Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Shade Ransomware?
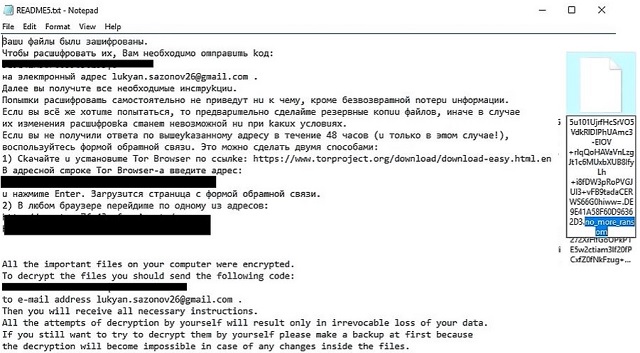
Readers recently started to report the following message being displayed when they boot their computer:
All the important files on your computer were encrypted.
To decrypt the files you should send the following code:
to e-mail address lukyan.sazonov26@gmail.com.
Then you will receive all necessary instructions.
All the attempts of decryption by yourself will result only in irrevocable loss of your data.
If you still want to try to decrypt them by yourself please make a backup at first because
the decryption will become impossible in case of any changes inside the files.
If you did not receive the answer from the aforecited email for more than 48 hours (and only in this case!),
use the feedback form. You can do it by two ways:
1) Download Tor Browser from here:
https://www.torproject.org/download/download-easy.html.en
Install it and type the following address into the address bar:
Press Enter and then the page with feedback form will be loaded.
2) Go to the one of the following addresses in any browser:
Hackers have started to revisit and renew some of their older programs. As a result, we’re up against a wave of improved ransomware infections. For example, the Shade Ransomware is back – stronger and more cunning than ever before. As if it needed progress. There are also new versions of Locky, Cerber and other equally devastating viruses. If you didn’t know it already, ransomware is the worst infection you could catch. File-encrypting programs are very problematic. Why? Unfortunately, you’re about to see for yourself. Shade Ransomware starts its trickery as soon as your computer gets infected. The installation itself happens completely behind your back. Of course, you wouldn’t install one of the most harmful viruses online on purpose. That is why these parasites use sneaky methods to get spread. You’ll learn more about the infiltration down below. Now, back to your problem. The Shade Virus firstly scans your computer. It locates your personal data this way. Pictures, music files, MS Office documents, videos, etc. Ransomware is dreaded for a reason. By using the RSA-2048 and AES CBC 256-bit encrypting cipher, Shade locks your data. All your data. Every single file you’ve stored on your device falls victim to the parasite. Your own files and your own computer. In which parallel universe is this fair? In none. The virus utilizes a strong encrypting algorithm. It messes with the format of the target data and adds a malicious extension. In this particular case, the appendix is .no_more_ransom. However, we have also come across many other extensions associated with Shade – .better_call_saul, .breaking bad, .da_vinci_code, .xtbl, .7h9r, .ytbl, .heisenberg. Each one of them is a giant red flag for danger. If you notice these extensions, it’s game over. Your files have already been encrypted and are no longer accessible. By renaming them, Shade Ransomware turns your data into unreadable gibberish. You can’t open your information thanks to the parasite’s shenanigans. You can’t use your data either. If you thought that was bad, wait till you hear the rest of it. Shade Ransomware creates README.txt files which contain payment instructions. Yes, you’re supposed to PAY a certain amount of money to free your encrypted files. It’s usually not a small sum either. Crooks offer you a deal – you make the payment in the next 48 hours and they provide a decryptor. If you thought paying the ransom was a bad idea, you were correct. Don’t even consider giving your Bitcoins away.
How did I get infected with?
Chances are, the virus was attached to some fake email. This is one of the oldest techniques out there. It is also the most effective tactic. All that hackers have to do is send the infection straight to your inbox. You do the rest by opening the corrupted email. The virus might pretend to be a legitimate email sent from a shipping company. It might get disguised as a job application. Remember, spam email-attachments could be hiding a huge threat to your safety. Delete what you don’t trust and be careful online. Other popular tricks involve freeware bundles, exploit kits or bogus torrents. In addition, Shade Ransomware might have used the help of a Trojan horse. Check out the PC system for more parasites. The ransomware could be having company. Last but not least, stay away from unverified websites as they are often dangerous. The Internet is absolutely infested with parasites so make no mistake. Preventing infiltration is indeed less troublesome than having to delete a virus. Make sure you protect your device from all sorts of malware.
Why is Shade dangerous?
The parasite relies on your anxiety and panic. This is actually nothing but a cyber fraud so you must be very careful. Otherwise, you may get scammed and lose money. Shade Ransomware modifies your personal data. It denies you access to your own information. Furthermore, this pest of a program asks for a ransom. According to its instructions, you have to contact crooks. The message includes an email address – Lukyan.Sazonov26@gmail.com, VladimirScherbinin1991@gmail.com, Novikov.Vavila@gmail.com, etc. Shade Ransomware mainly targets PC users from Russia and Ukraine. However, it could cause you damage anywhere on the globe. Stay away from the suspicious email addresses Shade Ransomware shows you. Paying would only worsen your situation. Hackers have no reason whatsoever to keep their end of the bargain so you cannot trust them. Ignore crooks’ empty promises and threats. Tackle the virus instead. To delete it manually, please follow our removal guide which you’ll find down below.
Shade Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Shade Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Shade encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Shade encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



