Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Milarepa.lotos@aol.com Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
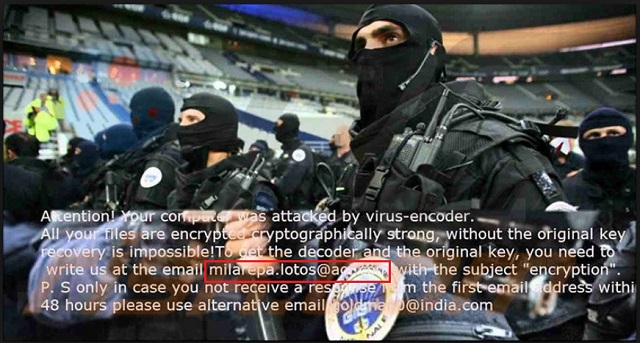
Attention! Your computer was attacked by virus-encoder.
All your files are encrypted cryptographically strong, without the original key
recovery is impossible! To get the decoder and the original key, you need to
write us at the email milarepa.lotos@aol.com with the subject “encryption”.
P.S. only in case you not receive a response from the first email address within
48 hours please use alternative email email-goldmail@india.com
Milarepa.lotos@aol.com is an email addresses which will contact you with hackers. That sentence alone should be enough to make you realize how serious the situation is. You’ve fallen victim to one particularly virulent infection. Ransomware. Have you heard of it? Ransomware is a file-encrypting virus that locks your personal data. And, by “persona data”, we mean all files you’ve stored on the PC system. All your pictures, videos, MS Office documents, music, etc. Anything of value on your computer gets encrypted. Do you see why PC users dread ransomware? This infection is among the most dangerous, aggressive and problematic programs out there. You have been unfortunate enough to download it, therefore, you have to take action ASAP. Now, how does this pest work? First of all, it’s part of the infamous Crysis Ransomware family. Immediately after installation, the virus performs a thorough scan on your computer. It locates your files. As already mentioned, this nuisance takes down a huge amount of file formats. The target data gets encrypted with RSA-2048 – quite a popular algorithm. Thanks to this complicated encrypting cipher, your private information is now inaccessible. Yes, ransomware denies you access to your own data. And that’s not even the worst part. After encryption is complete, your files get renamed. They receive a brand new file extension which replaces the original one. Obviously, this appendix is malicious. It includes a unique ID and ends with {Milarepa.lotos@aol.com}.CrySiS. Your computer is unable to recognize this new file format. Logically, you’re unable to use your information. Why is this whole thing needed? Why are hackers so desperate to lock your personal files? Because you might be willing to pay a hefty sum of money to set them free. We’ve reached the sole purpose ransomware-type infections have – to blackmail you. While encrypting your data, the virus also drops Decryption instructions.txt files. They contain a detailed ransom message. Yes, crooks offer you a deal. A bargain. A way to restore access to your pictures and other unreadable files. The question is, why trust hackers? Even though they promise a decryption key, crooks are only aiming for revenue. That means even if you pay the ransom, it’s very likely you’ll be ignored. Furthermore, your files will remain encrypted.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
Stay away from suspicious -looking emails. This might be the oldest trick in the books but it seems to be working very well to date. Remember, some nasty parasite might be attached to a spam email or message. Restrain yourself from clicking anything you don’t trust. You might accidentally set free a Trojan horse or another ransomware-type virus. In addition, infections get disguised as perfectly legitimate mail. Keep an eye our for malware and don’t overlook any potential threat. Another popular trick involves illegitimate torrents, websites and corrupted pop-ups. There’s no such thing as being too cautious online. Ransomware might also get bundled with unverified programs. Last but not least, these viruses often travel the Web with the help of Trojans. Check out the PC for more infections. There’s a great variety of malware distribution techniques and hackers are full of ideas. Make sure you always outwit crooks.
Why is Milarepa.lotos@aol.com dangerous?
The {Milarepa.lotos@aol.com}.CrySiS file extension only means one thing – that your data is unusable. It goes without saying some immensely important, precious information might get locked as well. As if that wasn’t enough, ransomware is trying to steal your money. The virus provides you payment instructions and promises a decryptor. This unique combination of symbols is supposed to unlock your data. The problem is, hackers aren’t famous for being honorable people. They are famous for scamming gullible PC users. Crooks are so focused on gaining illegitimate Bitcoins that your files simply don’t matter. You might cause an even bigger hassle if you pay the ransom. In the worst case scenario you’ll end up with your machine still compromised and your files still encrypted. In addition, a large sum of your money will be gone. Is that what you’re aiming for online? No? Then keep your Bitcoins. Don’t even consider contacting hackers because this is a battle you can’t win. What you can (and should) do is uninstall the ransomware as soon as possible. To do so manually, please follow our comprehensive removal guide down below.
Milarepa.lotos@aol.com Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Milarepa.lotos@aol.com Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Milarepa.lotos@aol.com encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Milarepa.lotos@aol.com encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



