Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove README.hta File Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
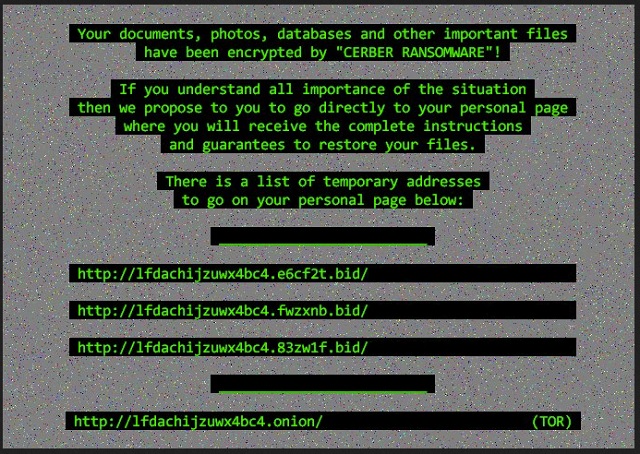
CERBER RANSOMWARE
Instructions
Can’t you find the necessary files?
Is the content of your files not readable?
It is normal because the files’ names and the data in your files have been encrypted by “Cerber Ransomware”.
It means your files are NOT damaged! Your files are modified only. This modification is reversible.
From now it is not possible to use your files until they will be decrypted.
The only way to decrypt your files safely is to buy the special decryption software “Cerber Decryptor”.
Any attempts to restore your files with the third-party software will be fatal for your files!
You can proceed with purchasing of the decryption software at your personal page:
Please wait…
{Unique link for the victim}
README.hta belongs to the ransomware family. Let’s start by cluing you into how ransomware tools work, in general. Well, they are a menace. They throw you into a word of unpleasantness and inconvenience. If you manage to catch such an infection, you’re in for a bad time. The program slithers into your system without you even realizing it. And, once it’s there, proceeds to corrupt it. It gets to work, and locks everything you keep on your PC. That’s right. Every picture, document, video, all your music, just everything! It all falls victim to the ransomware. It encrypts it by adding a special extension that solidifies its hold over it. And, once the encryption is done, you can no longer access your files. You can’t open then, and moving or renaming them, does nothing. The only way to release them from the tool’s grip is with a decryption key. And, the infection makes sure you know that. If you want your data back, you have to pay for it. But no matter the ransom demands, don’t go through with them! Don’t do what you’re told! Don’t be complicit with the cyber crime! Yes, this may sound a bit harsh. But, here’s the thing. If you follow the infection’s requirements, you only bury yourself deeper in problems. Why? Well, to pay the ransom, you have to do a money transfer. And, by doing that, you allow strangers access to your private information. You open the door to your personal and financial details. Then these people can get in any time they want, and they can use what they find as they see fit. You can’t stop them. Because, once it’s opened, that door cannot be closed. So, don’t open it in the first place. Don’t pay the ransom. The people behind the README.hta infection are untrustworthy and malicious. Don’t trust them to keep their promises. They won’t. What they will do is double-cross you. Don’t fall in the trap. These cyber criminals prey on your naivety. Don’t provide it. Prioritize and pick what’s more important. Pictures or privacy?
How did I get infected with?
Ransomware infections are quite sneaky. They tend to sneak in undetected by preying on your careless. For them to invade your system, you need to allow it. Confused? Well, like most cyber threats, ransomware tools need user’s permission to access your PC. They have to ask you for approval, and you have to give it if they’re to enter. So, with that in mind, how do you suppose the exchange went down? After all, if the tool had just come out in the open, and sought your permission, you would have denied it? Right? Well, that’s exactly why it doesn’t do that. Ransomware tools are masters of deception. They seek your approval in the sneakiest way possible. That involves hiding behind freeware or corrupted links or sites. It can also use bogus updates as a shield to lurk behind. Like, Adobe Flash Player or Java update-impostors. However, ransomware tools, like the one plaguing you, tend to turn to emails to gain access to your PC. They attach themselves to an email by an unknown sender. And, if you’re naive enough (or, let’s just say it, foolish enough) to open that email, and also the attachments, that’s it. You get stuck with a dangerous cyber menace, just like README.hta. If you wish to avoid that, and keep your computer infection-free, be wary! Be extra vigilant and cautious. Don’t give into gullibility. Don’t rush. Never discard doing your due diligence. Always remember that even a little extra attention today can save you a ton of troubles tomorrow.
Why is README.hta File dangerous?
We explained the general idea of how ransomware works. Now let’s get into specifics about the one you’re currently stuck with. README.hta is not a program. It’s rather a ransom note. The program it goes with is a variant of one you might have already heard of. Or, even dealt with. It bears the name Cerber. It’s a long-time menace to many users. And, it just doesn’t go away. It keeps coming back. The README.hta note contains what you’d expect. It explains your current predicament. That you’re targeted by a ransomware, which encrypted your data. And, that if you wish to decrypt it, you have to pay a ransom. It’s pretty standard. Even the requested ransom is one, which Cerber victims are accustomed to seeing. The infection demands you pay 1 Bitcoin. But that amount changes after the first five days. After that, it grows to 2 Bitcoins. The longer you delay your decision whether to pay or not, the bigger the requested sum gets. So, we’ll help you. We’ll make the decision for you. DO NOT PAY! And, it’s not even because 1 Bitcoin equals roughly about 600 US dollars. Even if the request was just for a single cent, it still wouldn’t matter. As was already stated, by paying, you let the people behind the ransomware into your private life! And, you don’t want to do that! Don’t expose your personal and financial information to these unknown individuals! Keep strangers away from your privacy. Nothing good can come from cyber criminals having access to such delicate data. And, speaking of data, you need to let yours go. Say goodbye to your files. They’re not worth your privacy. You can replace your files. Can you day the same about your private information?
README.hta File Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover README.hta File Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with README.hta File encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate README.hta File encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



