Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove HADES LOCKER Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
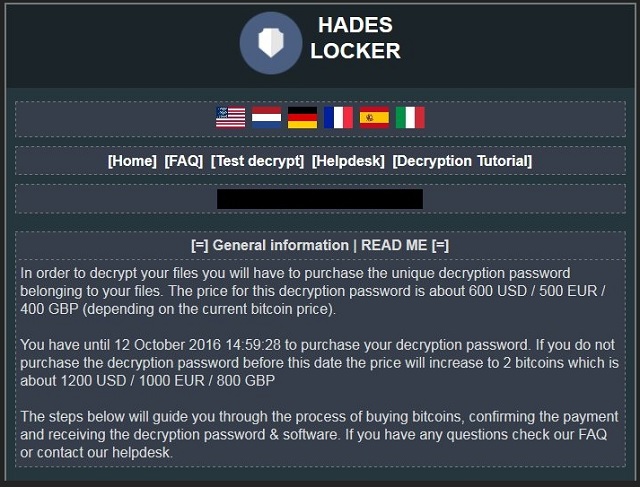
!! IMPORTANT INFORMATION !!
All your documents, photos, databases and other important files have been encrypted!
In order to decrypt your files you will have to buy the decryption password belonging to your files
There are 2 options to solve this problem
1. Format your hard disk and loose all your files for ever!
2. Pay to buy your decryption key. With this decryption key you
can decrypt your files and use them again like before.
To buy the decryption password you will have to visit our website. Pick a website below
http://pfmydcsjib.ru/3DE5BCD6057B470E
http://jdybchotfn.ru/3DE5BCD6057B470E
If these websites dont work you can visit our website on the TOR network follow the steps below to visit our TOR website.
1. Download and install the TOR browser: https://www.torproject.org/projects/torbrowser.html.en
2. After installation run the TOR browser and wait for initialization
3. Inside the TOR browser (just like a normal browser) navigate to n7457xrhg5kibr2c.onion/3DE5BCD6057B470E
HWID (personal identification ID): (redacted)
!! you have until (redacted), (redacted) to buy the decryption key or the price will double !!
Hades Locker belongs to the ransomware family. And, in case you didn’t know, that’s quite possibly the worst type of infection you can catch. Ransomware is a menace. It’s a plague on your PC, and a threat to your privacy. These infections prey on your naivety and hope. They rely on you to hope that money will fix everything. Don’t be naive. Don’t lie to yourself. Money won’t get rid of the infection. And, even if it succeeds in getting your files back, hold on to that joy for it will be brief. The infection can strike back at any given moment, and lock your data once more. When you’re stuck with a ransomware tool, either way you look at it, you lose. The game is rigged against you. So, cut your losses! Figure out your priorities, and answer the following question. Would you rather lose your files? Or, would you rather hand your private life to strangers? It’s either one or the other.
How did I get infected with?
Cyber threats, like the Hades Locker, are sneaky. They use slyness and subtlety to gain access. More often than not, they slither in via the old but gold means of invasion. In fact, they’re so sneaky in their deceit, you don’t even realize they snuck in. Oh, yes! The infections gain entry to your PC, and keep you oblivious to their presence. That may seem odd, considering they need your permission to install themselves. And, they certainly get it. They pretend to be a bogus update. Or, hide behind corrupted links. Or, sites. Or, spam email attachments. There are many ways they can deceive you. And, each one requires your approval. And, by extension, your carelessness. For, if you’re not careless, will you grant it? Save yourself a ton of troubles, and be extra vigilant and cautious. Don’t rush, and don’t skip the terms and conditions. Always be attentive, and thorough.
Why is HADES LOCKER dangerous?
Let’s get into how this particular ransomware plague works. The tool sneaks in undetected, and then gets to work. It follows its programming. Get in, encrypt everything, demand payment. Once inside your PC, Hades Locker loads http://ip-api.com/xml site. By doing so, it’s able to tell where you’re from. It gets your country, city, zip code, IP address. It gets your exact location. When it retains this information, it sends it to C&C server. And, the response you get from that server, is an infection. The nasty tool then implements a unique AES encryption key, thus, encrypting your data. All of it. Nothing escapes Hades Locker’s reach. When it finishes with the encryption process, it leaves a ransom note. It creates a ‘ReadMe’ file. That file contains instructions on what you’re expected to do, if you wish to free your data. No matter its requirements, demands, wishes, whatever, ignore them! It’s not worth falling in that rabbit hole. If you comply, you only make your situation worse. Compliance does NOT guarantee you ANYTHING. You can pay these people, and still have your data locked. The extortionists behind Hades Locker are unreliable and untrustworthy people. The program slithered into your system, and corrupted it. It encrypted your files. Then demanded monetary payment for their release. The individuals behind that programming are wicked. Do you honestly trust them to keep their word? And, even if they give you the decryption key you need, your files can still be lost. Why? Well, what if it’s the wrong one? What if it doesn’t work? Or, as was already mentioned, it works but the infection kicks in again tomorrow? Or, an hour later after decryption? Or, a single minute? There aren’t enough ways to stress this: you have NO guarantees! Don’t risk losing your personal and financial information to strangers! For, if you pay, you give access to just that to the people behind Hades Locker. Don’t comply. Don’t pay. Make the right choice. Say goodbye to your data. It’s replaceable. Privacy is not.
HADES LOCKER Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover HADES LOCKER Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with HADES LOCKER encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate HADES LOCKER encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



