Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Zobm Ransomware?
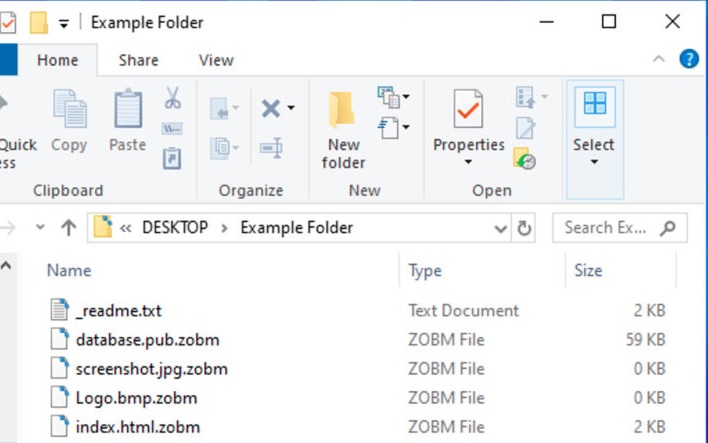
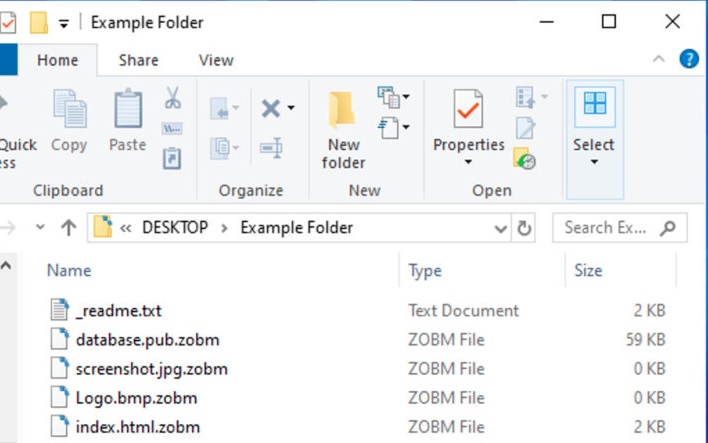
Zobm is a cryptovirus planned for extorting its unfortunate users for their cash. To do this, Zobm renders all important personal files unavailable through encryption and requests a payoff to give a decryption key. The Zobm Ransomware will begin encoding your documents the minute it infiltrates your machine.
How did I get infected with?
What you have to think about such kinds of malware is that they will in all likelihood run ан encryption process out of sight of the system and without indicating obvious side effects. At that point, they will ask the unfortunate user whose information has been scrambled to pay a specific amount of cash as a ransom.
Why is Zobm dangerous?
Zobm ransomware is a threat. It sneaks into your PC and wrecks everything. The infection encrypts your information and makes it difficult to reach. Zobm makes your PC useless. It pushes you to pay the ransom. Practice shows that the crooks will in general overlook their exploited people once they get the cash. There are situations when the exploited people paid just to be coerced for more. There are additionally occurrences when the unfortunate users got nonfunctional or halfway practical decoding instruments. What will you do if this transpires? You can’t request a discount. You are helping crooks who request digital coins. Nobody can follow these monetary standards. When you complete the exchange, there’s no returning. Try not to get the ball rolling. Consider disposing of your records. On the off chance that you have reinforcements saved money on outer gadgets, you can utilize them to reestablish your information. Simply ensure that .Zobm is totally expelled before you endeavor any such exercises.
Zobm Removal Instructions
STEP 1: Kill the Malicious Process
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 3: Locate Startup Location
STEP 4: Recover Zobm Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Zobm encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Zobm encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.