Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Suddenly Nuesearch.com took over your homepage and you cannot remove it.
Nuesearch.com has been classified as browser hijacker. Have your browser settings been modified behind your back? Is the machine now sluggish? Do your browsers crash and freeze on a daily basis? If so, then it’s safe to say you’re in trouble. In other words, your computer system has been infected with a hijacker. As you could imagine, the sooner you take action, the better. We have never come across a hijacker that deletes itself and chance are, neither have you. In this particular case the virus you’re stuck with is called Nuesearch.com. It follows the classic hijacker pattern which means it lies shamelessly in your face. If you check out Nuesearch.com’s official website, you’ll read that this program delivers “more relevant and comprehensive results every time you search”. It goes without saying this isn’t true. The only thing Nuesearch.com will indeed provide you is quick and easy access to malware. Are you upset already? This is just the begging. Behind the parasite’s sugary facade of a perfectly legitimate search engine lies a sneaky, aggressive and very dangerous infection. Yes, it’s supposed to enhance your browsing experience. In reality, though, the hijacker’s very last concern is to be beneficial for you. If anything, it’s only beneficial for its developers. Since the moment your machine gets compromised, Nuesearch.com begins to serve hackers’ purposes. Trust us when we say, crooks’ plans greatly mismatch your own. The parasite replaces both your default search engine and default browser homepage with its malicious domain so now you’re forced to use it every time you surf the Web. There are numerous problems with this domain, though. Problem number one – your consent or permission or authorization or any kind for these browser modifications wasn’t required. Once the PC gets compromised, your entire browser experience is no longer up to you. That means your preferences and opinions about your own machine simply don’t matter anymore. Problem number two – Nuesearch.com’s search engine generates sponsored, tailored search results. The virus also presents them as accurate and safe so it could trick you into clicking. Do you want to know why? Because each time you click some sponsored web link generated by Nuesearch.com, its creators gain profit. Now that you know money is at the bottom of this entire scheme, are you feeling nervous? Hackers don’t seem to think twice when revenue is involved and they have absolutely no reason to take care of your safety. There’s no doubt some web links you currently see on your PC screen lead directly to malware. You might end up on a highly questionable website infested with parasites thus causing your machine even greater damage. To prevent such an unpleasant scenario, stay away from anything brought to you by Nuesearch.com; you won’t regret it.

How did I get infected with?
Speaking of Nuesearch.com’s official page, we didn’t mention the fact there is no download option to be seen on the website. A rule of thumb for the future – not having a download button is a huge red flag concerning any program’s reliability. Obviously, the hijacker used some stealthy infiltration method in order to land on board. The most popular technique right now is freeware/shareware bundling and it’s so immensely effective that all types of infections apply it. Every single time you download programs off of the Internet, watch out for malware. Furthermore, pay close attention to all programs that come bundled, especially if they also come for free. There might be a whole bunch of viruses attached to the bundle; unless you’re very cautious, you’ll install the parasites as well. Opt for the advanced/custom option in the Setup Wizard and don’t be careless. Remember that preventing virus installation is much easier that removing some vicious infection later on. Last but not least, don’t skip reading the Terms and Conditions. You should always be aware what exactly you accept, shouldn’t you?
Why is this dangerous?
Nuesearch.com installs a malicious browser extension. Of course, this plugin is compatible with three of the most commonly used browsers out there – Google Chrome, Mozilla Firefox and Internet Explorer. As we mentioned already, this program is very problematic. It’s one goal is to generate web traffic towards some specific websites which may or may not be dangerous. However, are you willing to risk infecting your PC with more parasites? Regardless of how attractive Nuesearch.com’s search results are, stay away from them. The virus also stubbornly redirects you thus jeopardizing your safety even further. To top it all, Nuesearch.com collects browsing-related information such as browsing history, search queries, passwords, usernames, email addresses, etc. As you could imagine, your personal information gets diligently monitored and sent to hackers. Yes, greedy cyber criminals with questionable intentions now have access to your sensitive data. Don’t waste time. To delete Nuesearch.com manually, please follow the comprehensive removal guide you’ll find down below.
