Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove POLIZIA DI STATO Ransomware?
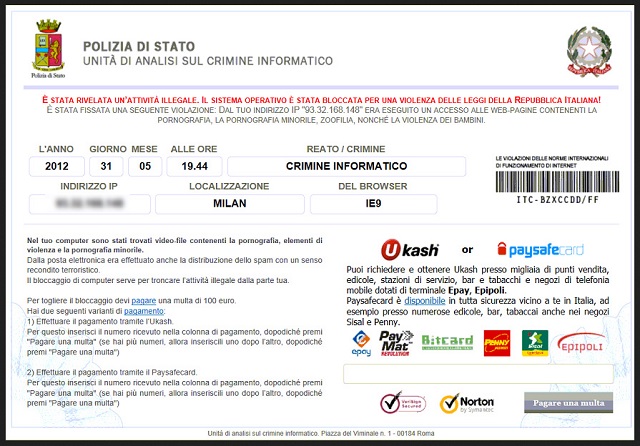
Readers recently started to report the following message being displayed when they boot their computer:
Polizia di stato
Unità di analisi sul crimine informatico
Attenzione! Il Suo computer e bloccato a causa di uno o piu motivi di cui sotto
(…)
Tutte le operazioni fatte a questo computer sono scritte. Se usa la webcam, video, foto si conservano per l’identificazione.Lei può essere individuate facilmente per il Suo indirizzo IP e l’indirizzo del domain legato con esso.Il tuo computer è stato bloccato!
Polizia Di Stato is a ransomware-type cyber parasite. It blocks your PC screen and displays a fake notification. According to this bogus message, you’re having some serious trouble with the law. However, you only have problems with your computer system. The device has been infected with ransomware. That is one of the most cunning, deceptive and dangerous infections online. Ransomware is unpredictable. It goes out of hand very quickly and is capable of causing great damage. Hence, the sooner you take action, the better. Polizia Di Stato has one quite prosaic (and aggravating) goal – stealing your money. It’s a simple scheme, actually. Immediately after installation, the virus displays its deceptive message. As you could imagine, this note has NOTHING to do with the Italian government. It pretends to be a legitimate notification from the police. In this message you’ll read numerous accusations of various online crimes. Watching/distributing pornography, using pirated software and other copyrighted content, etc. Obviously, this isn’t true. Hackers rely on the fact you’ll get nervous, though. Even if you’re perfectly aware these accusations are false, you might believe the lie. After all, a message sent directly from the Italian police could be pretty intimidating. Keep in mind that no legal organization uses online messages and pop-ups to fight crimes. To pretend getting scammed, you have to pay attention. Don’t give into your anxiety because it might cost you a hefty sum of money. Now, crooks demand 100 Euro. This fine is just as fake as your copyright violations. The money you pay will go straight to hackers’ bank account. They will use every single cent they gain to develop more malware. Eventually, more people will have to deal with parasites. Do you really think you should sponsor crooks’ malicious business? Keep your Euro and tackle the ransomware ASAP. You’re supposed to use Ukash or PaySafeCard to make the payment. You also have a deadline. Polizia Di Stato only gives you 72 hours to pay the “fine”. It’s quite obvious that hackers rely on your panic. Don’t even consider complying. You could uninstall the virus without paying anything so do the right thing. Get rid of the virus.
How did I get infected with?
There are many malware distribution methods. That makes it very difficult to determine which one Polizia Di Stato used. However, there are some particularly popular techniques. Hackers’ favorites. Number one are spam messages and corrupted emails. There might be a potential parasite in your inbox right now. Logically, if you click it open, you let the virus loose. Stay away from anything suspicious-looking and be careful. Delete what you don’t trust because email-attachments are usually dangerous. Ransomware also travels the Web with the help of Trojan horses. We highly recommend that you check out the PC for more viruses. It might turn out that the ransomware isn’t your only problem. In addition, avoid illegitimate websites and third-party pop-up ads. Those are unreliable and problematic too. When installing bundled software, take your time during the entire process. If you notice a malicious bonus program, don’t hesitate to deselect it. Never underestimate cyber criminals and their infections. Keep in mind that preventing infiltration is much easier than removing viruses. Last but not least, ransomware gets spread via exploit kits and fake software updates.
Why is POLIZIA DI STATO dangerous?
Polizia Di Stato belongs to the Flimrans ransomware family. Its target are Italian PC users but there are many variations of this pest. We’ve witnesses Canadians and Americans versions of the same scam. As mentioned already, no organization will use a notification to accuse you of crimes. Fortunately, governments don’t work that way. What you must remember is that you’re dealing with a virus. It’s sneaky, skillful and harmful. Restrain yourself from paying anything because that would be a terrible mistake. You don’t have to support greedy cyber criminals. Ignore the parasite’s empty promises and fake threats. Tackle this intruder on the spot. To do so manually, please follow our detailed removal guide down below.
POLIZIA DI STATO Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover POLIZIA DI STATO Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with POLIZIA DI STATO encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate POLIZIA DI STATO encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



