Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Microsoft Decryptor Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
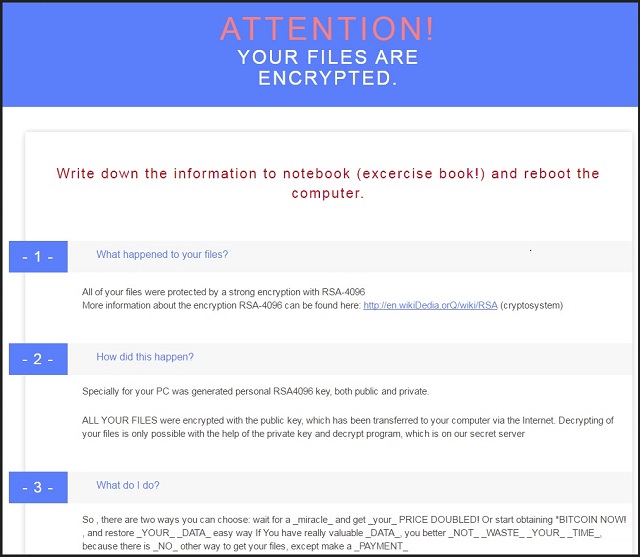
What happened to your files ?
All of your files were protected by a strong encryption with RSA4096
More information about the encryption keys using RSA4096 can be found here: hxxp://en.wikipedia.org/wiki/RSA_(cryptosystem)
How did this happen ?
!!! Specially for your PC was generated personal RSA4096 Key , both public and private.
!!! ALL YOUR FILES were encrypted with the public key, which has been transferred to your computer via the Internet.
!!! Decrypting of your files is only possible with the help of the private key and decrypt program , which is on our Secret Server
What do I do ?
So , there are two ways you can choose: wait for a _miracle_ and get _your_ PRICE DOUBLED! Or start obtaining *BITCOIN NOW! , and restore _YOUR_ _DATA_ easy way
If You have really valuable _DATA_, you better _NOT_ _WASTE_ _YOUR_ _TIME_, because there is _NO_ other way to get your files, except make a _PAYMENT_
Your personal ID:
For more specific instructions, please visit your personal home page, there are a few different addresses pointing to your page below:
1 – http://*************.onion.to
2 – http://*************.onion.city
If for some reasons the addresses are not availablweropie, follow these steps:
1 – Download and install tor-browser: hxxp://www.torproject.org/projects/torbrowser.html.en
2 – Video instruction: hxxps://www.youtube.com/watch?v=NQrUZdsw2hA
3 – After a successful installation, run the browser
4 – Type in the address bar: http://*************.onion
5 – Follow the instructions on the site
You’re stuck with ransomware. To say the least, that’s quite a problematic situation. Microsoft Decryptor Ransomware has been harassing PC users for just a couple of weeks now. However, it’s already proved to be a complete and absolute pest. This program is a classic member of the destructive ransomware family. It’s actually a new version of two parasites we’re already familiar with – CryptXXX and UltraCrypter. As you could imagine, hackers constantly keep working on ransomware-type infections. Crooks could be very hard-working people when it comes to creating malware. The problem is, their efforts might eventually cause you trouble. Take Microsoft Decryptor Ransomware, for example. It uses the asymmetric RSA-4096 encrypting algorithm in order to lock your personal files. Furthermore, this program infects all versions of Windows. It also has one more special trick up its sleeve – this virus doesn’t rename the target files. Most ransomware parasites add a bizarre appendix to the data they encrypt. Microsoft Decryptor, on the other hand, does no such thing. The way it works is, the virus creates a malicious executable. When this executable gets launched, problems begin. Microsoft Decryptor Ransomware firstly scans your PC so it could locate your private data. And it does. Pictures, music, MS Office documents, videos, etc. The virus basically searches for anything of value you might have stored on your machine. It pretty much goes without saying how dangerous that is, right? Whatever you have stored on your own computer falls victim to the ransomware. Once encryption is complete, your valuable information is no longer accessible and/or readable. The RSA-4096 cipher is highly complicated and effectively holds your data hostage. As mentioned, Microsoft Decryptor Ransomware employs an asymmetric algorithm. That means it uses two different keys. One is public (used to encrypt files) and one is private (used to decrypt files). Now, you need the private key if you want to restore your compromised files. As you could imagine, though, hackers are not willing to give you the key for free. Quite the opposite. Crooks demand 1.2 Bitcoins (about 800 USD!) for the luxury to unlock your infected files. Unless you pay instantly, the ransom reaches the dizzying 2.4 Bitcoin (almost 1600 USD!!). Make sure you don’t pay even a single cent. In order to learn why not, please keep on reading.
How did I get infected with?
All ransomware-type viruses travel the Web stealthily. No one would download such a pest voluntarily, right? These parasites pretend to be something they are not. For instance, Microsoft Decryptor Ransomware might have been attached to a spam message or some spam email. When you click open such a questionable message, you automatically give green light to the virus hidden behind it. Pay attention to anything you may come across in your inbox. Remember, the Web is infested with malware. You have to be cautious so hackers don’t fool you. This program also gets spread online in illegitimate software bundles or via fake torrents. Always take your time in the installation process, especially when the software comes bundled. And especially when it comes for free. Deleting a virus is much more troublesome than preventing infiltration in the first place.
Why is Microsoft Decryptor dangerous?
Microsoft Decryptor Ransomware drops README.txt, README.bmp, and README.html files during the encryption process. You will find these files in all folders that contain locked data. Obviously, hackers want you to be seeing them. That is because these files provide you payment instructions. And payment is what hackers are aiming for. Ransomware is nothing but a clever, original way for crooks to steal your money. They rely on the fact many people would give into panic/despair and, ultimately, pay the ransom demanded. You see, that is exactly what must be prevented. Instead of falling right into hackers’ trap, ignore their promises. Paying the money will not solve your problem. It will only allow crooks to balckmail you. Cyber criminals simply cannot be trusted. Therefore, restrain yourself from giving your money away. According to the ransom note, you’ll receive a decryption key in exchange for your money. Again, this is a lie. Hackers have no reason whatsoever to help you fix the issue or to restore your files. Microsoft Decryptor Ransomware has to be deleted on the spot. To do so manually, please follow our removal instructions.
Microsoft Decryptor Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Microsoft Decryptor Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Microsoft Decryptor encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Microsoft Decryptor encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



