Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
If you are seeing a message on your desktop that “Your personal files are encrypted!” and there is a countdown timer – then you are in a serious trouble. You probably got the Most Destructive Malware in 2013 – it is called Cryptolocker. This is the scariest Ransomware being developed even right now. This computer parasite first was noticed in the beginning of September 2013. It is targeting various Windows Operating Systems including Windows XP, Windows Vista. Windows 7 and Windows 8. When the malware does its dirty work it will pop-up and ask you to pay a ransom of either 100 USD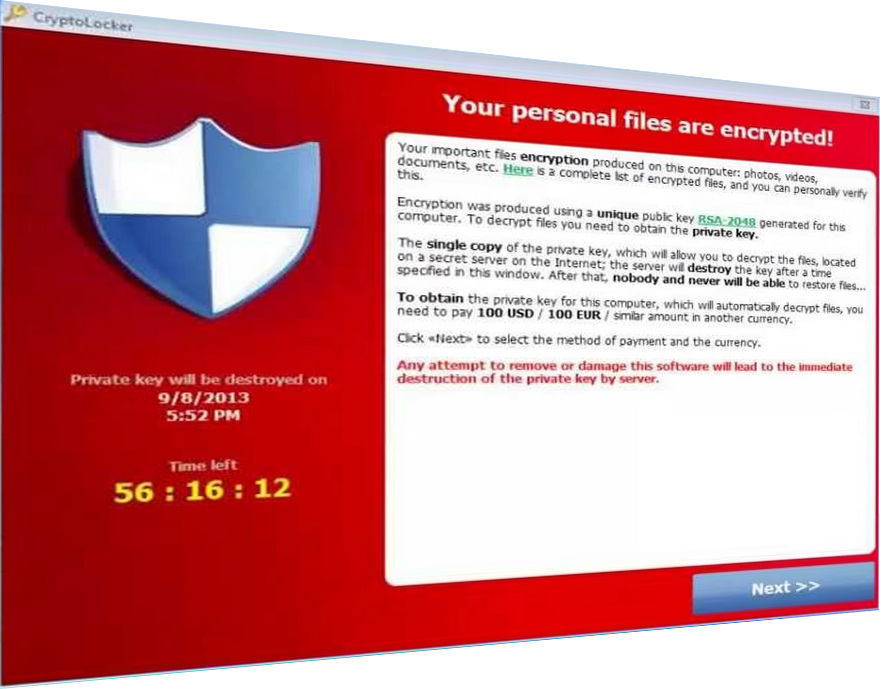
or 300 USD in order to decrypt all your documents and pictures depending of the version of the malware you’ve got. It will display a countdown timer as well. When the time ends, the chance of recovering your files through conventional means is completely lost.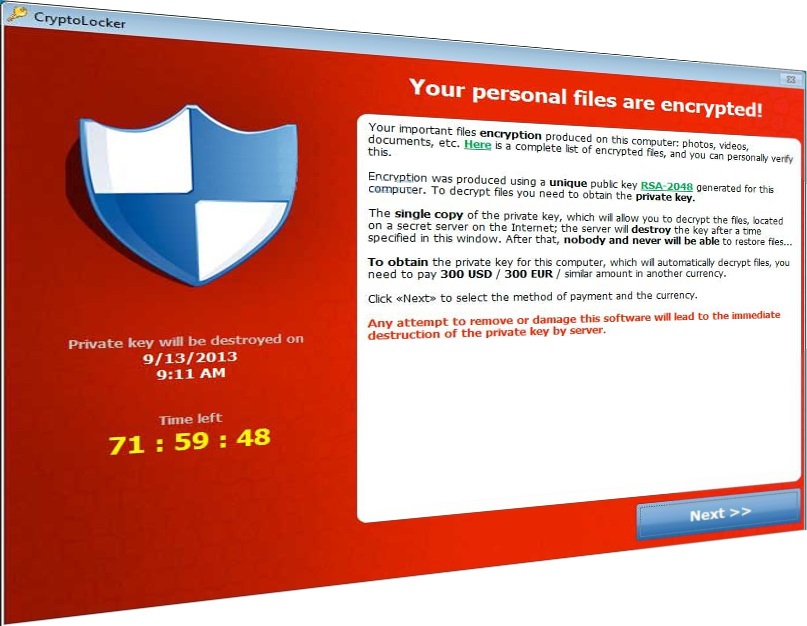
However, the recent modifications of the parasite offer a decryption service for an even greater price: 10 Bitcoins (the price of Bitcoins is increasing tremendously recently).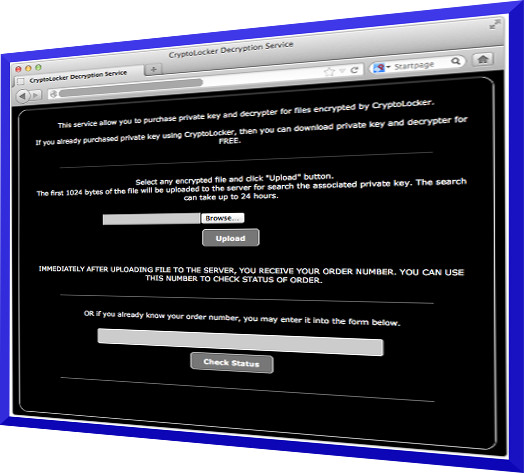
The infection is mainly distributed by emails and exploited web sites using random generated droppers. Once the ransomware is executed it adds a point of execution in the registry key:
KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “CryptoLocker”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce “*CryptoLocker”
KEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “CryptoLocker_<version_number>”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce “*CryptoLocker_<version_number”
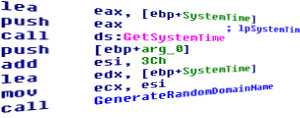
Communication with the command and control server is established through either a hardcoded IP or if that fails through a random domain generation algorithm located at 0x40FDD0.
The communication is RSA encrypted. Using this type of encryption not only allows the hackers to obfuscate the real communication between the victim and the server, but to make sure the malware is talking to a real victim and not to a controlled by malware researchers testbed.
