Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Donald Trump Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
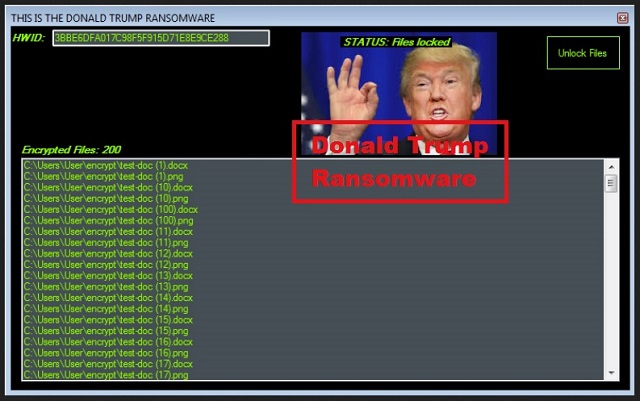
“This is the Donald Trump Ransomware. STATUS: Files locked.”
Turning on your computer, and seeing the face of Donald Trump is hardly something you wished for. But, here it is! The Donald, as American media loves to call him! Right in front of your eyes! There, in the top right corner of a picture on your Desktop. And, below his face, you see a message you dread. “This is the Donald Trump Ransomware. STATUS: Files locked.” It’s safe to assume that’s not how you were hoping to start the day. We can’t say we’re surprised the name caught on with cyber criminals. It was bound to happen! After all, according to some, it’s just plain perfect! You have an application that slithers its way into a place where it’s not wanted, and just makes a mess of things! Much like, Donald’s getting into politics. One day, it’s just there, and you can’t seem to get rid of it. You’re stuck. The nasty ransomware is an utter menace. Well, arguably, not as big of a menace as Donald Trump’s presidential candidacy, but still. The infection is a plague on your PC. After it slithers its way in, it encrypts all your files, and demands a ransom. You have to pay up to see your files again. Don’t mistake that for the tool’s removal. If you pay the ransom, you don’t get rid of the ransomware. You get the decryption key to free your files. The infection promises to give it to you, and why would it lie? In case, you can’t tell, that’s sarcasm. There are several ways the exchange can go wrong. The tool can choose NOT to send you a key, or send you one that doesn’t work. There are NO guarantees that compliance will gain you control over your data. None. And, here’s the thing. Even if you pay up, you don’t get rid of the encrypting tool itself. It’s still there. There aren’t enough ways to stress that. The ransomware remains. Don’t allow naivety lead you to paying the ransom. Don’t let extortionist cyber criminals get away with your money. They WILL double-cross you. After all, they’re untrustworthy individuals. They invaded your PC and took your data hostage, only to extort you for monetary gain. Don’t think that if you pay, the problem will go away. It will still be there. Don’t fool yourself. Wanting the infection to go away does not make it go away. You can’t wish the issue away. Wishful thinking doesn’t work! The American presidency race has proved that beyond the doubt.
How did I get infected with?
How does the Donald Trump ransomware slither into your system? Well, like all other ransomware do! It’s not special at all. It follows the same pattern of infiltration, and uses the same invasive tactics. In fact, it’s just like all the other cyber threats, plaguing the web. It’s rather average. It turns to the same old tricks to sneak into your system. Freeware, spam email attachments, corrupted links or sites. Pretending to be a bogus update is also an option. For example, you believe you’re updating your Java, but you’re wrong. In actuality, you’re installing an infection. And, here’s another resemblance with the presidential candidate! You think you’re allowing a trustworthy, sober-minded person into Office, but you’re not. In reality, you’re giving a toddler the power to control nukes. To recap, the Donald Trump ransomware uses the old but gold means to invade your system. It relies on your naivety and haste, and preys on your carelessness. It’s like all other cyber threats. It may bear the name of a special little snowflake, but it’s not special at all. Much like that snowflake that’s just lying to itself. If you wish to avoid the Trump infection, be more careful and attentive. Do your due diligence today. So you’re not faced with problems, you could have prevented, tomorrow.
Why is Donald Trump dangerous?
Let’s make the joke, we all knew was coming. The Donald Trump ransomware is building a wall between you and your files! Yes, after the nasty tool sneaks into your PC, it goes to work and does what it’s programmed to do. It stands between you and your data by encrypting it. It takes your files hostage, and locks them so you can no longer access them. Unlike Donald, however, the Donald Trump ransomware doesn’t discriminate. It locks all your files, and every single one gets encrypted. It spreads its tiny metaphorical fingers throughout your entire system, and takes hold of your data. It adds the ‘encrypted’ extension at the end of each one, thus, solidifying its grip over it. For example, if you have a video called “DonaldTrumpIsATrafficCone,” it becomes “DonaldTrumpIsATrafficCone.encrypted.” Once the extension is there, you can’t open your files. All your music, videos, pictures, documents, everything, is beyond your reach. Renaming or moving them won’t work. The only way to free them is with the decryption key. And, of course, it costs money. Whatever the ransomware asks you to pay, do NOT pay it! Even if it’s one single cent, do NOT do it! If you pay, chances are, you’ll find yourself into a bigger mess. Why? Well, if you transfer the requested sum, you give access to your privacy to strangers. The cyber criminals behind the Donald Trump infection get your personal and financial details. Do you think that will end well? Hardly. Don’t take chances! Don’t pay! If you’re a victim of the Donald Trump ransomware, it’s better to say goodbye to your files. The alternatives are much worse. After all, data is replaceable. Privacy is not.
Donald Trump Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Donald Trump Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Donald Trump encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Donald Trump encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



