Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
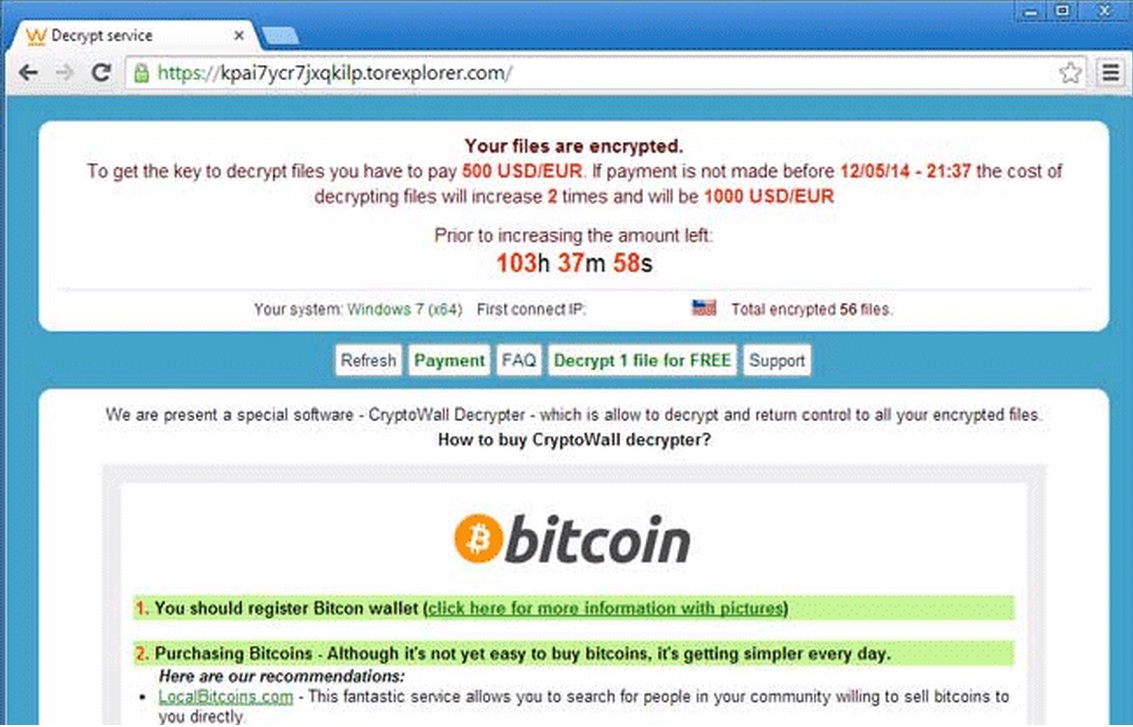
CryptoWall is a very scary computer program that encrypts your personal files and asks for ransom. That is why it is being classified as ransomware. Usually, people get infected with it without even noticing what they did wrong. This particular virus is spreading through windows vulnerabilities and utilization of sophisticated social engineering tricks to make you willingly infect yourself. It is hard to notice the virus until it is too late. Once the ransomware does its evil, it will encrypt your files and start a countdown as shown in the screenshot above. It will ask you to pay money in order to decrypt your files. As the time passes by the price will increase. If you don’t pay the money after the countdown ends, a new count down will start. It will claim that if you do not pay the ransom in one month, your files will be permanently deleted. Please, have in mind that even if you pay the ransom, there is no guarantee that you can decrypt and use your files again.
How to Remove Cryptowal Manually?
