Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Noob Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
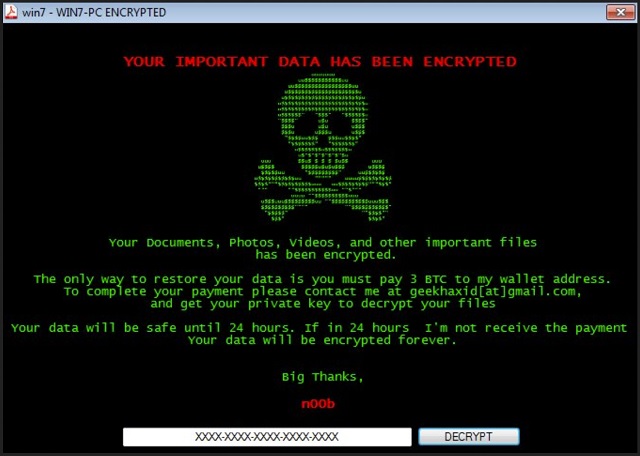
YOUR IMPORTANT DATA HAS BEEN ENCRYPTED
Your Documents, Photos, Videos, and other important files
has been encrypted.
The only way to restore your data is you must pay 3 BTC to my wallet address.
To complete your payment please contact me at geekhaxid[at]gmail.com,
and get your private key to decrypt your files
Your data will be safe until 24 hours I’m not receive the payment
Your data will be encrypted forever.
Big Thanks,
n00b
XXXXX-XXXXX-XXXXX-XXXXX-XXXXX DECRYPT
Noob is the latest cryptovirus infection, roaming the web and plaguing users. The ransomware earned its name with the note, it leaves you. Let’s elaborate. The cyber plague spreads throughout your system, and corrupts it. It encrypts each file you have on your computer. And, makes it impossible for you to access your documents, pictures, anything. Everything gets locked, and only Noob has the key. As you may imagine, if you want it, you have to pay for it. The infection makes that clear in the ransom note. It leaves it behind after encryption gets done. Once Noob completes the process, and all your data gets locked, you see a TXT file. It’s on your Desktop, as well as in each of your affected folders. In that note, it refers to you, the victim, as ‘n00b.’ Noob’s note is exactly what you’d expect as it’s pretty standard. It explains your situation. How your files got locked by a ransomware, and payment is your only way out. If you wish to see your files again, you have to pay. Right? Only then, will you receive the key that removes the encryption. It’s rather straightforward. The tool demands 3 Bitcoins in exchange for the decryption key. Right now, that’s about 3000 US Dollars. It’s no small fee. But even if it were a single dime, experts still advise against payment. It’s all smoke and mirrors. A delusion of false safety. Payment is supposed to solve your problems. But it doesn’t! It creates many more! Do NOT pay! Don’t buy the infection’s false promises! You’ll get deeper in trouble if you do. It’s not about the money, it’s about trust and guarantees. Of which you have none! You cannot trust cyber criminals to keep their word. And, you have no guarantees that payment solves anything. Heed experts advise. Don’t pay. It’s hard, but it’s best to say goodbye to your files. Accept they’re lost to you, and next time make back-ups. Discarding your data is the lesser of two evils.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
Noob invades your system via the usual trickery. It preys on your naivety, and dupes you into allowing it in. Most cyber threats use freeware as a means of infiltration. That’s because it’s most favorable for covert invasions. It provides the sneakiest access point to your PC. Why? Well, chances are, you’re not as attentive as you should be when dealing with it. When installing freeware, most users throw caution to the wind. They don’t do their due diligence but, instead, rely on luck. That strategy often results in infection, slithering into your system. Don’t discard the importance of due diligence! Always read the terms and conditions. Don’t give into naivety and haste, and say ‘Yes’ to everything. Vigilance goes a long way. And, it can save you dealings with threats as severe as Noob. Choose caution over carelessness. One leads to infections, slipping right by you, and corrupting your PC. The other keeps them out. You choose which one to go which.
Why is Noob dangerous?
Noob is thought to be a sort of extended family to the HiddenTear infection. Much like AngleWare and MafiaWare, it doesn’t particularly stand out. It follows standard instructions. After it locks your files, you face a choice. You have a decision to make – to pay or not to pay? Let’s examine your choices. If you don’t pay, you lose your files. That’s the better alternative. That’s the way, experts want you to go. And, there’s a reason for that. And, it isn’t to save you money. It’s to protect your privacy. Because, here’s what happens if you go through with the extortion. When you transfer the money, you provide private details. You leave your personal and financial information for the infection to find. And, once it gets its hands on it, it can use it as it sees fit. Don’t let the cyber criminals behind Noob have a field day with your privacy. Protect it! Don’t pay. Also, payment guarantees you nothing. Well, besides extortionists getting a hold of your private life. And, losing all that money. What do you expect happens after payment? You receive the needed key, apply it, and all’s fine and dandy? No. What if the ransomware doesn’t send you a key at all? Or, gives you one that doesn’t work? And, even if you get the one, you need, what then? The decryption key decrypt your data. It removes the encryption, the ransomware put there. Not the ransomware itself. It does nothing to solve your actual problem, which s that you have an infection on your hands. One that lurks somewhere on your PC, ready to strike again at any moment. Think about all you know now, and you’ll come to the realization that experts are right. It’s a tough call to make, but you have to make it. Forsake your files. They’re replaceable, and privacy is not.
Noob Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Noob Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Noob encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Noob encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



