Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove HiddenTear 2.0 Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
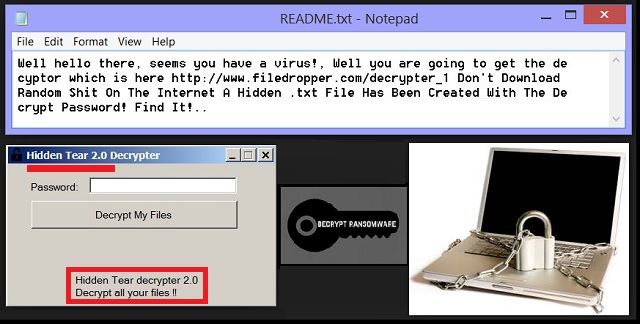
Well hello there, seems you have a virus! Well you are going to get the decryptor which is here http://www.filedropper(.)com/decrypter_1 Don’t Download Random Sh*t On The Internet A Hidden .txt File Has Been Created With The Decrypt Password! Find It!..
Ransomware is considered to be the most problematic and troublesome type of virus online. This title is well-deserved. Who would want to deal with an aggressive file-encrypting infection? Nobody. Nobody would want to have all their data encrypted. Ransomware works in silence and strikes out when you least expect it. This kind of parasite locks your private files and demands a ransom. Yes, you’re supposed to PAY for the privilege to use your own information stored on your own PC. Paying the money guarantees you nothing, though. You may or may not regain access to your locked files. One thing is for sure – you lose money. And hackers gain it. Why are we telling you all of this? Because that is exactly the lesson HiddenTear 2.0 Ransomware wants to teach you. Luckily, this isn’t your everyday ransomware infection. It’s known as a proof-of-concept ransomware virus. Instead of stealing your money, this program’s goal is to educate you on the topic. That means HiddenTear 2.0 Ransomware will NOT ask you to pay a ransom. It will encrypt your files, though. The virus pretty much follows the classic ransomware pattern. As soon as it gets installed, this thing thoroughly scans your machine. Then it uses the infamous AES encryption algorithm to lock your files. All of them. We assume you keep some quite important files on your machine. Is that so? What you may not do is keep backups of your valuable data. The most effective way to protect yourself from damage (apart from prevention) is having backup copies of your files. If HiddenTear 2.0 wasn’t an educational ransomware, you’d be in some serious trouble right now. A huge variety of file formats gets encrypted. That includes pictures, music, videos, Microsoft Office documents, presentations. The target data is now renamed. If you notice the .isis extension added to your data, that means it’s been locked. Therefore, it is now inaccessible. Ransomware is turning your precious files into unreadable gibberish. Your files change format. As you can probably tell, this trick is just a way for hackers to catch you attention. Every single bit of information stored on your machine gets suddenly encrypted. Many people panic when they witness such random, unauthorized modifications. And that’s what crooks hope for. Ransomware allows hackers to blackmail PC users but, as mentioned, HiddenTear 2.0 doesn’t demand any payment. Nevertheless, it still needs to be uninstalled ASAP.
How did I get infected with?
Do you remember installing a ransomware virus? No? That is because you never agreed to download this pest. Instead of waiting for your help, hackers prefer using stealthy tactics. Number one method is also the oldest technique out there. Spam email-attachments. Have you ever received some bizarre email from an unknown sender? Keep in mind that those are immensely dangerous. All sorts of infections could be hiding in a seemingly safe email or message. Usually, crooks present such emails as job applications. Ransomware may also pretend to be an email sent from a shipping company, for example. It is your responsibility to watch out for potential parasites. If you come across some suspicious-looking emails, stay away from them. One single click could compromise your entire computer so be cautious. Another thing to remember is that you should avoid illegitimate websites. The software offered there is often corrupted as well. In addition, malware could travel the Web via exploit kits, fake program updates or fake torrents. You may also have a Trojan horse on your machine that helped the ransomware get installed. Check out your PC for more malicious intruders. In the future, always watch out for parasites and save yourself the hassle.
Why is HiddenTear 2.0 dangerous?
The HiddenTear 2.0 Ransomware encrypts your data. Unlike most ransomware infections, this one doesn’t demand any money from you. It drops a README.txt file on your desktop and informs you about the decryption. According to that note, you don’t have to buy a decryptor. All you have to do is find one certain file on your computer. It provides you a static password to help you restore your data for free. The file is called DecryptPassword.txt and is placed in the My Documents folder. Compared to other ransomware viruses which demand a hefty sum of money in Bitcoin, HiddenTear is definitely less harmless. There are many infections online that will not only lock your files but attempt to scam you. Bear that in mind and stay away from ransomware. To delete this program manually, please follow our detailed removal guide down below.
HiddenTear 2.0 Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover HiddenTear 2.0 Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with HiddenTear 2.0 encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate HiddenTear 2.0 encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



