Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Karmen Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
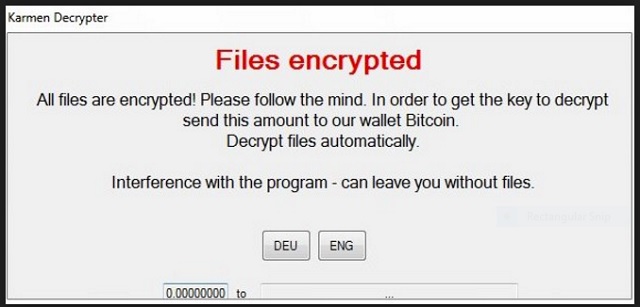
Files encrypted
All files are encrypted! Please follow the mind. In order to get the key to decrypt send this amount to our wallet Bitcoin.
Decrypt files automatically.
Interference with the program – can leave you without files.
Karmen is yet another ransomware infection that is terrorizing PC users around the world. It is demanding a lot of money to decrypt your locked files. We can say that Karmen uses a standard procedure to lock its victim’s files. It will sneak into your computer unnoticed, scan the HDD and encrypt all target files. Once all this is done, Karmen will display a ransom note which explains what have happened to your files and states the demanded sum for the decryption key. What is interesting about this particular virus is that it is quite popular among the underground society. In fact, it is advertised. DevBitox, a Russian-speaking user, has been promoting this ransomware as, imagine this, a user-friendly ransomware kid. This basically means that anyone with little programming knowledge, can buy the virus, modify it, and, of course, use it to blackmail their victims. The people who have bought the win-locker can make a lot of changes to the design of the virus. Therefore, it is possible that victims of this ransomware receive different ransom notes. Yet, the encryption algorithm used to lock their files remains the same. Karmen uses the AES encrypting algorithm which is one of the most complex possible. The virus is based on another open source ransomware project known as Hidden Tear. Security experts know about this project and work on decryption software. Hopefully, soon we will have tools that can remove this lock without having to pay the ransom.
How did I get infected with?
Karmen, just like many other ransomware viruses, relays on spam email campaigns to reach its victims. It may sound trivial, but let’s say it one more time. Do NOT open emails from strangers. The risk is too high. Before you open an email from an unknown sender, check their contacts. It is quite simple actually. You just need to enter the email address you have received a letter from into some search engine. If this address was used for shady business, someone must have complained online. Yet, this method is not flawless. New scams are created every day. And with them, new email accounts. So, double check everything. For example, if you receive a letter from a company or organization, go to their official website. There, under the contact section, you will find their authorized email address. Compare it with the one you have received an email from. If they don’t match, delete the spam message immediately. Scammers are very imaginative. They will do anything to lure you into downloading an attached file. Only your caution and diligence can save you from future troubles. Other ransomware distribution techniques involve corrupted links, fake update alerts and, in some cases, freeware bundling. Be vigilant. Your computer’s security is your responsibility and yours only.
Why is Karmen dangerous?
All ransomware infections are dangerous. Karmen is not an exception. Once on board, this virus will add its extension to your files. Your videos, pictures, documents, archives, etc. will be locked. You will be able to see their icons, yet, you won’t be able to open or use them. The ransomware ads the “.grt” suffix at the end of all encrypted files. Thus, if you have a file named music.jpg, the virus will rename it to music.jpg.gtr. You will see the .grt extension everywhere. To get rid of it, you must pay. We strongly advise against such actions. Keep in mind that you are dealing with cyber criminals. You cannot expect them to play fair. There are cases where the victims paid but did not receive anything. Even if you receive a decryption key, it may not work properly. Furthermore, if you send money to those people, you will sponsor their malicious business. On the other hand, if no one is paying, eventually, they will stop spreading such venomous parasites. One more thing. Whatever you decide, delete the virus first. If you decrypt your files, without removing the infection first, your newly restored files will be re-encrypted. Use a trustworthy anti-virus program to track this pest down. Of course, you can use our guide to do so manually. Don’t waste time and act!
Karmen Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Karmen Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Karmen encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Karmen encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



