Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Nuke Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
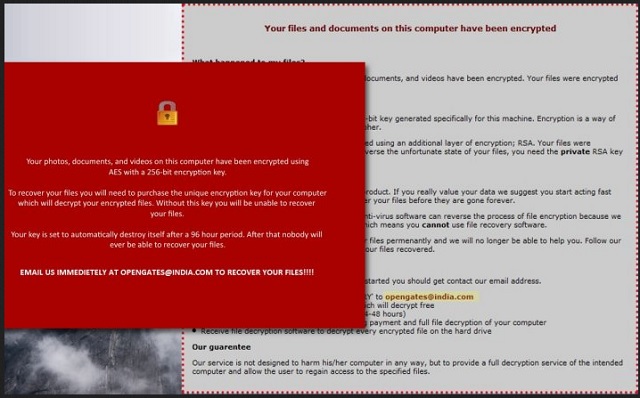
!! Your files and documents on this computer have been encrypted !!
** What has happened to my files? **
Your important files on your computer; photos, documents, and videos have been encrypted. Your files were encrypted using AES and RSA encryption.
** What does this mean? **
File encryption was produced using a unique 256-bit key generated specifically for this machine. Encryption is a way of securing data and requires a special key to decipher.
Unfortunate for you, this special key was encrypted using an additional layer of encryption; RSA. Your files were encrypted using the public RSA key. To truly reverse the unfortunate state of your files, you need the private RSA key which is only known by us.
** What should I do next? **
For your information your private key is a paid product. If you really value your data we suggest you start acting fast because you only short amount of time to recover your files before they are gone forever.
There are no solutions to this problem, and no anti-virus software can reverse the process of file encryption because we have also erased recent versions of your files which means you cannot use file recovery software.
Modifying your files in any way can damage your files permanently and we will no longer be able to help you. Follow our terms assigned to you below, and we will have your files recovered.
** Recovering your files **
– Send an email with the subject ‘FILE RECOVERY’ to opengates@india.com
– For a free test decrypt, send one small file which will decrypt free
– Wait for a response from us (up to 24-48 hours)
– We will send you further information regarding payment and full file decryption of your computer
– Receive file decryption software to decrypt every encrypted file on the hard drive
It remains a mystery why hackers chose to name their parasite Nuke. What is crystal clear is the fact nobody wants to deal with ransomware. However, these infections are practically everywhere on the Web. The nasty Nuke Virus was discovered just a couple of days ago and it’s one of many. Actually, ransomware is on the rise right now for one very simple reason. These programs help hackers gain profit. They are also considered to be the most virulent programs on the Web. As you could imagine, this is a well-deserved title. What makes Nuke Ransomware so dangerous? For starters, it’s a file-encrypting virus. That means it uses a complicated encrypting algorithm (RSA) to lock your files. All your files. Ransomware doesn’t discriminate between the different file formats you’ve stored on your PC. Nuke is no exception. It utilizes the AES-256 cipher and takes down all your files. We’re talking music, pictures, MS Office documents, even videos and presentations. Do you see why ransomware is so immensely dreaded? The virus locks your private files and keeps them hostage. Nuke Ransomware renames the target data with a random combination of characters. It also adds the malicious “.0x5bm” extension to them. Seeing this bizarre appendix only means one thing. Your data is no longer accessible. As mentioned, ransomware locks your information. By changing its format, Nuke makes your files unreadable. Your computer can’t recognize this new file format. As a result, you can’t use or even open your very own files. If you think that’s unfair, wait till you hear the rest. Nuke Ransomware is just getting started. Now that all your data is locked, the virus starts testing your nerves. It creates “!!_RECOVERY_instructions_!!.html” and “!!_RECOVERY_instructions_!!.txt” files. Your desktop wallpaper gets modified as well. As you can see, hackers really insist that you see their ransom note. Why? Because they want you to panic. According to these dubious ransom messages, your files have been encrypted. As if you didn’t know it already. Nuke Ransomware also provides you an email address – opengates@india.com. You’re supposed to contact hackers in order to free your data. And having your files back doesn’t come for free. At the end of the day, ransomware is nothing but a nasty online scam. It tries to steal your money by tricking you into paying a ransom. Are you willing to give away your Bitcoins, though? Crooks do offer a decryptor (a unique combination of symbols that unlocks your data). However, making a deal with cyber criminals would be a terrible mistake and you know it.
How did I get infected with?
You’ve clicked something open that you should have ignored. For instance, a corrupted email or a harmful message. Getting your device infected is quite an easy task so don’t underestimate hackers’ creativity. Stay away from suspicious emails and spam email-attachments. The virus might pretend to be a job application or legitimate mail from a shipping company. Next time you receive something in your inbox that you don’t trust, delete it. Don’t take any chances because you might infect your own PC with malware. Be cautious. Parasites also travel the Web via illegitimate torrents/websites/software bundles. In addition, Nuke Ransomware might have landed on board with the help of a Trojan. Yes, this program may not be the only virus you have to worry about. Pay attention online and always watch out for potential threats. Preventing infiltration is much easier than having to remove a virus afterwards. Our advice is to be careful online and make sure you avoid hackers’ endless tricks.
Why is Nuke dangerous?
Just like Cerber, Killer Locker, Locky, Nagini, etc., this thing is very dangerous. By locking your precious files, it attempts to blackmail you. As you could imagine, having your data encrypted may cause some serious damage. Whatever Nuke Ransomware locks, becomes unreadable. The parasite turns your files into unusable gibberish. In order to free your information, you have to pay a ransom. Furthermore, you have a deadline. Nuke only gives you 96 hours to complete the payment. Obviously, this is yet another cheap trickery hackers play on you. They will not provide you any decryption tool no matter what they promise. Think about it. You’d be giving your money to crooks. Do you really believe they will help you? They are the ones who locked your data in the first place. Stay away from the parasite’s email address and don’t even consider paying the ransom. If anything, that will only worsen your situation. To delete Nuke Ransomware manually, please follow our removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Nuke Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Nuke Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Nuke encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Nuke encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