STEP 1: Start Your Computer into Safe Mode with Command Prompt
- Make sure you do not have any floppy disks, CDs, and DVDs inserted in your computer
- Restart the computer
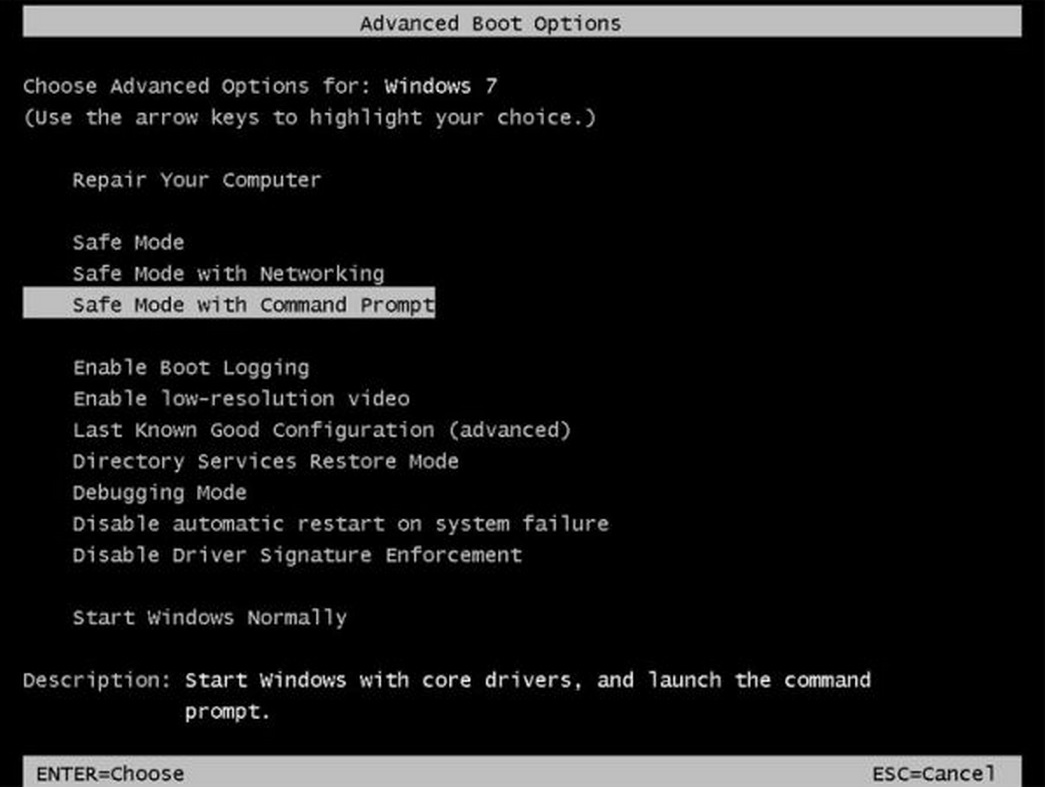
- When you see a table, start tapping the F8 key every second until you enter the Advanced Boot Options

For Windows 8, press the Windows key + C, and then click Settings. Click Power, hold Shift Key and click Restart, then click on Troubleshoot and select Advanced options. In the Advanced Options screen, choose Startup Settings, then hit Restart. When in safe mode press 6 on your keyboard to Enable Safe Mode with Command Prompt.
- If you are using Windows XP, Vista or 7 in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Command Prompt , and then press ENTER.
Once you see the administrator console you need to type: explorer.exe as shown in the picture below:
Once your desktop icons come in place you will be able to use windows programs again.
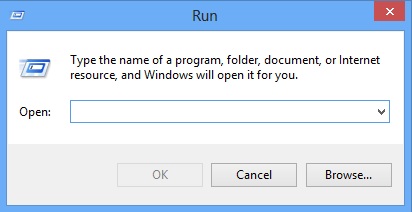
STEP 2: Modify Registry
Simultaneously press the Windows Logo Button and then “R” to open the Run Command
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Type “regedit” in the box to open Registry Editor, you can learn how to safely modify your windows registry from here.
After that, locate and remove the registry entries of the ransomware listed below.
