Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Norvas Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
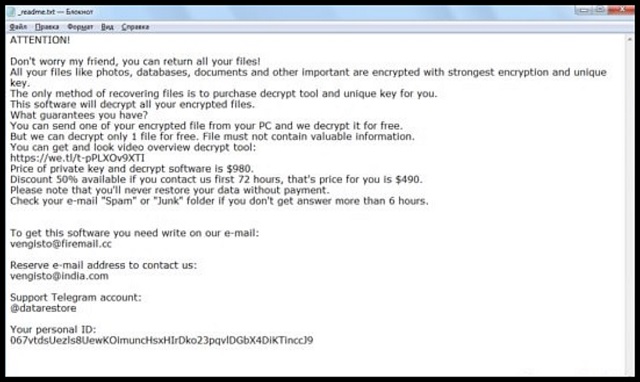
ATTENTION!
Do not worry my friend, you can return all your files!
All your files are encrypted with the unique key.
Decrypt tool for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get a video of the decrypt tool:
https://we.tl/t-pPLXOv9XTI
Price is $ 980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $ 490.
Please note that you never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get it answer more than 6 hours.
To get this software you need to write on our e-mail:
vengisto@firemail.cc
Reserve e-mail address to contact us:
vengisto@india.com
Support Telegram account:
@datarestore
Your personal ID:
Norvas is an atrocious ransomware. It’s a version of the Djvu ransomware, which is part of the STOP family of threats. The infection uses slyness to infiltrate your system. Then, spreads corruption. It targets every file, you have, and encrypts it. Then, it extorts you for money. It demands you pay up, if you wish to decrypt the locked data. You’ve fallen victim to a classic blackmailing scheme. After the ransomware seizes control over your files, it proceeds to list its demands. No matter its requirements, don’t follow them! Do nothing, it asks of you. Compliance will not solve your predicament. Payment won’t make your problems go away. The infection counts on you to act rash. To give into naivety and fear, and do something, you’ll later regret. Don’t oblige. Don’t act against your best interest, by following the tune of cyber kidnappers. Don’t comply.
How did I get infected with?
Norvas uses trickery to invade your PC. The most common method, the tool turns to, is via spam email. You get an email, one day, that seems legitimate. It appears to come from a well-known company, like Amazon or PayPal. And, it reads that you have to verify some private information, or confirm a purchase. To do so, it requests you click a certain link, or download an attachment. If you follow through, you end up with an infection. Don’t click or download anything! Take everything with a grain of salt. Always take the time to be thorough. Look for the fine print, double-check everything. Don’t discard the importance of vigilance. Even a little extra attention can save you a ton of troubles. Caution helps you to keep a system, free of infections. And, carelessness does the opposite. Keep that in mind.
Why is Norvas dangerous?
After Norvas slithers its way in, it strikes. It targets every file, you keep on your PC. Pictures, archives, documents, videos, music. Nothing escapes its clutches. The tool uses cryptography algorithms to lock it all. To solidify ts grip, it appens the ‘.norvas‘ extension, as well. Say, you have a music file called ‘no.mp3.’ After Norvas, it becomes ‘no.mp3.norvas.’ And, once that happens, it becomes unusable. Moving or renaming it proves futile. The only way to regain access to your data, is via a unique decryption key. And, to get it, you must pay up. The infection makes that clear, in the note it leaves you. It’s a text file, called “_readme.txt.” It’s pretty standard, as far as ransomware notes go. It explains your predicament, and gives you one way out. Compliance. Supposedly, if you pay $980, you’ll get the key. And, if you pay within the “ first 72 hours,” you’ll get a “50% discount.” The key word here is ‘supposedly.’ No matter the promises it makes, you have no guarantees. You’d do best to keep that in mind. The infection lists demands, threats and whatnot. But you have no assurances that compliance will work. Let’s examine your options, shall we? Say, you decide to pay up. You make the payment, and await to receive the promise decryption key. Well, what if you don’t get it? The extortionists can choose not to send it. Then, what? You’ve less money, and your data remains locked. Or, say, you do get the key, but it proves to be the wrong one. Then, again, you’re left with less money and locked data. But even in your best-case scenario, you’re still not in the clear. Even if it all goes according to your expectations, then what? Yes, you paid, got the key, and decrypted your data. But what follows that? You paid money to remove a symptom of the infection, not the infection itself. The Norvas ransomware still lurks on your PC, despite your compliance. What if the tool chooses to strike mere moments after you apply your newly-received key? It can do that. And, then, you’re back to square one. Only, this time, you have less money and locked data. Don’t pay these cyber criminals a dime. Don’t comply!
Norvas Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Norvas Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Norvas encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Norvas encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


