Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Crystalcrypt Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
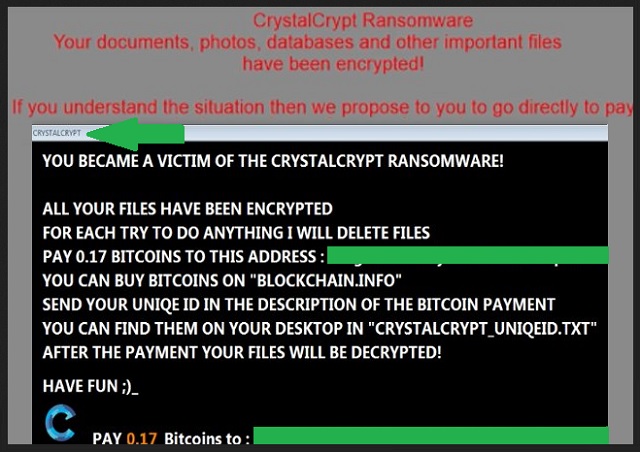
You became a victim of the crystalcrypt ransomware!
All your files have been encrypted
For each try to do anything I will delete files
Pay 0.17 Bitcoins on “Blockchain.info”
Send your uniqe ID in the description of the Bitcoin payment
You can find them on your desktop in “crystalcrypt_uniqeid.txt”
After the payment your files will be decrypted!
Have fun ;)_
PAY 0.17 Bitcoins to : [Bitcoin wallet account address]
The Crystalcrypt tool belongs to the most dreaded category of cyber threats. It’s a ransomware infection. And, you’ll rue the day it invaded your system. Once the program slithers its way in, it doesn’t take long before you notice its presence. One day, you come to find all your data locked. Pictures, music, videos, documents, everything. The tool encrypted it all, and now has the audacity to threaten and extort you. That’s the whole game-plan of ransomware. They target your files, take them hostage, and demand money for their release. In Crystalcrypt’s case, 0.17 Bitcoin. It may not seem like a lot, but don’t get fooled. Think of you paying the ransom as a stepping stone to bigger and worse things. You’re already in a lot of trouble. Given that you’re stuck with an infection that has your data kidnapped. But compliance only worsens your predicament. To meet the tool’s demands is to set yourself up for a bad time. Think about what paying cyber criminals entails. They get access to your private information. Your personal and financial details. What do you think happens after? Well, nothing good, for sure. Also, Crystalcrypt threatens you with the deletion of your data. It claims that if you try any “funny business,” the cyber kidnappers delete files. That’s a threat, they come through on. So, it’s good incentive to comply. But you must NOT do it. It’s a far better alternative to forsake your files than to try to get them back. You can’t win because the whole game is rigged against you. Don’t try. Discard your data. Protect your privacy.
How did I get infected with?
Crystalcrypt turns to the old but gold means of infiltration. When it comes to invasion, it sticks to the basic. The tool uses spam email attachments and freeware. Lurks behind corrupted pages and sites. Pretends to be a fake system or program update. Like, Adobe Flash Player or Java. In case, you didn’t spot it, there is a common denominator between the methods. They need your carelessness to succeed. If you apply caution when it’s needed, odds are, you can prevent ransomware invasions. But if you go the other way, don’t act surprised when you get greeted with the ransom note. Always choose caution over carelessness. Read through the terms and conditions when installing tools or updates. Make sure you are aware with what you allow into your system. Don’t leave your system’s fate to chance. Don’t jeopardize your privacy. You have nothing to gain from distraction, naivety, and haste. Vigilance is the way to go. Even a little extra attention can save you a ton of troubles.
Why is Crystalcrypt dangerous?
Crystalcrypt doesn’t take long to strike. Pretty soon after it settles, it takes over. The program encrypts your data, and solidifies its hold by adding a special extension. Say, you had a picture called ‘me.jpg.’ After the ransomware’s done, you see it as ‘me.jpg.BLOCKED.’ Once the extension is in place, the tool offers you only one way out. Pay the ransom. If you don’t, you lose them all. It’s a simple choice, and we’re here to make it simpler! Do not pay! There aren’t enough ways to stress what a horrendous mistake it would be to comply. Think about what happens after payment. You wait for cyber criminals to keep their end of the bargain. Does anything about these extortionists scream ‘trustworthy’ to you? Don’t be naive! They will not go through with their promise! These are people who unleashed a malicious infection onto web users. They will double-cross you. And, what’s your best-case scenario? You pay, and receive the needed decryption key, which they promised? You apply it, and your files are no longer locked. But then what? The ransomware remains on your PC. What if it encrypts everything again, five minutes after decryption? It can do that. But even worse than the looming threat of getting sent back to square one, is the privacy risk. As we explained already, to pay is to allow access to your personal and financial details. And, to extortionists no less. That’s not a good idea, and it does not end well. You have ZERO guarantees when it comes to ransomware. And, every scenario you face ends with you losing. Don’t gamble. It’s not worth it. Your files are not worth it. Accept your defeat, and cut your losses.
Crystalcrypt Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Crystalcrypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Crystalcrypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Crystalcrypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



