Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove RarVault@ruggedinbox.com Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
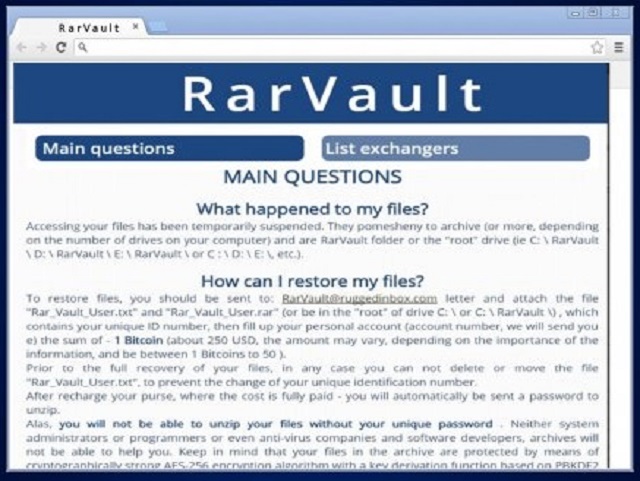
What happened to my files?
Accessing your files has been temporarily suspended. They pomesheny to archive (or more, depending on the number of drives on your computer) and are RarVault folder on the “root” drive (ie C: \ RarVault, D: \ RarVault \ E: \ RarVault \ or C : \ D: \ E: \, etc.).
How can I restore my files?
To restore your files you should be sent to: RarVault@ruggedinbox.com letter and attach the file “Rar_Vault_User.txt” and “Rar_Vault_User.rar” (or be in the “root” of drive C:\’or C: \ RarVault \), which contains your unique ID number, then fill up your personal account (account number, we will sent you e) the sum of – 1 Bitcoin (about 250 USD, the amount may vary, depending on the importance of the information and be between 1 Bitcoins to 50 ).
Prior to the full recovery of your files, in any case you can not delete or move the file “Rar_Vault_User.txt”, to prevent the change of your unique identification number.
After recharge your purse, where the cost is fully paid – you will automatically be sent a password to unzip.
Alas, you will not be able to unzip your files without your unique password . Neither system administrators or programmers or even anti-virus companies and software developers, archives will not be able to help you. Keep in mind that your files in the archive are protected by means of cryptographically strong AES-256 encryption algorithm with a key deviation based on PBKDF2.
There’s a new cryptolocker malware, roaming the web, claiming victims. It’s connected to the RarVault@ruggedinbox.com email address. And, it’s known among users as RarVault, for short. It’s earned the reputation of terrible cyber menace as it’s utter plague on your system. The nasty tool falls in the category of ransomware. It acts like a typical one, although it doesn’t follow the exact pattern of operation. Confused? We’ll elaborate. Yes, the infection locks your files. But it doesn’t do it with a file extension. Instead, it archives them in password protected ZIP files. And, it moves them to a special folder, a vault, if you will. Hence, the name RarVault. Once it creates the password-protected archive, it displays its ransom demands. It leaves a RarVault_User.txt file on the desktop. It clarifies your current predicament, and contains instructions. The cyber criminals prompt you to visit the http://RarVault.myfreesites.net/ page. And, also, to contact them via the RarVault@ruggedinbox.com email. Don’t do it. If you follow their instructions, or reach out to them in any way, you only make things worse. And, here’s what you must understand prior to anything else. If you find yourself a casualty of the RarVault ransomware, you face a tough choice. Should you risk it all for the prospect of reclaiming your locked data? Or, should you play it safe and forsake your files in the name of your privacy? Well, as you may already suspect, experts urge you to pick the latter. Privacy is far more important than pictures. Figure out your priorities, and act in accordance. But do it fast. Don’t delay.
How did I get infected with?
Cyber infections don’t just show up on your computer one day as if by magic. There’s nothing magical about how they got there. The reality of the matter is that you allowed them to invade your PC. Oh, yes. Most (if not all) infections require user’s permission to enter. They have to ask whether you agree to install them, and enter only after your consent. The same goes for the ransomware infection, you’re battling with. It asked, and you complied. And, chances are, you don’t even remember the scenario unfolding. That’s not surprising. After all, the infection doesn’t openly come out and request access to your PC. That leaves too much room for denial. So, it turns to trickery, and inquires for your approval sneakily. More often than not, via the old but gold means of infiltration. After all, they’ve proven their effectiveness over time. Each method cannot succeed without your carelessness. Cyber threats prey on it. They rely on your distraction, gullibility, and haste. So, if you wish to improve your chances of keeping your PC infection-free, be more cautious! Don’t rush and always do your due diligence. You’d be surprised how much trouble even a little extra attention can save you.
Why is RarVault@ruggedinbox.com dangerous?
The RarVault infection slithers into your system undetected. And, its reign of terror begins shortly after. Once it’s settled on your PC, the tool strikes. As was already stated, it does not encrypt your files as most ransomware applications do. Instead, it transfers your data to an archive, protected with a password. You cannot access said archive unless you have the proper password. And, to get it, you have to pay. Don’t think you can just guess it. You can’t. It’s 128-bit long, which renders the task virtually impossible. You can’t crack it. So, the logical assumption, is to pay the ransom, right? Wrong. RarVault employs scare tactics when it comes to its ransom demands. The infection states that the requested sum is 1 Bitcoin. At first. However, it can grow up to 50 Bitcoin with time. Or, if it deems your files are too important for a mere ransom of 1 Bitcoin. If you don’t know the currency, 1 Bitcoin is roughly 500 USD. And, that’s being modest. So, even if the requested amount stays at the bottom of the ransom spectrum, it’s still a lot of money. But it’s not even about the money when it comes to ransomware. Even it asked for a single dollar, it’s ill-advised to comply and pay. Do NOT the sum that the infection demands! It’s a set-up. The program already has a hold over your files. If you pay, you’ll give it access to your personal and financial details, as well. Yes, if you transfer the money it asks for, you hand it control over your privacy. Don’t do that! Don’t dig yourself deeper into the hole of disaster! Instead, cut your losses. Accept that you’ve lost your files to the clutches of a dangerous infection. And, contain its reach. Don’t allow RarVault to steal your private information, as well.
RarVault@ruggedinbox.com Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover RarVault@ruggedinbox.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with RarVault@ruggedinbox.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate RarVault@ruggedinbox.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



