Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
This article can help you to remove Zeb89 Virus. The step by step removal works for every version of Microsoft Windows.
Zeb89 is a secretive, sneaky Trojan horse. It modifies your system registry behind your back and exposes you to cyber threats. Furthermore, the parasite jeopardizes your privacy and steals some immensely personal details. Long story short, Trojans are problematic. The Zeb89 infection has all the malicious potential it needs to cause you damage. To prevent it, you have to take immediate action and uninstall this nuisance. The sooner you take measures, the better. Keep in mind that a virus only becomes more and more destructive as time passes. Instead of putting up with this program’s shenanigans, you have to uninstall it. Simple as that. Trojans are full of surprises so Zeb89 is quite unpredictable. The parasite has a rich variety of tricks to offer. It starts harassing you by modifying your PC settings. Your preferred, default settings get altered without any permission. It goes without saying how dangerous that is. Zeb89 changes your system registry. It might modify some system files and damage others. Therefore, the virus will affect the way your machine performs. For instance, you may notice that some of your programs don’t run. That is one of the very few tell-tale signs that an infection is present. Be careful because if you spot a virus on board, you have to tackle it ASAP. Zeb89 might spend a good while on your machine without your knowledge. Also, pay attention to the PC speed. A Trojan horse causes your computer to underperform, to crash or freeze. You may also experience the dreaded Blue Screen of Death. Long story short, this program makes using your device impossible. In addition, it serves as a back door to malware. More often than not, Trojans help ransomware get spread online. And ransomware is perhaps the most vicious, cunning type of virus you could come across. To prevent further harm, get rid of the Zeb89 parasite. This nuisance might mess with your default browser settings as well. That means Zeb89 could modify your search engine or homepage and hijack your browsers. As you can tell, you have no reason to tolerate the infection. On the other hand, you have plenty of reasons to uninstall it.

How did I get infected with?
Trojans don’t usually deviate from the classic infiltration methods. The most popular technique they apply is also the oldest trick in the books. We’re talking about spam messages and fake email-attachments. You see, hackers tend to send infections straight to your inbox. You actually end up compromising your own machine by clicking the fake email open. To protect your device, delete anything untrustworthy you may receive. Bear in mind that the Internet is full of malicious programs so you can’t afford to overlook the threat. Unless you constantly keep an eye out for parasites, you might accidentally install viruses. We’d recommend that you avoid opening suspicious-looking emails, especially if their senders are unknown. Save yourself the headache that dealing with parasites causes. Put your security first. Another commonly used tactic involves fake torrents as well as corrupted software updates. Last but not least, always check out the bundles you download for additional programs. There might be some nasty infection hiding in a seemingly safe freeware or shareware bundle.
Why is this dangerous?
The Trojan successfully wreaks havoc and slows down your PC speed. It could also get to your browser settings and alter them. In this scenario, this program begins to redirect you. Yes, you could land directly on malicious websites filled with parasites. Zeb89 keeps on exposing you to more infections till the moment you take action. Do that quickly so the pest can’t cause you serious damage. This nuisance spies on your browsing-related data as well. It collects browsing history and usernames and passwords and IP addresses. All this information gets sent into the greedy hands of hackers. Also, the Trojan horse could grant them remote control over your very own computer. It puts both your safety and privacy in danger. You may even fall victim to identity theft if Zeb89 steals some personally identifiable details. Make no mistake with this virus. To delete it for good, please follow our detailed manual removal guide down below.
Manual Zeb89 Removal Instructions
The Zeb89 infection is specifically designed to make money to its creators one way or another. The specialists from various antivirus companies like Bitdefender, Kaspersky, Norton, Avast, ESET, etc. advise that there is no harmless virus.
If you perform exactly the steps below you should be able to remove the Zeb89 infection. Please, follow the procedures in the exact order. Please, consider to print this guide or have another computer at your disposal. You will NOT need any USB sticks or CDs.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Track down Zeb89 related processes in the computer memory
STEP 2: Locate Zeb89 startup location
STEP 3: Delete Zeb89 traces from Chrome, Firefox and Internet Explorer
STEP 4: Undo the damage done by the virus
STEP 1: Track down Zeb89 related processes in the computer memory
- Open your Task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Carefully review all processes and stop the suspicious ones.

- Write down the file location for later reference.
Step 2: Locate Zeb89 startup location
Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
Clean Zeb89 virus from the windows registry
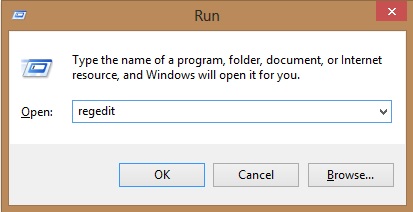
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to: %appdata% folder and delete the malicious executable.
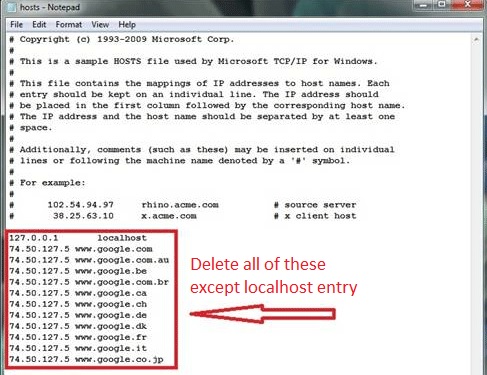
Clean your HOSTS file to avoid unwanted browser redirection
Navigate to %windir%/system32/Drivers/etc/host
If you are hacked, there will be foreign IPs addresses connected to you at the bottom. Take a look below:
Step 4: Undo the possible damage done by Zeb89
This particular Virus may alter your DNS settings.
Attention! this can break your internet connection. Before you change your DNS settings to use Google Public DNS for Zeb89, be sure to write down the current server addresses on a piece of paper.
To fix the damage done by the virus you need to do the following.
- Click the Windows Start button to open the Start Menu, type control panel in the search box and select Control Panel in the results displayed above.
- go to Network and Internet
- then Network and Sharing Center
- then Change Adapter Settings
- Right-click on your active internet connection and click properties. Under the Networking tab, find Internet Protocol Version 4 (TCP/IPv4). Left click on it and then click on properties. Both options should be automatic! By default it should be set to “Obtain an IP address automatically” and the second one to “Obtain DNS server address automatically!” If they are not just change them, however if you are part of a domain network you should contact your Domain Administrator to set these settings, otherwise the internet connection will break!!!
- Check your scheduled tasks to make sure the virus will not download itself again.
How to Permanently Remove Zeb89 Virus (automatic) Removal Guide
Please, have in mind that once you are infected with a single virus, it compromises your whole system or network and let all doors wide open for many other infections. To make sure manual removal is successful, we recommend to use a free scanner of any professional antimalware program to identify possible virus leftovers or temporary files.