Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Happylocker Ransomware?
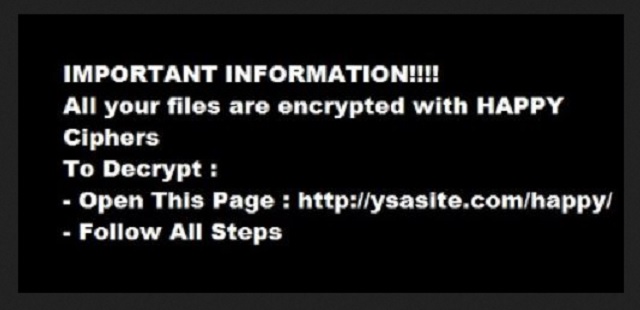
Readers recently started to report the following message being displayed when they boot their computer:
IMPORTANT INFORMATION! ! ! !
All your files are encrypted with HAPPY Ciphers
To Decrypt:
– Open This Page: hxxp://ysasute.com/happy
– Follow All Steps
Happylocker will make you feel many emotions. Anxiety. Sadness. Disappointment. Despair. However, happiness isn’t among them. Despite its smiley face, Happylocker is the least cheerful thing you could have downloaded. It’s part of the ransomware family. Those of you familiar with ransomware are probably cringing already. This virus belongs to the infamous Hidden Tear project. Very similar to the WildFire Locker Ransomware, it will lock your data. All your data. Being compatible with a huge variety of file formats, Happylocker is incredibly aggressive. How does this pest work? First of all, the parasite invades your once infection-free computer system. The installation itself happens behind your back. As you could imagine, most people don’t tend to download ransomware on purpose. Parasites don’t need your permission either. They travel the Web via stealth and deceit. To learn more about the infiltration methods malware uses, keep on reading. Once Happylocker gets installed, it scans your PC. This is how the virus locates your private files. Your very own files stored on your own computer. Do you think that’s fair? Happylocker uses the AES-256 encrypting algorithm. It quickly takes down all files on your machine. The virus adds a malicious appendix to the target data. Seeing the .happy extension is a crystal clear sign your files are now inaccessible. It’s also a sign that your happiness online is effectively ruined. Ransomware-type viruses utilize strong ciphers and deny you access to your data completely. If you thought that was bad, wait till you see what else Happylocker has in store. There’s a reason why file-encrypting infections are so dreaded. This program not only encrypts your files but also demands a ransom. Yes, we’re reaching ransomware’s main goal – to steal your money. It locks your files in order to trick you into paying a ransom. While encrypting your data, the parasite creates READ.jpg and READDDDDDD.txt files. Happylocker adds them to all folders that contain locked information. Obviously, those are quite a lot of folders. You will also notice that your desktop wallpaper has been modified too. This program is forcing its payment instructions on you practically all the time. According to the ransom notes, you must pay. Otherwise, you won’t be able to free your encrypted files. Or so the parasite claims. Crooks demand 0.1 Bitcoin. If you’re unfamiliar with online currency, 0.1 Bitcoin equals 73 dollars. Don’t even consider paying it.
How did I get infected with?
Perhaps the most commonly used technique involves spam emails. You might stumble across all sorts of infections in your inbox. It goes without saying that you shouldn’t open suspicious-looking emails. For instance, when you don’t personally know the sender, this might be a parasite. As mentioned already, malware is extremely sneaky and secretive. It often gets disguised as a legitimate email from shipping companies. Hence, be careful what you click open. Same piece of advice goes for third-party pop-ups and messages in social media. Remember, the Internet is full of infections. It is your responsibility and yours only to prevent infiltration. All you have to do is pay attention online. Stay away from random torrents, unverified websites and freeware/shareware bundles. Also, keep an eye out for fake program updates. This virus might have used the help of a Trojan or some exploit kit. Determining the exact tactic Happylocker used is a rather difficult task. What you should do is always be cautious when surfing the Web. Don’t let ransomware cause you a headache again.
Why is Happylocker dangerous?
Happylocker encrypts your precious files. It makes them unreadable, inaccessible and unusable. Your computer will be unable to recognize their brand new file format. As a result, you’ll be unable to use your own data. This infection could cause you serious damage in the blink of an eye. Keep a backup of your files to prevent such trouble. Also, tackle the parasite as soon as possible. The Happylocker Ransomware offers you a deal. It claims that if you make the payment, you’ll receive a special decryptor. As you can tell, that’s a lie. This program is aiming at your bank account so don’t let it scam you. Paying guarantees you absolutely nothing so be careful. Do not let crooks blackmail you and involve you in their nasty fraud. To delete the parasite manually, please follow our removal guide down below.
Happylocker Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Happylocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Happylocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Happylocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



