Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Oopslocker Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
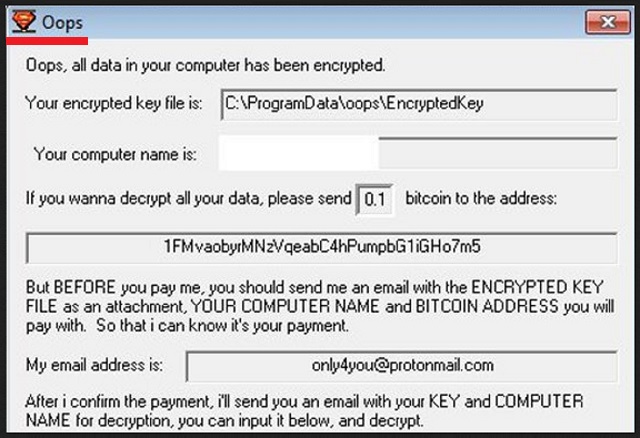
Oops, all data in your computer has been encrypted.
Your encrypted key file is: C: \PrograrnData\oops\EncryptedKey
Your computer name is: *****
If you wanna decrypt all your data, please send 0.1 bitcoin to the address:
1FMvaobyrMNzVqeabC4hPumpbG1iGHo7m5
But BEFORE you pay me, you should send me an email with the ENCRYPTED KEY FILE as an attachment, YOUR COMPUTER NAME and BITCOIN ADDRESS you will pay with. So that i can know it’s your payment.
My email address is: only4you@protonmail. com
After i confirm the payment, i’ll send you an email with your KEY and COMPUTER NAME for decryption, you can input it below, and decrypt.
[…]
[Decrypt]
If you press Decrypt with right KEY, WAIT PATIENTLY, don’t do anything until decryption succeeded I!!
If you close it, you can reopen it in C:\ProgramData\oops\oops.exe.
When you reopen it, you should open as Administrator, otherwise, not all data can be decrypted properly. Very Important!!!
Do not modify anything in the oops folder before you pay!!! Very Important!!!
You’d better pay it in a week, the prize will double every week.
If you have any questions, send me an email. I will reply as soon as possible!
Believe it or not, there is a virus out there named Oops Ransomware. Oopslocker Ransomware is its latest version. Perhaps hackers are running out of creative ransomware names because we’ve recently also tackled WannaCry Ransomware. However, the infection’s name doesn’t affect this program’s level of danger. Ransomware still holds the title of “most destructive parasite” online. To put it mildly, you were quite unlucky to have downloaded the Oopslocker virus. This is a classic representative of the dreaded file-encrypting family. It installs two files – oops.exe and EncryptedFiles.Txt. Once that is complete, trouble starts right away. Thanks to a combination of AES and RSA ciphers, the ransomware locks all your files. Yes, all the information stored on your PC falls victim to this pest. Do you see what makes these parasites so harmful? They go after your personal data. Pictures/photos, music files, videos, MS Office documents. We assume that you store some very important, private data on your machine. However, do you also have backups? Many people overlook the giant threat ransomware poses and have irreplaceable files. Keep in mind that the Internet is currently infested with file-encrypting viruses. There is no guarantee that you wouldn’t come across another ransomware pest. The only way to be one hundred percent certain your files are safe is by keeping backup copies. Oopslocker Ransomware encrypts your files. As mentioned, it targets the personal information on your machine. To be able to lock all of it, this program firstly performs a thorough scan. By doing so, it locates the target files so the next step of its trickery could start. Encryption. You may have noticed that your data is now renamed. Oopslocker Ransomware adds the .oops file extension. Seeing this malicious appendix means the virus is holding your data hostage. It isn’t going to stop here, though. Ransomware has a very solid reason to rename and lock your private information. This is nothing but a cheap attempt for a cyber scam which allows hackers to gain illegal profit. The problem is, crooks take advantage of your anxiety and desire to free your files. Crooks offer a unique decryption key in exchange for 0.1 Bitcoin. For those of you unfamiliar with online currency, that equals 347 USD at the moment. Are you willing to pay almost 350 dollars for the privilege to use your very own files? Do not let hackers blackmail you.
How did I get infected with?
The virus was most likely sent straight to your inbox. One particularly popular malware infiltration technique involves spam messages and emails. Hence, you may receive ransomware that’s disguised as some harmless email-attachment. Watch out for fake job applications or emails from some shipping companies. Unless you spot the virus on time, you might compromise your own security. To prevent that, we’d recommend you pay attention. Note that spam messages and emails are a commonly used technique viruses apply. Delete what you don’t trust instead of clicking it open. You could save yourself quite the trouble that way. These infections also travel the Web via exploit kits, bogus torrents and malicious websites. Be very careful what you give green light to and only download verified software. In addition, keep an eye out for third-party pop-up ads as well as corrupted program bundles. Take your time during the installation so you don’t have to fight an infection afterwards. Last but not least, ransomware often gets downloaded with some help from a Trojan. In other words, you might be having a Trojan horse on your machine. Check out the device for further threats because Oopslocker Ransomware could be having company.
Why is Oopslocker dangerous?
Hackers are not the people to negotiate with. They are solely focused on stealing your money so believing their ransom notes would be a mistake. How the fraud works is, crooks offer a decryptor. On theory, you’re supposed to make the payment in order to receive it. On practice, though, freeing your locked information is hackers’ very last concern. Even if you immediately pay the ransom, your files may remain encrypted and inaccessible. You’d be completely dependent on greedy cyber criminals who are shameless enough to blackmail you. Keep your 347 dollars instead of becoming a sponsor of crooks. Stay away from the only4you@protonmail.com email address provided and tackle the ransomware right away. You will find our detailed manual removal guide down below.
Oopslocker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Oopslocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Oopslocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Oopslocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



