Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove MongoLock Ransomware?
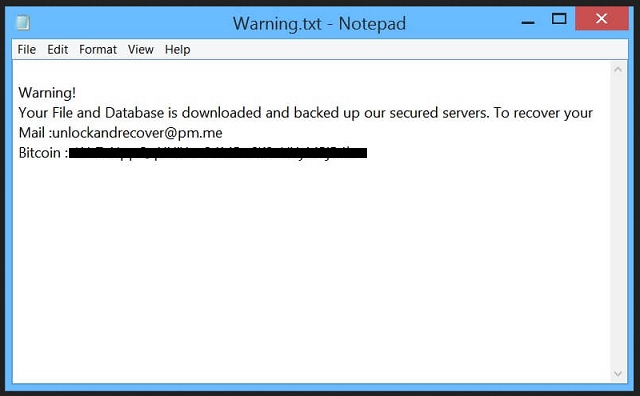
Readers recently started to report the following message being displayed when they boot their computer:
Warning!
Your File and DataBase is downloaded and backed up on our secured servers. To recover your lost data : Send 0.1 BTC to our BitCoin Address and Contact us by eMail with your server IP Address and a Proof of Payment. Any eMail without your server IP Address and a Proof of Payment together will be ignored. We will drop the backup after 24 hours. You are welcome!
Mail:unlockandrecover@pm.me
BitCoin:1NrZsNppQqXNiYnu34MPo6K2sHYyMPjR4h
The latest ransomware, plaguing users, goes by the name MongoLock. MongoLock is not quite the same as all other threats of its kind. Yes, it attacks your PC and extorts you for money. But there are differences with its approach. Differences for the worse. You see, most ransomware threats attack your PC, and lock your data. Your files remain on your computer, while out of your reach, because they’re encrypted. But they are there! With MongoLock, that’s not the case. Once the cyber threat strikes, it deletes your files. That’s right. It deletes your data, and formats your drive. It leaves a ransom note for you to discover. It’s a text file called ‘Warning.txt.‘ It’s concise and clear. It cuts to the chase, and doesn’t even explain, you’re victim to a ransomware. Instead, it attempts to calm your panic, by claiming that your files are safe. That, “your File and DataBase is downloaded and backed up on our secured servers.” It continues to provide instructions. Supposedly, if you wish to regain your data, you must pay a ransom. It’s 0.1 BTC to a BitCoin Address, which they’ve included in the note. After payment, you have to reach out to these people via email. They’ve included that, as well. In the email, you must provide proof of payment, and your server IP Address. Once you do that, they promise to “drop the backup after 24 hours.” Let that sink in. Cyber criminals infiltrate your system, corrupt it, delete your data, and demand payment. They expect you to comply, and leave you with nothing but their promise. Their promise to hold their end of the bargain, and give your data back to you. These are cyber kidnappers with malicious intentions. They’re not people, you can count on, or trust. Don’t rely on them to keep their word. They won’t! Don’t waste your time, money, or energy dealing with them. You will not come out on top.
How did I get infected with?
MongoLock ends up on your computer via deception. The infection uses the old but gold invasive methods. And, slithers into your system undetected. But no matter how sly the tool is, it still can’t invade without you. Well, rather, your carelessness. It’s the key ingredient that ensures its successful invasion. Here’s the thing. The ransomware uses freeware to conceal itself. It can also pretend to be a fake update. Or, lurk behind corrupted links, or sites. But, the most common method it chooses, is via spam email. One day, you get an email that appears to come from a legitimate company. A well-known one, like Amazon or DHL. The email urges you to click a certain link, or download an attachment, it contains. If you do, that’s it. You get stuck with MongoLock, and lose your data. You see, infections prey on user’s distraction, haste, and naivety. Ransomware tools are no exception. They need you to rush, and not bother to do your due diligence. They rely on you to leave your fate to chance. Don’t! Don’t make their infiltration easier. Always choose caution over the lack thereof. Vigilance helps to keep an infection-free PC. And, even a little extra attention can save you a ton of troubles.
Why is MongoLock dangerous?
MongoLock uses scare tactics to get you to act against your best interest. It relies on you to panic, and do what it demands of it. And, do it, with no thought of consequences. It counts on your carelessness. Don’t fall for its trickery. Don’t pay these people for you will regret it, if you do. Think about it. Let’s examine your options. Say, you comply to the fullest. You pay, send proof of payment, and wait. These people promised to send you your data back, right? What if they don’t? What’s to stop them from double-crossing you? You’ve already sent them money. Why should they follow through on their word? They have nothing to lose by breaking their promise. Why would you trust strangers that extort you for money? Don’t be so naive! The odds are not in your favor. Don’t put your faith onto cyber kidnappers. Instead, put your faith onto backup storage. Like, cloud services and external storage.
MongoLock Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover MongoLock Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with MongoLock encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate MongoLock encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.