How to Remove Nuesearch.com virus
If you feel technical enough you may proceed with Manual Virus Removal
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
If you perform exactly the steps below you should be able to remove the Newsearch.com infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with the Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate the Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 6: Make sure your Windows HOSTS file is clean
- open your explorer and Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
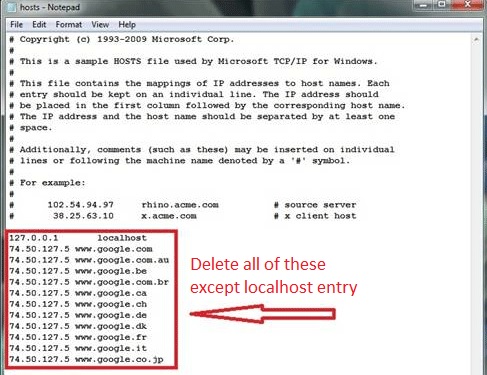
If you are uncertain about the IPs below “Localhost” contact us in out google+ profile and we will try to help you.
STEP 7: Check your internet connection settings
- Right-click on the active Network Adapter, Click on Properties
- Navigate to Internet Protocol Version 4 (ICP/IP), click Properties.
- Click on Advanced and then navigate to the DNS TAB. The DNS line should be set to Obtain DNS server automatically. If it is not, set it yourself.
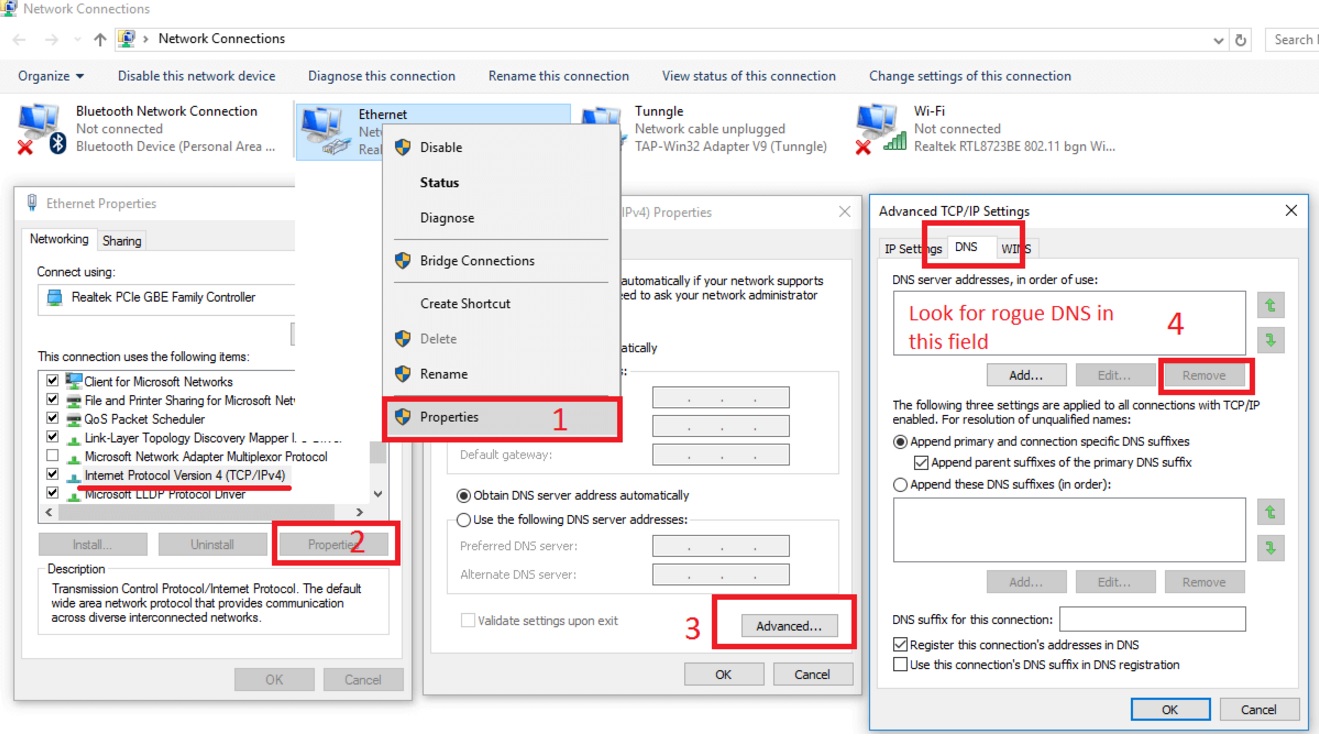
Double check your proxy settings as the malware is capable of modifying them.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for example, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
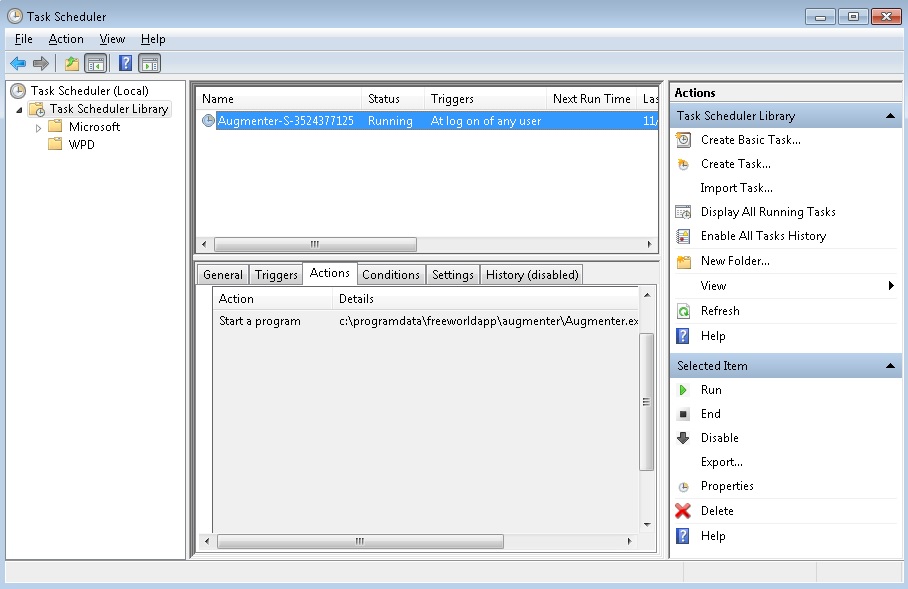
STEP 8: Check your Scheduled Tasks
- Open your windows task scheduler and delete any suspicious program. Usually, adware applications hide their droppers in here. Even if you remove the whole infection from the system files – the dropper will regenerate everything and the nightmare will start again.
Step 9: Repair system files.
