Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove CVLocker Ransomware?
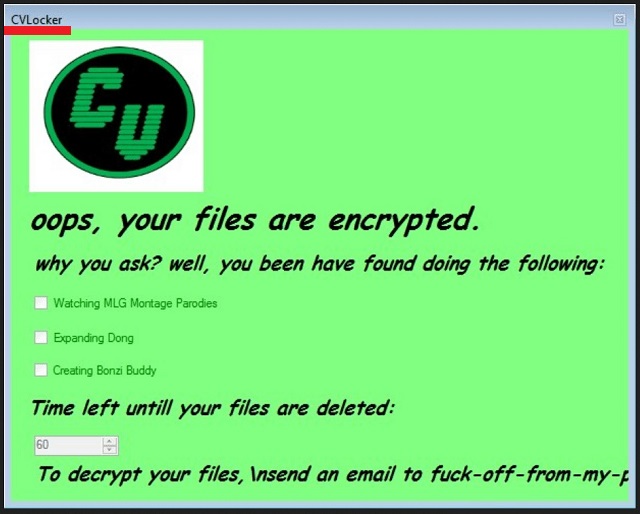
Readers recently started to report the following message being displayed when they boot their computer:
CVLocker
oops, your files are encrypted.
why you ask? well, you been have found doing the following:
– Watching MLG Montage Parodies
– Expanding Dong
– Creating Bonzi Buddy
Time left untill your files are deleted:
60
To decrypt your files, send an email to fuck-off-from-my-p…
The world is flooded with multiple dangerous ransomware viruses. People are talking about them with fear. Many ransomware imposters got an advantage of the situation. One such imposter is CVLocker Ransomware. This parasite is not a real ransomware virus. Even though the parasite can lock your screen, it is more like a practical joke than a real threat. The “virus” will lock your screen and display an obnoxious “ransom” note. It states that your files have been encrypted and gives you only 60 minutes to pay the demanded sum. At first glance, everything looks quite legit. Don’t panic. This is a lie. Check your files. They are alright. CVLocker states that your files will be deleted if you don’t pay the ransom. Yet, security experts have analyzed this parasite and confirmed that the “virus” cannot perform such operations. All this aside. The CVLocker “ransomware” should not be neglected. It locks your screen. It is an obstacle that is preventing you from using your device freely. Take its appearance as a sign. A sign that your security is lacking something essential. You were extremely lucky this time. You can remove CVLocker. Upgrade your security. The Internet is bursting with viruses. All of them are using the same strategies. Prepare yourself. You can prevent future infections!
How did I get infected with?
The CVLocker “Ransomware” can be categorized as a joke. Maybe a friend of yours have sent the “virus” to you? If not, there are still many techniques such parasites use to travel the web. Corrupted links, fake software updates and freeware bundling. These techniques are just the most commonly used ones. Be vigilant. The internet is bursting with parasites. You can never know where an infection may stake from. Therefore, if you receive an email from a stranger, check the sender’s contacts firs. Scammers tend to write on behalf of well-known organizations. If you receive such a letter, go to the organization’s official website. There, under the contact section. You can find their authorized email addresses. Compare them with the one you have received a message from. If they don’t match, delete the spam email immediately. The scammers can corrupt both the email attachments and the body of the letter itself. Proceed with caution. If a suspicious email contains links, don’t follow them. A corrupted link can download a virus without any visual indications. Opt for suspicious signs. The reliable companies and organizations would use your real name. Thus, if an email starts with “Dear Friend” or “Dear Customer,” there is a high possibility that this message is a scam. You are the one who is responsible for your computer’s health. Always do your due diligence.
Why is CVLocker dangerous?
The CVLocker “Ransomware” is an imposter. Yet, if you are not careful, it can steal your money. This application is designed to look authentically. It uses psychological tricks to make you act impulsively. The sixty-minutes timer, for example, is there to scare you. Nothing will happen. In the light of the recent ransomware attacks, many PC users did not check this virus and paid the price. Not with money, of course. The “ransomware” has no instructions on how the ransom is supposed to be paid. Its victims paid with their nerves and time. They got scared over nothing. Don’t become one of them. You can remove this intruder by yourself. Follow our guide or use a trustworthy anti-virus program. The CVLocker “ransomware” appears to be unfinished. If its developers manage to finish their creation, this parasite can “upgrade” itself and become a full-fledged virus. Remove it before it is too late. Furthermore, this infection managed to enter your computer. This means that your computer’s security is not efficient enough. This time you were lucky. Yet, dangerous viruses are using the same techniques to spread themselves. Fix the holes in your security. Install better anti-virus software. And most importantly, be more careful. You are the one and only one who is responsible for your computer’s security. Be always vigilant and doubting. Your caution can spare you tons of troubles!
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
CVLocker Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover CVLocker Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with CVLocker encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate CVLocker encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



