Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Viro Ransomware?
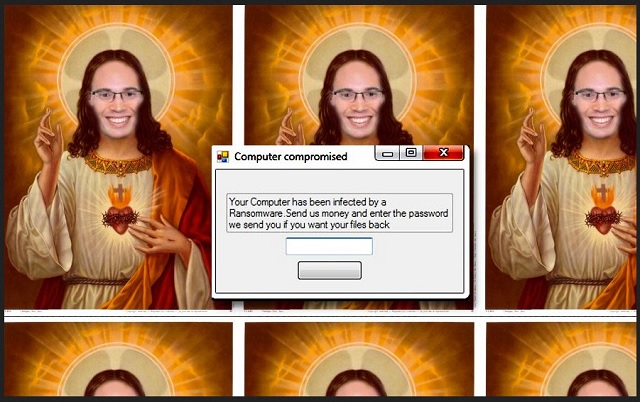
Readers recently started to report the following message being displayed when they boot their computer:
Computer compromised
Your Computer has been infected by a Ransomware. Send us money and enter the password we send you if you want your files back.
[…]
[OK]
The Viro infection is part of the dreaded ransomware family. It’s an updated version of the Hidden-Tear tool. Although, it’s a newer program, it doesn’t quite work right. Experts have noticed that its programming doesn’t function as well as expected. It seems to be an unfinished project, of sorts. And, though, that’s a somewhat positive for you, don’t rejoice yet. Viro is still a dangerous cyber threat. The infection comes bundled with a worm and keylogger. It’s the worm that doesn’t perform to standard. And, the keylogger also has its quirks. Instead of following the footsteps of predecessors, it differs. When it acts up, it doesn’t steal passwords and other sensitive data. As you know, that’s the typical way ransomware work. The keylogger, instead, takes aim at your browsing history. It targets your browsers – Chrome, Firefox and Internet Explorer. After it steals enough data, it extorts you. Once it strikes, it changes your Desktop image. You come to find it replaced with a photoshopped image of a holy picture. After the switch is in place, you begin to see a “Computer compromised” pop-up. You see it all the time. The ransomware forces it on you, non-stop, in an attempt to get you to panic. Then, once in your panicked state, it’s easier to exploit you. The tool tries to get you to act against your best interests. Don’t fall for it! And, remember, Viro’s programming may be lacking today. But its ‘unfinished’ status can change at any given time. There is room for improvement. Don’t give the threat time for updates. Get rid of it now! The sooner you remove it, the safer you’ll be.
How did I get infected with?
Viro turns to the usual antics to invade. It employs the help of the old but gold means of infiltration. The tool often hitches a ride with spam emails. Or, pretends to be a fake system or program update. Apply extra caution when installing a seeming Java or Adobe Flash Player update. Carelessness has consequences. For example, take another favorite method of invasion. Freeware. The infection uses it as a shield to lurk behind. And, if you’re not vigilant enough to spot it, it slips right by you. Don’t allow that to happen. Choose caution over carelessness. Take the time to read the terms and conditions. Look for the fine print. Double-check everything before agreeing to it. To click that YES in a rush could prove to be a colossal mistake. Avoid it! Even a little extra attention goes a long way.
Why is Viro dangerous?
Viro is still a ransomware, like all other. It invades via trickery, then takes over your system. And, corruption ensues. The infection spreads its clutches throughout, and it’s not long before you face its influences. Your data gets locked, and your information taken hostage. Then, you see the demands. The gist is: “Give us money or lose your data.” It seems a simple enough choice, but it’s not. The infection claims that if you comply, and do what it asks, you’ll receive what you need to free yourself of it. But, here’s the thing. Can you trust strangers that hold your information, system, computer, everything, hostage? These are cyber criminals with agendas. Extortionists, who lust for your money. They don’t care if you regain control of your data. What they care about is monetary gain. Profit over propriety. Do NOT rely on them to keep their word. Expect them to break it. Even if you comply to the fullest, it guarantees you nothing. They can double-cross you a dozen different ways. If you’re foolish enough to transfer the sum, they demand, you’ll regret it. Not only do you lose money, but you also lose your privacy. By paying the ransom, you provide personal and financial details. Details, which can then get discovered, and used by the extortionists. Isn’t it enough that they got a hold of your data? Why grant them access to your private life, as well? Protect your privacy. It’s far more precious than pictures and documents. They’re replaceable. Privacy is not.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Viro Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Viro Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Viro encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Viro encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



