Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Aleta Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
[WHAT HAPPENED]
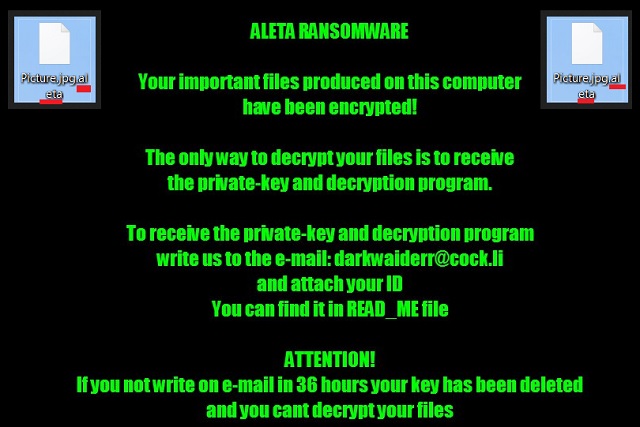
Your important files produced on this computer have been encrypted due a security problem
If you want to restore them, write us to the e-mail: black.mirror@qq.com
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us.
After payment, we will send you the decryption tool that will decrypt all your files.
[FREE DECRYPTION AS GUARANTEE]
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information
and their total size must be less than 1Mb
[HOW TO OBTAIN BITCOINS]
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller by payment method and price
h[tt]ps://localbitcoins.com/buy_bitcoins
[ATTENTION]
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 36 hours – your key has been deleted and you cant decrypt your files
Your ID: [RANDOM CHARACTERS]
Today’s article is all about a brand new ransomware virus. AKA, the latest version of BTCWare Ransomware. This parasite sneaks itself onto your machine in silence and encrypts your files. Yes, all your files. There is a reason why most PC users dread file-encrypting infections. Being extremely aggressive and problematic, these programs inevitably cause a mess. Unless you take immediate measures, ransomware could cause you irreversible harm. As mentioned, the virus lands on board behind your back. You remain absolutely oblivious to the fact you have been infected with ransomware. And the parasite isn’t going to waste any time. The virus gets activated as soon as it gets downloaded and performs a scan. By doing so, this pest locates all your sensitive information. We’re talking pictures, music files, videos, documents. A great variety of formats falls victim to the ransomware. The parasite targets such a huge percentage of your data because it is about to play some mind games with you. You see, once the scan is complete, encryption begins. All your files get locked out of the blue; they are left renamed and unreadable. Ransomware uses a complicated encrypting algorithm to lock your information. Such a strong cipher successfully denies you access to your files. Do you keep precious data on your machine? Perhaps you do. In the future, always be prepared in case another ransomware pest gets to you. Keep backups of your data so you know no infection could try to blackmail you. Now that you’ve crossed paths with ransomware, are you willing to go through it again? This parasite renames your files. That is how you can tell whether the encrypting process has ended. You will notice an “email.[black.mirror@qq.com].aleta” file extension after your files get locked. When you do come across this appendix, know the ransomware is holding your data hostage. It is about to lie to your face demanding a ransom. While encrypting the target files, this program drops !#_READ_ME_#!.inf. Those are your detailed payment instructions because you’re supposed to buy a decryption key. Do you see the scam? Your important, favorite files get suddenly locked. They are impossible to open and you can’t use any of them anymore. It goes without saying this trick could make you very nervous. Unfortunately, that’s exactly what hackers are aiming for. If you give into your panic and frustration, you end up getting involved in a scam.
How did I get infected with?
Ransomware is just a computer program that needs your permission to get installed. The problem is, these infections usually trick you into downloading them. For instance, this program probably pretended to be something else. The most commonly used method involves spam messages or email-attachments. When you receive such random emails/messages, keep an eye out for malware. Hackers could be impudent enough to sent infections straight to your inbox. If you click the corrupted email open, you let the virus hiding in there loose. As you could imagine, removing viruses is indeed a greater hassle than preventing installation. Always be cautious in order to protect your device from intruders. Also, we’d recommend that you avoid illegitimate websites and programs. Stay away from unverified software, especially if it comes in a bundle. Only download programs that you trust and remember that parasites need a single moment of your haste. Thus, watch out for malware and don’t underestimate hackers’ creativity. Ransomware could also travel the Web via exploit kits. Last but not least, these viruses might use help from other parasites (Trojan horses). Definitely check out your device for further cyber threats.
Why is Aleta dangerous?
According to the parasite’s ransom notes, you have to make a payment. The virus demands 2 Bitcoins which equals 4985 USD at the moment. Are you really willing to give hackers almost 5000 dollars for a decryptor? You should also keep in mind there’s no guarantee crooks would follow the rules. To put it mildly, hackers aren’t famous for being honorable people. In fact, cyber criminals keep on creating ransomware to gain illegal profit online. They are solely focused on scamming you so you can forget about the bogus decryption key right away. This is just a lie crooks use to blackmail gullible PC users. Don’t reward hackers for locking your private files. Don’t pay the ransom. Paying the sum demanded would only make matters worse so keep your Bitcoins. To delete the ransomware, please follow our comprehensive manual removal guide. You will find it down below.
Aleta Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Aleta Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Aleta encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Aleta encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



