Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Green Ray Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
Attention!!! To restore information email technical support send 3 encrypted files green_ray@india.com
OR
Attention! Your files are encrypted During the restoration, please mail green_ray@india.com Note! Attempt self-recovery destroy files
Green Ray is part of the extensive, and utterly dreadful, ransomware family. It’s a malicious and invasive infection, which exposes you to an abundance of dangers, and threatens to steal your private details, and use them for malicious purposes. The tool influences your system in arguably the worst possible way – it kidnaps your files and demands a ransom. That’s right. The nasty cyber threat targets your data. Once it slithers its way into your system, it hardly wastes time and goes to work. The dangerous cyber threat’s programming kicks in, and it attacks every single file you have stored on your computer. It encrypts everything via the RSA-2048 key (AES-CBC 256-bit encryption algorithm) and renders it unusable. The tool renames your files by adding the green_ray@india.com.xtbl extension, and once it slaps it on them, you can no longer access them. It backs you up into a corner. You can rename your pictures, music, videos, etc., as many times as you want but it won’t work. You won’t be able to free them from Green Ray’s captivity. Once the infection is done with the encryption process, it displays you a message, which clues you into your options. You can pay a ransom and regain control over your data, or not and lose them. It’s not much of a choice, is it? But here’s the deal. It’s a horrible idea to pay the file kidnappers. It’s the worst possible decision you can make because odds are, it WILL end badly, and you WILL regret it. Every potential outcome is negative on your part. So, follow experts’ advice as unpleasant and harsh as it may seem – discard your data. It’s not worth the risks! Don’t pay these people! It’s the right choice, albeit a hard one.
How did I get infected with?
Green Ray didn’t just make an appearance on your computer one day. Tools like it cannot choose to enter a system, and then magically pop up. They have to gain your permission to get in, which means they must ask for it. Yes, ransomware programs like this one, are bound to inquire you whether you agree to install them or not, and if you deny them – no admittance. But if the tools asked for your permission, how come its appearance surprised you? Why don’t you remember giving the green light to a dangerous infection? Well, it’s pretty straightforward. You were duped. The cyber threat doesn’t just openly come out, and ask permission. That leaves too much to chance. What if you say ‘no’? So, it goes the other way and uses trickery and deceit as it asks covertly. The dreaded application, like all others of its kind, is an utter master of deception. It employs slyness and subtlety to fool you into allowing it to enter. More often than not, it succeeds by using the old but gold methods of infiltration, like pretending to be a bogus system or program update. It can also hitch a ride with freeware or spam email attachments, or hide behind corrupted links or sites. If you wish to keep Green Ray, and others like it, away from your PC, try to be more cautious and vigilant! Infections prey on carelessness, so make sure not to provide it. Always do your due diligence and never rush! Gullibility and haste are your enemies.
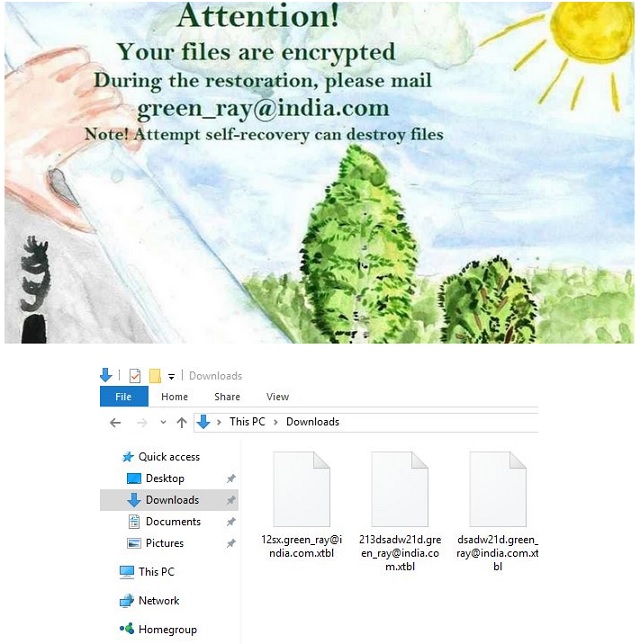
Why is Green Ray dangerous?
Green Ray slithers its way into your system via deception and finesse, and once it’s in, proceeds to corrupt it. The tool installs various files and alters your system registry so that its malicious code runs every single time you reboot your Windows. Thus, making sure there’s no escape. It employs the AES-265 and RSA encryption method to lock all of your files. And, make no mistake! It will undoubtedly get a hold of every single file you have stored on your PC, and render it inaccessible. It leaves no stone unturned. Once its encryption is complete, you’ll find your files with an added .green_ray@india.com.xtbl extension, and a message, which claims the only way to decrypt them is to pay a ransom. It’s usually in Bitcoin, and payment tends to be fruitless. By that, we mean that even if you comply with every requirement, which the kidnappers throw your way, there are NO guarantees that you’ll regain your files. As a matter of fact, if you pay up, you’ll only place yourself into a worse situation. How come? Well, to transfer the money required, you’ll have to provide these people with access to your personal and financial information. Do you think that’s wise? Hardly. So, don’t jeopardize your privacy for the tiny prospect of freeing your files. And, even if you do manage to decrypt your data with the key, sent by the captors, don’t get too thrilled about it. There’s nothing to stop the infection from kicking back in the very next day and encrypt everything, thus, sending you back to square one. Do what’s best for you, and protect your privacy! Do NOT comply with these strangers’ demands! Do NOT pay! Pick your private life over data! Data is replaceable. Privacy is not.
Green Ray Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Green Ray Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Green Ray encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Green Ray encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



