Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Hitler Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
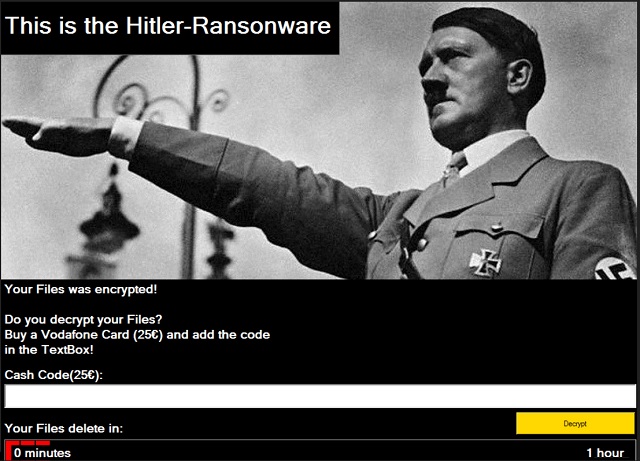
This is the Hitler-Ransomware
Your Files was encrypted!
Do you decrypt your files?
Buy Vodafone Card (25EUR) and add the code
in the TextBox!
Cache Code(25EUR):
[text field]
Your Files delete in:
[countdown timer for 1 hour]
Hitler isn’t a name you would associate with PC viruses, is it? Hackers’ main source of inspiration seems to be Greek mythology. We’ve come across infections named Cerber, Zeus, VenusLocker, etc. Of course, there are also Juicy Lemon and TrumpKard. Hence, when it comes to parasites’ names, we’ve pretty much seen it all. This particular infection is just the nth ransomware-type program with a weird name. Hitler. Sounds quite intimidating, don’t you think? This infection was actually designed to make you feel anxious and afraid. However, there’s nothing to be afraid of. If you take quick measures and follow our removal steps, Hitler will be defeated yet again. This is just a sneaky, deceptive PC virus which aims at your bank account. Do the right thing concerning your safety and don’t panic. All you have to do is tackle the parasite. Obviously, the sooner you do so, the better. Now, how does the Hitler Ransomware work? First of all, this isn’t the typical ransomware infection. Unlike most programs of this kind, Hitler doesn’t encrypt files. It does lie and claim the opposite, though. Hitler Ransomware locks your PC screen. The virus displays a black-and-white picture of Hitler himself accompanied by a ransom message. According to that message, “your files was encrypted”. The lock screen also refers to the virus as “Hitler-Ransonware”. Hackers seem to be paying less and less attention to grammar and spelling rules. What’s even more terrifying than hackers’ English is the fact crooks threaten you. Yes, they have also added a timer to the lock screen. Their offer is very simple – you pay the money demanded or you wait till your files get deleted. When the time (one hour) is up, Hitler Ransomware deletes your data. This ransom is a lot smaller than what we’re used to seeing. Hackers only want 25 Euro (about 28 USD). The usual ransom varies between 0.5 Bitcoin (almost 300 USD) and 1.5 Bitcoin (almost 900 USD). Do you see the difference? What all ransom-type programs have in common, though, is that they try to blackmail you. No matter what the exact sum is, hackers are trying to steal it. Ransomware is nothing but a clever attempt for a financial fraud. Don’t even consider paying the ransom. You’d become a sponsor of hackers’ malicious business. Ransomware is considered to be one of the most harmful programs online for a reason. Don’t underestimate the threat this parasite poses and uninstall it.
How did I get infected with?
You probably clicked something open in your inbox that you should have ignored. Ransomware usually travels the Web as a spam email or message. It often gets disguised as a job application, for example, or other legitimate mail. You must be very careful unless you’re willing to compromise your PC again. Delete what you don’t trust instead of opening it. Another popular method is freeware and shareware bundling. When installing program packages, avoid unverified websites. Also, take your time to check out the bundle thoroughly before installation. Always remember that you have to be attentive online. There’s no such thing as being too cautious so make no mistake. In addition, ransomware travels the Web with the help of Trojans sometimes. That means Hitler Ransomware may not be the only infection currently on board. Last but not least, stay away from suspicious-looking ads and illegitimate torrents. Restrain yourself from clicking anything unreliable because the Web is infested with malware. It is your job and yours only to prevent virus installation.
Why is Hitler dangerous?
Yes, Hitler is dangerous. The infamous Hitler Ransomware is perfectly capable of wreaking havoc. As mentioned, this program doesn’t encrypt personal data. It removes all file extensions and plays mind games with you. You’re supposed to use a Vodafone card code in order to make the payment. Unless you pay the ransom on time, Hitler Ransomware will delete all files in the %UserProfile% folder. When the time for payment is up, this virus crashes your PC. Then it reboots the system and destroys all your private data. We suspect that the nasty Hitler Ransomware might get improved thus becoming even more worrisome. Get rid of it ASAP and protect your computer in the future. Paying the ransom isn’t an option. This program’s greedy developers are only interested in their illegal revenue. There is no guarantee they would follow the rules. To sum up, Hitler Ransomware is indeed quite a pest. In order to delete it, please follow our comprehensive removal guide down below.
Hitler Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Hitler Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Hitler encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Hitler encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



