Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove BlackSheep Ransomware?
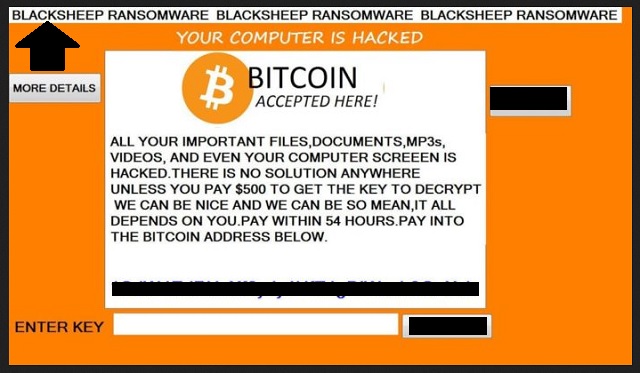
Readers recently started to report the following message being displayed when they boot their computer:
BLACKSHEEP RANSOMWARE BLACKSHEEP RANSOMWARE BLACKSHEEP RANSOMWARE
YOUR COMPUTER IS HACKED
ALL YOUR IMPORTANT FILES, DOCUMENTS, MP3s, VIDEOS, AND EVEN YOUR COMPUTER SCREEEN IS HACKED. THERE IS NO SOLUTION ANYWHERE UNLESS YOU PAY $500 TO GET THE KEY TO DECRYPT WE CAN BE NICE AND WE CAN BE SO MEAN, IT ALL DEPENDS ON YOU. PAY WITHIN 54 HOURS. PAY INTO THE BITCOIN ADDRESS BELOW.
1CdW4EdRUeXf6ydy4HfZ4gDiWcxb9QnXxb
ENTER KEY:
The Internet is definitely not a safe place. One of the latest parasites traveling this dangerous zone is a cryptovirus named BlackSheep Ransomware. The creators of the parasite are imaginative. It isn’t just the interesting name they chose, it is the way they designed their creation. While BlackSheep is caring the encryption process, it will display a fake Windows Update screen. If this is not brilliant, we don’t know what is. By displaying this message, the virus ensures that you are not going to use your PC. Thus, it can use all of your computer’s resources. The encryption will be completed much faster. Plus, you will not get a chance to interrupt the malicious process. BlackSheep Ransomware adds the .666 file extension at the and of all encrypted files. Thus, if you have a file named example .jpeg, the virus will rename it to example.jpeg.666. Once all target files are successfully locked, BlackSheep will display its ransom note. It states that all your files are encrypted and that you have only 52 hours to pay a $500 worth of Bitcoin as a ransom. Once the time is over, the hackers threat to become mean to you. Don’t panic! And most importantly, don’t pay the ransom. The hackers are using psychological tricks to make you act impulsively. We have some great news for you. Security experts say that this ransomware is decryptable. There is no decryption tool yet, but they are working on it.
How did I get infected with?
BlackSheep Ransomware uses not one, but many techniques to spread itself. Torrents, fakes software updates and corrupted links are just the tip of the iceberg. Yet, the most commonly used distribution method is via spam emails. Yes, the good old spam emails. They are still the main cause of virus infections. You’ve probably heard it a thousand times, you will read it one more time. Don’t open emails from strangers. Scammers are quite imaginative. They write on behalf of well-known organizations and companies. If you receive such a message, proceed with caution. Check the sender’s contacts before opening the letter. You can do so by entering the questionable email address into some search engine. If it was used for shady business, someone must have complained online. Unfortunately, this method is not flawless. New email addresses are created every day. If you are part of the first wave of spam messages, there may not be any evidence online. Therefore, double-check the sender. If the questionable email pretends to be sent from an organization, visit that organization’s official website. There you will be able to see their authorized email address. Compare them with the one you have received a message from. If they don’t match, you know what to do. Delete the spam letter immediately. Only your caution can prevent infections.
Why is BlackSheep dangerous?
BlackSheep Ransomware is extremely dangerous. It has locked your personal files and demands a ransom. It is obnoxious and irritating. You must not, under any circumstances, pay that ransom. Keep In mind that you are dealing with cyber criminals. You can’t expect them to play fair. They will double-cross you for sure. Hackers tend to ignore the victims once the ransom is paid. Furthermore, even if you pay, they may continue to blackmail you. They will demand more and more money. Don’t contact these people. No one can guarantee you that they will keep their part of the deal. Besides, they promised to send you a description key. No one mentioned anything about a working key. Such cases exist. Victims paid but the decryption tool worked only partially. It is not worth the risk. We must also mention that if you use your corrupted PC to pay the ransom, BlackSheep will record your paying details. Unfortunately, this ransomware deletes all System Shadow Copies. This makes the file-restore a bit more complicated. Yet, if you have a system backup saved on an external device, you can use it to restore your files for free. Be warned! Neither the file-restore nor the decryption key can remove the virus. Whatever you decide to do, clean your PC first. Otherwise, your newly restored files will be re-encrypted. As for external memory, it will get infected too. Be smart! Use a trustworthy anti-virus program to remove this parasite.
BlackSheep Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover BlackSheep Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with BlackSheep encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate BlackSheep encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



