Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove IcedID Virus. The step by step removal works for every version of Microsoft Windows.
IcedID is the name of a problematic PC infection. This Trojan horse causes numerous issues and exposes you to various threats. It is a classic member of the nasty Trojan family so there is no doubt IcedID is dangerous. As soon as this pest gets installed, trouble starts right away. The Trojan modifies some of your default computer settings. By altering your system registry, IcedID practically takes over. Neither your permission nor consent was in any way involved in the parasite’s modifications. After all, we’re talking about a devious creation of cyber criminals. Trojans don’t get developed to help you surf the Internet. They solely exist so hackers could gain questionable profit. How does IcedID help crooks make money? The parasite messes with your default, important PC settings. It damages some system files and changes others. As you could imagine, such modifications cannot remain of no consequence. On the contrary, IcedID makes it impossible for you to use some programs. This parasite also causes a poor PC performance. Now, it is immensely important that you pay attention to the way your computer behaves. The moment you realize your device starts crashing or freezing, take action. Chances are, your PC has fallen victim to a dangerous infection if it underperforms. Bear in mind that Trojans are particularly sneaky. It may take you a good while to spot the virus. Of course, IcedID will be using all this time to wreak havoc. The parasite may also alter some of your browser settings. For example, you might notice modifications in your search engine or homepage. Don’t be surprised when the virus redirects you to random websites either. If you get redirected, you could easily land on malicious pages full of parasites. Instead of overlooking the threat, get rid of the parasite. Both your safety and privacy are at stake so don’t hesitate. The Trojan must be deleted for good.

How did I get infected with?
Trojans mainly get distributed online via fake emails and messages. If you do receive something suspicious-looking in your inbox, stay away from it. Hackers often send malware disguised as some job application or another harmless document. Once you open the fake email-attachment, you set the parasite free. To prevent malware infiltration, be careful what you click open. Cyber viruses also travel the Web via bogus torrents, corrupted third-party pop-ups or fake program updates. The Trojan might have been attached to some software bundle as well. You see, compromising your safety is a very simple task. Unless you’re cautious when surfing the Internet, you could download all sorts of malware. Do yourself a favor and watch out for potential intruders. Protecting your machine from infections is your job and yours only. There are plenty of harmful programs out there so be attentive. It only takes one wrong move to install viruses. Getting rid of them, though, takes much more.
Why is this dangerous?
There are plenty of malicious traits Trojans exhibit. As mentioned already, IcedID follows the typical Trojan pattern. After installation, the virus makes unauthorized changes in your default PC settings. That means hacker take advantage of your very own computer and its resources. IcedID also serves as a back door to more viruses. Trojans are famous for helping ransomware get downloaded. Keeping IcedID on board may worsen your situation so we recommend that you remove this pest ASAP. You certainly do not want to get stuck with a file-encrypting pest too. Therefore, uninstall the dreaded Trojan horse before it gets out of hand. This infection might modify some browser settings and bring along sponsored pop-up ads as well. Keep in mind many of the commercials are corrupted. In other words, you may get redirected to dangerous websites and compromise your PC further. To save yourself the hassle these pop-ups may cause, avoid them. Trusting any web link generated by a virus would be a mistake and you know it. Last but not least, IcedID jeopardizes your privacy and steals sensitive data. The Trojan could even attempt to involve you in some financial scam or identity theft. It could grant hackers remote control over your device as well. To delete it manually, please follow our detailed removal guide down below.
Manual IcedID Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
The IcedID infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the IcedID infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
STEP 1: Track down IcedID related processes in the computer memory
STEP 2: Locate IcedID startup location
STEP 3: Delete IcedID traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down IcedID related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate IcedID startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean IcedID virus from the windows registry
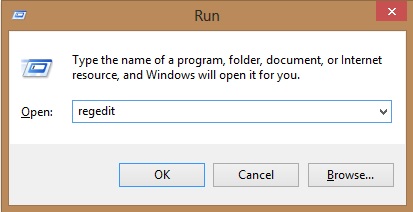
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
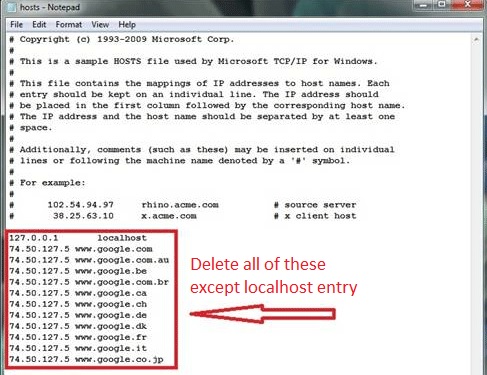
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by IcedID
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for IcedID, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove IcedID Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.