You can extract the public key at offset 0x00010da0 within the malware file. In its initial contact the ransomware will send a string that contains the version, system language, generated ID and group ID. The response from the server is a RSA public key.
It looks something like that:
—–BEGIN PUBLIC KEY—–
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAkQBZgSk3NNo54cx
wl3nSzZHMhFI4oU0ygX81IFsktcaCAIUrMSnUVQEcFvhcidh/5JuE+piQY5Z3i
uDcKqiF0yWZ7rck+xC1i/xaY5nNxJnh/clEqO8qRNg9DTe6qDlVO8PAHgr882
dUHTzZgdANOWR8+5rWxck9LxtB8+DSE8cWy
After that this key is saved inside the registry. If you want to collect the key on your infected system, you just need to break on CryptStringtoBinaryA.
The ransomware will encrypt files with the following extensions:
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.eps, *.ai, *.indd, *.cdr, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c
For every file that match any of the above patterns, the ransomware will create a new 256 bit AES key that will be used to encrypt the content of the file. The AES key is then encrypted using the unique public RSA key above. Both the RSA encrypted AES key and the content of the AES encrypted file along with some more info are input back to the file
The above information is implying that this ransomware is specifically developed for business users and is ignoring to some extend the ordinary people. The end result of that infection is that all the files in your computer that has the above extensions will be rendered completely unusable.
Unfortunately, even if the parasite is removed, your personal files will remain encrypted and decryption at this point is almost impossible without the private RSA key that is stored on the server controlled by the hackers.
You should never pay the ransom, as the funds will be probably used for development of even worse malware or creating a digital warfare. In How To Restore Encrypted By Cryptolocker Files article I am describing several ways that may help you to retrieve some of the lost information without paying the ransom and in the article How To Avoid Cryptolocker Infection to prevent this from happening on the first place.