Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove PewDiePie Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
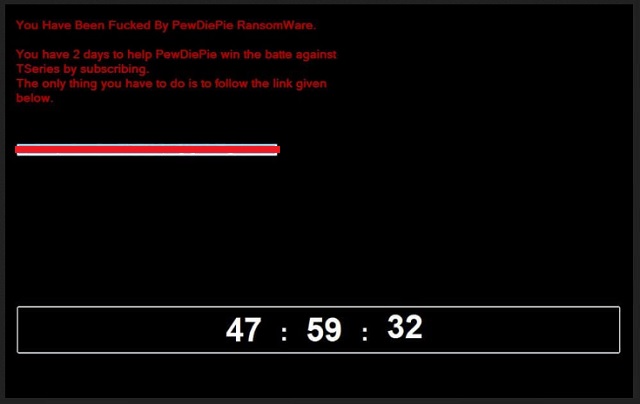
You Have Been Fucked By PewDiePie RansomWare.
You have 2 days to help PewDiePie win the battle against
TSeries by subscribing.
The only thing you have to do is to follow the link given
below.
[YouTube link] [Timer]
PewDiePie is the name of a well-known YouTuber. His channel has the most subscribers, currently hovering above 91 million. Though, he still holds the title, it’s quite the contested race. There’s a large channel that’s been on his tail, for months. It’s called T-Series. The web has thrived on this over-exaggerated ‘feud.’ So, naturally, it’s become a meme, at this point. Users, all over the world, pin the two channels against each other. And, root for one or the other, to win the title. For most people, it’s a fun game, with no real-life consequences. But, there are some, who have taken it to the next level. There’s now a PewDiePie ransomware, plaguing users. And, it’s not your typical one, either. Yes, it still encrypts your files, and lists demands. But, instead of demanding money, it requests you subscribe to PewDiePie. That’s right. It states, that, if you wish to decrypt your data, you must click the provided link. In doing so, it automatically subscribes you to the channel. Or, so it says. Despite it all sounding fun, you can’t be to careful, when it comes to cyber criminals. Click nothing. Don’t engage with the cyber kidnappers. Compliance tends to worsen your predicament, in these cases, and not improve it. So, don’t comply. And, if you wish to subscribe to PewDiePie, do it on your own accord. And, not via shady links, provided by cyber extortionists.
How did I get infected with?
The PewDiePie ransomware makes its way into your PC, via trickery. It uses the old but gold invasive methods. Like, hiding behind corrupted sites, links, or torrents. Or, fake updates and freeware. And, of course, spam emails. Spam emails provide, arguably, the easiest entry point. You get an email that seems legitimate. It appears to come from a well-known company, like Amazon or PayPal. Open it, and it claims you have to verify private information, or confirm a purchase. And, then, states you must click a link, or download an attachment, to do so. It’s all lies. Don’t buy into it. Infections, like ransomware, prey on your carelessness. They hope you don’t notice the deception. That you’re too careless to catch the cyber threat in the act of attempting invasion. Don’t ease the cyber threat’s entry. Always take the time to be vigilant. Look for the fine print, and double-check everything. Read terms and conditions, and know what you say YES to. Caution is crucial, if you wish to keep an infection-free PC. Don’t give into gullibility, and distraction. Don’t rush. Choose caution over carelessness. One keeps trouble out, and the other invites it in.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.

Why is PewDiePie dangerous?
You may recognize the PewDiePie name, from YouTube, but you’re now the victim of a ransomware. And, that’s hardly a fun experience. Once the infection slithers into your system, be wary. It doesn’t take long before it strikes. The tool uses unique encryption algorithms to lock your data. It targets every single file, you have on your computer. Documents, archives, pictures, videos, music. Nothing escapes its reach. The ransomware attaches the ‘.hwuwhdw‘ extension to solidify its grip. After it appends the extension, your files turn unusable. The only way to make them accessible again, is to comply. You’re expected to click the provided link, subscribing to PewDiePie. And, you get 2 days to do so. But, here’s the thing. Though this seems like fun and games, on the surface, you can’t know that’s all it is. You have no assurances that it all ends with a simple click, and a YouTube subscription. What if the link turns out to be malicious? What if it deteriorates your system’s performance even more? What if your data remains locked, despite your compliance? You have ZERO guarantees that following the instructions has a positive outcome. Don’t gamble with your system’s well-being. Whether it’s just another meme, or a grave threat, masquerading as one, don’t take chances. Don’t comply.
PewDiePie Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover PewDiePie Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with PewDiePie encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate PewDiePie encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.