the virus will infect your external memory and lock your newly restored files. Wana Decryptor is a highly dangerous threat. Don’t underestimate it. Whatever you do, proceed with caution. Yet, there is no need to live in fear. Use a trustworthy anti-virus program and clean your computer. Discard your files if it is necessary. Start backing up your system regularly. This way you will be prepared if a ransomware strikes again.
Wana Decryptor Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Wana Decryptor Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wana Decryptor encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wana Decryptor encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