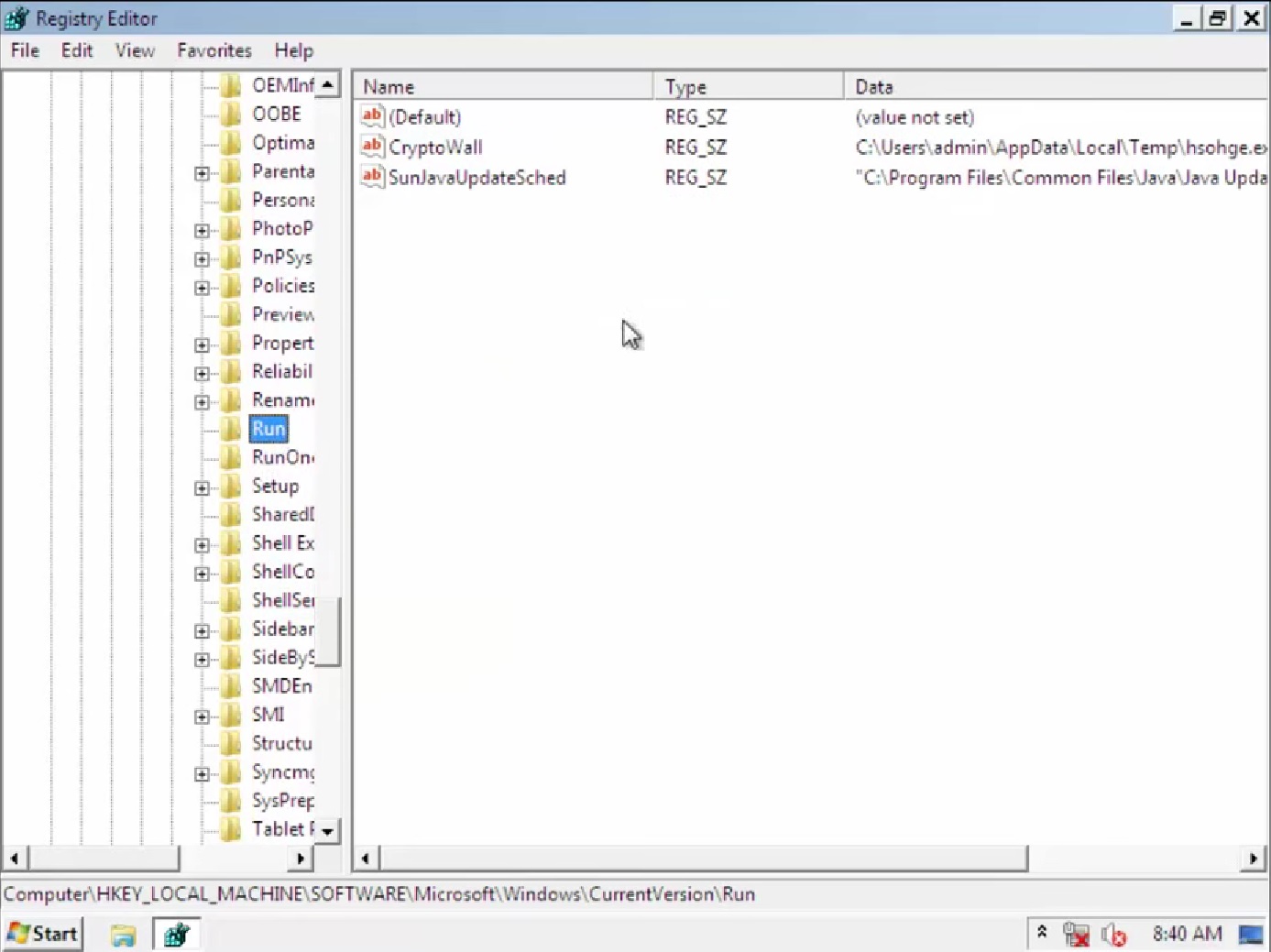
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Cryptowall
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\msmpeng.exe “Debugger” = ‘svchost.exe’
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\CryptoWall Decrypter
HKEY_LOCAL_MACHINE\SOFTWARE\CryptoWall Decrypter
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SystemRestore “DisableSR ” = ’1′
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ekrn.exe “Debugger” = ‘svchost.exe’
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings “WarnOnHTTPSToHTTPRedirect” = ’0′
HKEY_CURRENT_USER\Software\CryptoWall Decrypter
Delete the files located in your TEMP directory
Restart Windows.
