Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Cry Ransomware?
Reader recently start to report the following message being displayed when they boot their computer:
Central Security Treatment Organization Department of pre-trial settlement
Warning! Your files are encrypted!
Your documents, databases, project files, audio and video content and other critical files have been encrypted with a persistent military-grade crypto algorithm!!! To restore the access to your files you need to pay commission for the decryption in amount of $625
Only after the commission is paid in full you will be provided with the special software for the encrypted data recovery.
Important
In the case of non-payment of the full commission within 4d 4h , the amount of commission will be raised to $1250 Attention required Do not take any actions to decrypt your files on your own! This is absolutely impossible and can lead to the encrypted data corruption and, therefore, it can not be recovered in the future! In case of the repeated non-payment of the increased commission during the 4d 4h period, the unique decryption code for your files will be blocked and its recovery will be absolutely impossible!
Cry Ransomware. Oh, there might be crying involved. Despite being unusual, this name is actually quite appropriate. We’ve already tackled Cerber, Cerber2, Cerber3, Locky, Juicy Lemon and Chimera. Therefore, Cry Ransomware (CryLocker) isn’t the weirdest name out there. It’s one of the newest file-encrypting infections. Those of you who’ve stumbled across ransomware, know exactly what makes these programs dangerous. There’s a reason why most PC users dread ransomware. Also, there’s a reason why hackers constantly keep working on new parasites of this kind. To learn more about these viruses and the ways to deal with them, keep on reading. First things first, how does Cry Ransomware work? It scans your machine thoroughly and locates your files. Yes, all your files. Pictures, music, MS Office documents, presentations, videos. Anything of value you might have stored on the device falls victim to this parasite. It goes without saying there are probably some precious files on board. After Cry Ransomware finds your data, encryption begins. The parasite infects .jpg, .jpeg, .png, .pdf, .mp3, .mp4 and many more file formats. It replaces the original file extension with a malicious one – “.cry”. If you see this appendix, that is it. Your data is no longer accessible and your files are practically useless. Why does this program goes after your personal files, you may ask? Because it’s aiming at your bank account. You’re now involved in a nasty attempt for a cyber fraud. Yes, this is why ransomware exists in the first place. These programs hold your files hostage and demand a ransom. This is how hackers make illegitimate profit online. They strike where it hurts the most – at your private files. Your memories, your hobbies, your work-related documents. It’s crystal clear that ransomware could cause irreversible damage. This pest moves all the encrypted data to your desktop. Then it creates a folder called “old_shortcuts” and fills it with your locked information. Unfortunately, this is not all. Cry Ransomware also creates a ransom message. You will find !Recovery_[6 random characters].txt and !Recovery_[6 random characters].html files on your desktop. They contain detailed payment instructions. As mentioned, ransomware is trying to blackmail you. According to its ransom messages, you must pay a certain sum of money in exchange for a decryption key. The sum demanded isn’t a small one either. However, there’s no guarantee crooks will keep their end of the bargain. Don’t even consider paying the money.
How did I get infected with?
Cry Ransomware follows the classic rules. It mainly travels the Web as a spam email-attachment. This way, all you need to do in order to set the virus free is click the email open. It’s just that easy. Hackers often send ransomware directly to your inbox so make no mistake. Avoid spam emails and messages from unknown senders. You won’t regret it. In addition, stay away from illegitimate torrents, websites and software. You only get what you pay for. Keep in mind that “free of charge” and “infection-free” are two drastically different categories. Ransomware might get spread online with the help of a Trojan horse as well. That means you have to check out the PC thoroughly for more infections. The Cry Ransomware may not be the only parasite on board. Last but not least, watch out for fake software updates. The Web is infested with malware so make sure you protect your safety.
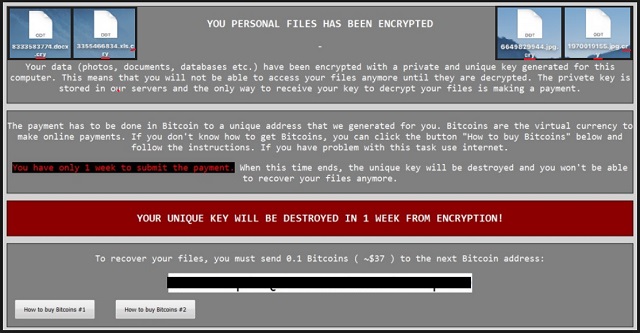
Why is Cry dangerous?
The Cry Ransomware is a complete and utter pest. By adding its malicious “.cry” extension, it denies you access to your own files. Just take a moment and think about it. You can’t use your very own information that you’ve stored on your very own computer. Furthermore, hackers are impudent enough to directly ask for money. Cry Ransomware demands 150 USD. That’s 150 USD for the privilege to free your pictures and music. Does it seem to be a fair deal? Unless you make the payment in the next 100 hours, the ransom doubles. Cry Ransomware has one more trick up its sleeve. This program provides a web link that leads you to a fake website. This bogus page claims to be a “Central Security Treatment Organization (Department of pre-trial settlement)”. That’s just one more way to scare you into paying the ransom. Remember, you’re seeing a fake logo of a non-existing organization. In reality, you’d be giving your Bitcoins to greedy and dishonest cyber criminals. In order not to become a sponsor of crooks, get rid of their ransomware. To delete it manually, please follow our detailed removal guide down below.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Cry Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Cry Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Cry encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Cry encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



