Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Booster.exe CPU Miner Virus. The step by step removal works for every version of Microsoft Windows.
Today’s article is focused on a vicious Trojan horse. In fact, the Web is currently infested with members of the Trojan family. Hackers seem to be paying extra attention to these infections which, of course, is bad news. Trojan horses are among the most aggressive and troublesome kinds of malware. That means you’re stuck with a particularly harmful parasite. Tackle the virus as soon as you encounter its presence on board. You have absolutely no reason to be hesitating. Booster.exe CPU Miner attempts to help its developers gain profit. To do so, this program mines digital currency. In other words, hackers are currently using your computer to make money. Are you willing to participate in their trickery? Are you going to become a sponsor of greedy cyber criminals? If the answer to these questions is no, which it should be, remove the Trojan ASAP. This parasite gets activated immediately after its installation is complete. For starters, it makes changes in your system registry. Some of your system files get modified and others get straight out damaged. As a result, you’ll notice that your computer behaves differently. The machine underperforms, it crashes and freezes. Even the most simple tasks now take a lot of time. You may come across the Blue Screen of Death too. Long story short, using your machine is no longer enjoyable now that it is infected. The Trojan efficiently uses your PC’s resources and harasses you on a daily basis. Your PC speed is slowed to a crawl which usually indicates the presence of a virus. In the future, know that such a sudden change in the PC speed is one of the few tell-tale signs that a Trojan is on board. Unless you pay attention to the way your machine behaves, you won’t be able to tackle the infection on time. And it is key for your safety to get rid of this parasite on the spot. The virus also spies on your personal details such as browsing history, usernames, passwords. It might mess with some of your browser settings as well. Last but not least, this pest may grant hackers remote control over your entire device. Don’t underestimate the threat; Booster.exe CPU Miner has to go.

How did I get infected with?
Trojans are famous for using fake emails to get spread online. Hence, the most likely explanation is that you opened some fake email or message that hackers sent to you. Know that crooks present their infections as perfectly harmless job applications or other documents. Watch out for parasites and be careful what you click open. It only takes one single wrong move to compromise your security. On the other hand, removing malware may take some long hours. Delete the questionable email-attachments you may receive, especially if you don’t know the sender. This simple piece of advice could protect you from sneaky Trojan horses so be cautious. Another popular infiltration method involves fake software updates or bogus torrents. Stay away from unverified websites as well as illegitimate programs. Trojans may also get attached to some freeware or shareware bundle so never rush when installing bundles. Instead, opt for the Custom option in the Setup Wizard and go through all programs thoroughly. Your care will pay off in the long run.
Why is this dangerous?
The Trojan causes a complete mess on your computer system. As mentioned, it makes plenty of unauthorized changes in your PC settings. Also, some of your browser settings may get modified. Don’t be surprised if you stumble across a pile of random, stubborn, useless pop-up ads. After all, hackers are now using your computer for their own purposes. They might change your default search engine or homepage thus bringing along sponsored pop-up ads. Avoid clicking any of these commercials, product deals or program updates. These get generated by a virus which means they are dangerous by default. Booster.exe CPU Miner could lead to some serious privacy issues as well. The parasite collects about as much sensitive data as possible. That may include your bank account information as well as online credentials. Thus, the Trojan could involve you in some financial scam or even identity theft. To delete it manually, please follow our detailed removal guide down below.
Manual Booster.exe CPU Miner Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The Booster.exe CPU Miner infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Booster.exe CPU Miner infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down Booster.exe CPU Miner related processes in the computer memory
STEP 2: Locate Booster.exe CPU Miner startup location
STEP 3: Delete Booster.exe CPU Miner traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Booster.exe CPU Miner related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Booster.exe CPU Miner startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Booster.exe CPU Miner virus from the windows registry
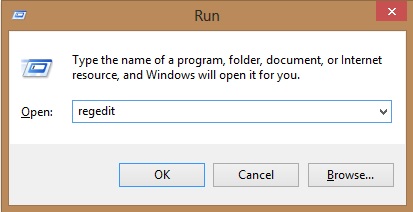
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
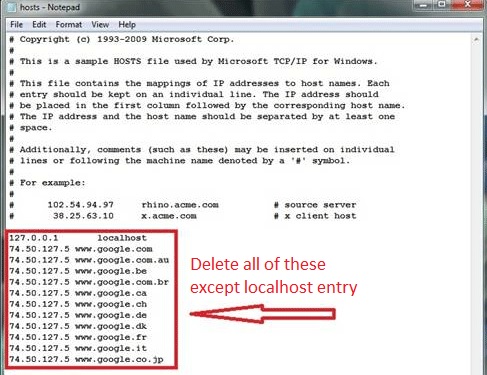
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Booster.exe CPU Miner
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Booster.exe CPU Miner, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Booster.exe CPU Miner Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.