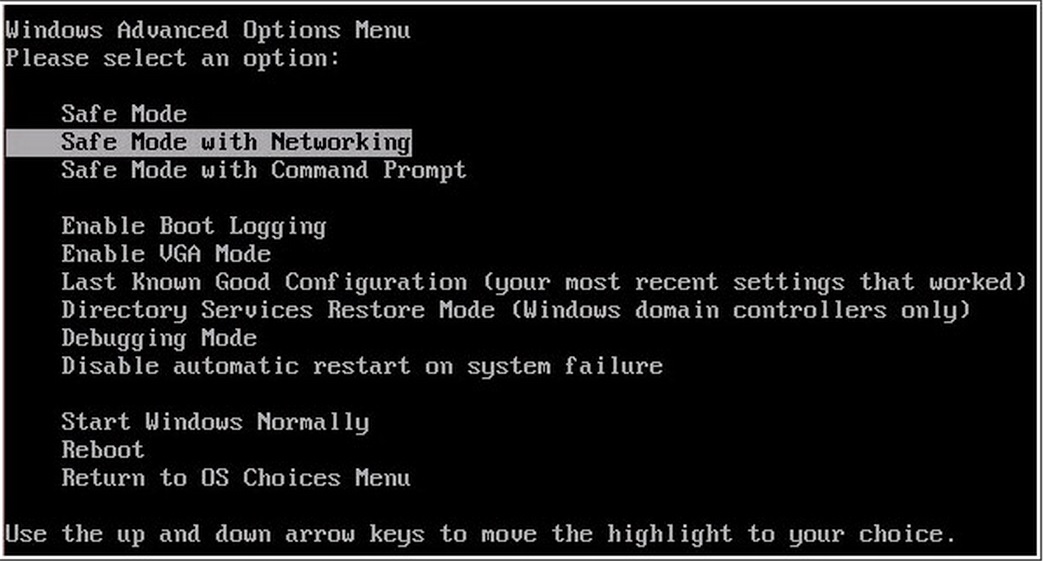
For this step you need to start Your Computer into Safe Mode with Networking
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

- For Windows 8, press the Windows key + C, and then click Settings. Click Power, hold Shift Key and click Restart, then click on Troubleshoot and select Advanced options. In the Advanced Options screen, choose Startup Settings, then hit Restart. When in safe mode go to Enable Safe Mode with Networking.
- If you are using Windows XP, Vista or 7 in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking, and then press ENTER.
- Once you have rebooted in Safe Mode type “cmd” in the Search Field.
- Right Click on it and choose Run as Administrator.
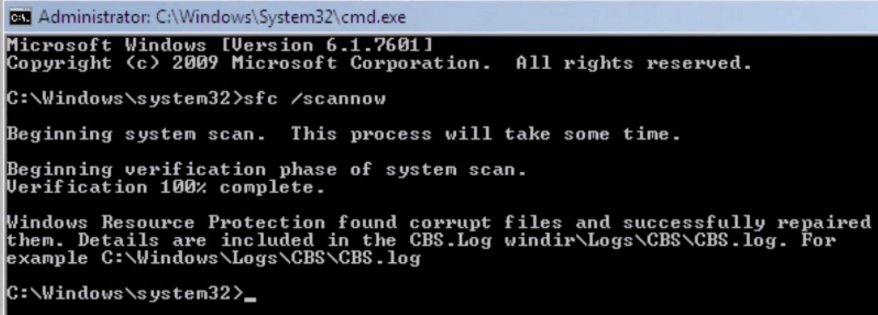
- In the new window that will appear type sfc /scannow and press Enter.
- Wait for the verification process to finish.
- You should get the following message:
You must clean all your browser shortcuts as well. To do that you need to
- Right click on the shortcut of your favorite browser and then select properties.
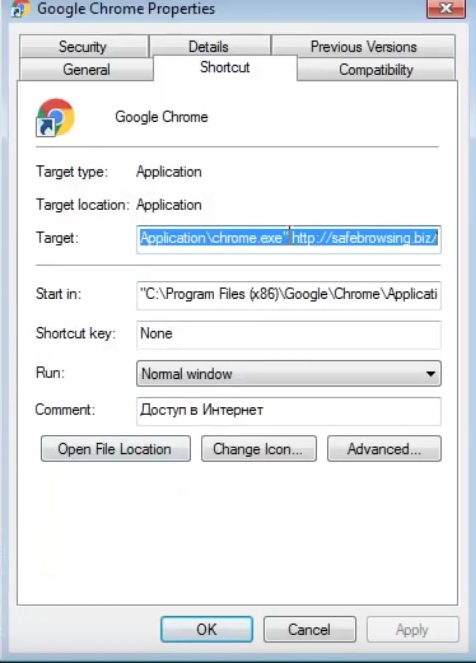
- in the target field remove malicious URL argument and then apply the changes.
- Repeat that with the shortcuts of your other browsers.
At this point, you should not have the Nuesearch.com infection anymore. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify malware registry leftovers or temporary files.