STEP 3: Recover Cryptowall Encrypted Files
There are several methods you can use, however nothing is guaranteed.
Method 1 to restore the encrypted by CryptoWall files by hand:
You can try to use the built in feature of Windows called System Restore. By default the system restore feature is automatically turned on. Windows creates shadow copy snapshots that contain older copies since the system restore was performed. These snapshots will let us to recover any previous version of your file, although it will not be the latest one, still you can recover some important information. Please note, that Shadow Volume Copies are only available with Windows XP SP2, Vista, Windows 7 and Windows 8.
Method 2 to partially restore the encrypted by CryptoWall files by using Microsoft Office junk files:
Basically you need to show your hidden files. The fastest way to do that is:
- Open Folder Options by clicking the Start button .
- In the search box type “FOLDER OPTIONS”.
- Select View TAB
- Under Advanced settings, find Show hidden files and folders and select it and then click OK.
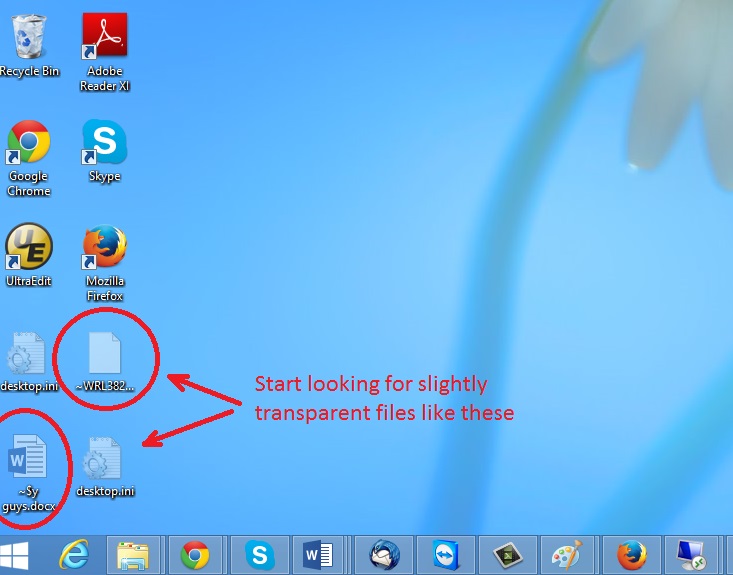
In the picture above I marked two hidden files. You are interested in every file that looks like ~WRL382.tmp This is actually a Microsoft office junk file that contains the previous version of the Word document itself. The Cryptowall parasite will not encrypt these files. The name of the file will be unknown, but you can recover a lot of lost documents using this method. This can be utilized for Microsoft Word and Microsoft Excel. In addition you can try to match the file sizes in order to figure out what is what and eventually you can restore a slightly older original document. In the picture on the left there is another method you can locate the files in question.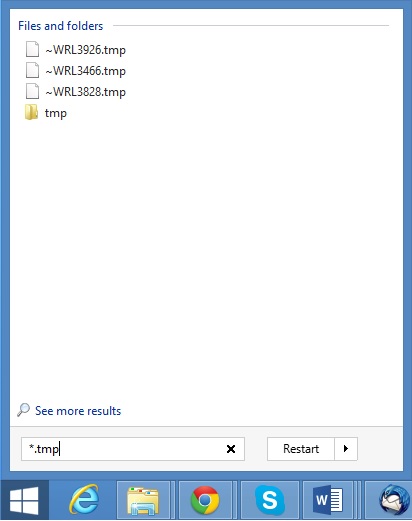 All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.
All you have to do is to hit the start button and type *.tmp. You will be presented a list of all the temp files located in your computer. The next thing is to open them one by one with Microsoft Word/Excel and recover the lost information, by saving it to another place. You can do that, by opening a new instance of MS Word/Excel, trough the file menu select open and then navigate to the location of the TMP file.