Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove !SATANA! Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
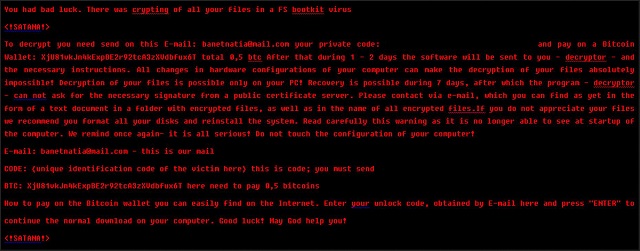
You had bad luck. There was crypting of all your files in a FS bootkit virus
SATANA!
To decrypt you need send on this E-mail: banetnatia@mail.com your private code: {unique identification of the victim here} and pay on a Bitcoin Wallet: XjU81vkJn4kExpBE2r92tcA3zXVdbfux6T total 0,5 btc After that during 1 – 2 days the software will be sent to you – decryptor – and the necessary instructions. All changes in hardware configurations of your computer can make the decryption of your files absolutely impossible! Decryption of your files is possible only on your PC! Recovery is possible during 7 days, after which the program – decryptor – can not ask for the necessary signature from a public certificate server. Please contact via e-mail, which you can find as yet in the form of a text document in a folder with encrypted files, as well as in the name of all encrypted files.If you do not appreciate your files we recommend you format all your disks and reinstall the system. Read carefully this warning as it is no longer able to see at startup of the computer. We remind once again- it is all serious! Do not touch the configuration of your computer!
E-mail: banetnatia@mail.com – this is our mail
CODE: {unique identification code of the victim here} this is code; you must send
BTC: XjU81vkJn4kExpBE2r92tcA3zXVdbfux6T here need to pay 0,5 bitcoins
How to pay on the Bitcoin wallet you can easily find on the Internet. Enter your unlock code, obtained by E-mail here and press “ENTER” to
continue the normal download on your computer. Good luck! May God help you!
SATANA!
What is the one thing that is more dreaded than Petya Ransomware and MISCHA Ransomware? A combination of both. Meet !SATANA!. This parasite was only discovered last week but it’s already proven itself to be a complete and utter pest. You had bad luck, states the virus. However, you didn’t just have bad luck. You had extremely, incredibly bad luck. Ransomware is the worst type of program you could have possibly stumbled across online. And yes, you’ve managed to install it. !SATANA! is a classic representative of the ransomware family which means it’s devastating. As if you thought otherwise. The way this thing works is, it firstly scans your PC. Thanks to this scan, !SATANA! locates all your personal files which it will then encrypt. This is where the really nasty part begins. !SATANA! utilizes a complicated encrypting algorithm that turns your data into unusable gibberish. To be more precise, this program uses a mix of RSA and AES ciphers. That makes the encryption twice as effective. The parasite renames your files and adds a malicious extension to them. The infected data now looks like that – Gricakova@techemail.com_[original file name]. As you could imagine, anything !SATANA! encrypts becomes inaccessible. That includes music, MS Office documents, pictures, videos, etc. Whatever of value you have stored on your PC falls victim to the parasite and, unfortunately, nothing is safe. Obviously, not many people would remain calm seeing such a sudden, unauthorized modification. Panicking isn’t going to help you, though. On the other hand, it might cost you money. While encrypting your private information, the virus also drops detailed payment instructions. You’ll come across a !satana!.txt file in all folders that contain encrypted data. Those are indeed a lot of folders. According to this aggravating message, you have to contact hackers in order to free your files. Crooks provide you a whole bunch of email addresses – ryanqw31@gmail.com, matusik11@techemail.com, rayankirr@gmail.com, Gricakova@techemail.com, Sarah_G@ausi.com, megrela777@gmail.com. Stay away from all of them. The thing with ransomware is, it’s aiming directly at your bank account. You see, its entire mechanism is actually quite clever. This infection locks your precious files and leaves you confused and worried. Then it starts forcing its ransom notes on you. !SATANA! demands 0.5 Bitcoins (about 335 USD) which is not a small amount of money. Furthermore, unless you make the payment in the next 7 days, your files will be gone.
How did I get infected with?
Ransomware gets spread online the exact same way all other infections do. For example, !SATANA! might have been attached to some spam email or a spam message. Keep in mind that social networks might jeopardize your safety if you’re not careful enough. Therefore, next time you notice something suspicious in your inbox, don’t hesitate to delete in on the spot. Also, the virus often travels the Web via corrupted torrents or illegitimate websites. Another plausible scenario is that !SATANA! entered your machine with the help of a Trojan. As you can see, ransomware applies numerous techniques to get installed. It’s important to watch out for infections constantly. This nuisance may also get attached to a freeware or shareware bundle or pretend to be a program update. Trust us on this one, ransomware is not something you want to deal it. Thus, prevent virus installation on time and take care of your PC.
Why is !SATANA! dangerous?
!SATANA! locks out your access to your very own files. Then it has the impudence to ask for money so it could “release” your infected data. Why the quotation marks, you may ask? Because this is a PC virus we’re talking about. It was developed by greedy cyber criminals to serve one purpose only – steal your money. You could pay the entire ransom and still receive nothing in exchange because that’s how ransomware works. This is an attempt for a scam. !SATANA! Is trying to blackmail you which is precisely what you shouldn’t allow. Don’t give into your anxiety and don’t even for a second believe the parasite’s ransom messages. The asymmetric encryption algorithm this pest uses is indeed very dangerous. However, paying the ransom would only worsen your situation. At the least, hackers will receive your money and get access to your bank account information. Are you willing to become a sponsor of hackers’ malicious business? No? Then don’t let them manipulate you. Take action instead and delete this virulent infection. To do so manually, please follow the detailed removal guide you’ll find down below.
!SATANA! Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover !SATANA! Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with !SATANA! encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate !SATANA! encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



