Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Scl File Extension Ransomware?
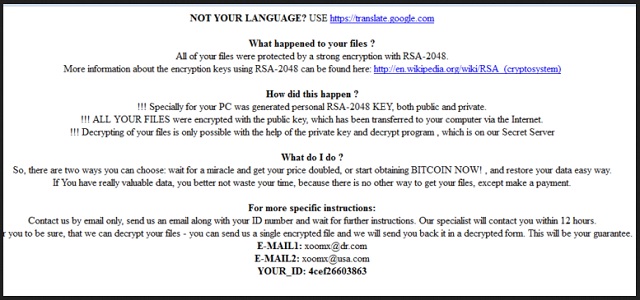
Readers recently started to report the following message being displayed when they boot their computer:
OT YOUR LANGUAGE? USE hxxps://translate.google.com
What happened to your files?
All of your files were protected by a strong encryption with RSA-2048. More information about the encryption keys RSA-2048 can be found here: hxxp://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen?
!!!Specially for your PC was generated personal RSA-2048 KEY, both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program, which is on our Secret Server.
What do I do?
So, there are two ways you can choose: wait for a miracle and get your pride doubled, or start obtaining BITCOIN NOW!, and restore your data easy way. If You have really valuable data, you better not waste your time, because there is no other way to get your files, except make a payment.
For more specific instructions:
Contact is by email only, send us an email along with your ID number and wait for further instructions. Our specialist will contact you within 12 hours. For you to be sure, that we can decrypt your files – you can send us a single encrypted file and we will send you back it in a decrypted form. This will be your guarantee.
E-MAIL1: pchelp_@_post.com
E-MAIL2: xerx_@_usa.com
YOUR_ID:
The program you’re stuck with is called CryptFIle2 (also known as Bandarchor). It’s a member of the nasty ransomware family. Ever heard of ransomware? You’ve somehow managed to get infected with the most problematic and destructive virus online. The Internet is now full of file-encrypting parasites. One of them is currently wreaking havoc on your device. Therefore, it is key for your further safety to take action as soon as possible. Immediately after installation, the parasite goes after your files. It changes their format thus making your data inaccessible. By renaming the target files, CryptFIle2 turns them into unreadable gibberish. This virus adds the .scl file extension. Seeing its malicious appendix only means one thing. You won’t be able to use your very own data anymore. Private pictures, favorite music, important work-related documents. CryptFIle2 modifies a huge variety of formats. It will inevitably cause you harm unless you have backup copies of your files. The CryptFIle2 Malware uses a strong encrypting algorithm. Thanks to the RSA-2048 ciphers, your personal data is now practically unusable. Furthermore, this program’s shenanigans don’t stop here. While locking your data, CryptFIle2 also creates ransom messages. The virus adds HELP_YOUR_FILES.HTML and HELP_YOUR_FILES.TXT files. They appear in all folders which contain locked information. As you could imagine, those are indeed quite a lot of folders. Crooks force their nasty ransom notes on you because this is a scam. Yes, ransomware is nothing but a clever attempt for a cyber fraud. Crooks are aiming directly at your bank account. The question is, are you going to comply? Are you going to help crooks gain illegitimate profit online? Are you going to become their sponsor? Don’t even consider paying the ransom. It’s not a small sum and paying won’t be beneficial for you in any way. As mentioned, the ransomware was developed solely to extort money from gullible PC users. This program also provides you a bunch of email addresses – enc5@dr.com, vexa@usa.com, enc0@dr.com, june7@iname.com, etc. Stay away from all of them. These email addresses will automatically lead you to the parasite’s creators. Keep your Bitcoins instead and get rid of this infection. You won’t regret it.
How did I get infected with?
The most reasonable explanation is that the virus landed on board unnoticed. How is that even possible, you may ask? Easy. Ransomware usually gets attached to spam emails. This way, all you have to do is click the corrupted email open. That is it. The parasite is set free and starts messing with your machine on the spot. To prevent infiltration, always keep an eye out for potential parasites. It is a lot more troublesome to remove malware afterward so don’t be negligent. Ransomware may pretend to be an email from a shipping company, for instance. It could also get disguised as a job application. In addition, stay away from random from messages in social media. These parasites have numerous distribution methods to choose from. However, you must protect your computer from all of them. Always take your time and be cautious. One single minute of haste may result in long hours of fighting a parasite. Other popular techniques involve exploit kits, illegitimate torrents and questionable websites. Avoid what you don’t trust on the Web. Remember, your safety online should be your number one priority.
Why is Scl File Extension dangerous?
CryptFIle2 follows the usual ransomware pattern. This pest of a program denies you access to your own private data. You can’t use or even view your files unless you pay a ransom. In which parallel universe is that a fair deal? As mentioned, this program attempts to steal your money. The very last thing you should do is follow hackers’ instructions. If anything, that will only worsen your situation. You may end up with your PC still compromised, your data still unusable and your money gone. Hackers promise a unique decryptor that’s supposed to free your data. In reality, though, they don’t deliver. You shouldn’t let crooks involve you in their nasty fraud. The CryptFIle is immensely dangerous and cunning. Tackle this intruder without wasting time. Don’t try to negotiate with cyber criminals because that’s simply a battle you can’t win. To delete the ransomware manually, please follow our removal instructions down below.
Scl File Extension Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Scl File Extension Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Scl File Extension encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Scl File Extension encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



