Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wyvern Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
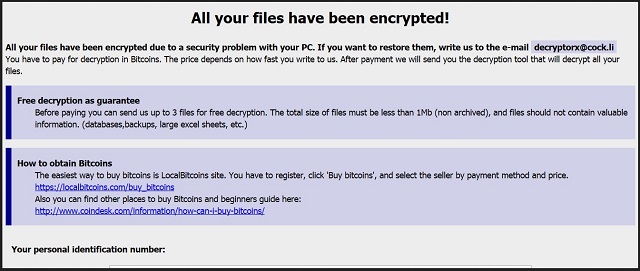
All your files have been encrypted!
All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail decryptorx@cock.li
You have to pay for decryption in Bitcoins. The price depends on how fast you write to us. After payment we will send you the decryption tool that will decrypt all your files.
Free decryption as guarantee
Before paying you can send us up to 3 files for free decryption. The total size of files must be less than 1Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.)
How to obtain Bitcoins
The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click ‘Buy bitcoins’, and select the seller by payment method and price.
https://localbitcoins(.)com/buy_bitcoins
Also you can find other places to buy Bitcoins and beginners guide here:
http://www.coindesk(.)com/information/how-can-i-buy-bitcoins/
Attention!
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.
Your ID: [redacted]
Ransomware is, quite possibly, the worst cyber threat you can catch. That’s not a statement, made lightly. These infections have earned their reputation. Unfortunately, you’re about to discover why they have. The Wyvern tool belongs to the dreaded category. It’s a new version of the BTCWare threat. And, if you come across it, you’re in for a horrendous experience. The malicious program gains access to your PC via trickery. It dupes you into allowing in, yourself. Then, after you permit its entry, it takes over. The tool spreads its clutches throughout, and takes hold of your system. As time goes by, its grip only tightens. You cannot escape the tool’s influence. For, it spreads its nastiness through every corner of your computer. Once the program activates, it encrypts every file you have. All the data, you keep on your PC, gets locked. If you wish to unlock it, you have to comply. The infection insist you follow its demands, or you’ll never see your data decrypted again. It places a simple dilemma in front of you. Well, at least it seems simple. Pay a ransom to decrypt your files. Or, don’t, and lose them forever. Well, here’s what the tool keeps from you. It’s not as simple of an exchange as the cyber extortionists would have you believe. The return of your files is not as certain as you hope. Compliance and payment mean nothing to these people. They are not bound to keep their end of the bargain. So, can you really trust them to follow through on their promises? Don’t. Don’t place your faith in cyber criminals, who extort you for money. They’re hardly trustworthy individuals. As unfortunate as it may be, accept defeat. Cut your losses, and say goodbye to your files. After the tool takes over, encrypts your data, and displays the note, do nothing. Don’t contact them. Don’t pay them. Don’t reach out in any way. Discard your data, and move on. Next time, create back-ups.
How did I get infected with?
Wyvern turns to the usual antics to invade. It spreads via tactics, you’ve come to expect. Like, it hides behind freeware. And, if you’re not careful enough during install. And, rush, and not bother to read the terms and conditions, that’s it. You end up with it. Carelessness costs you. Infections, like Wyvern, prey on it. They need your distraction, naivety, and haste to ensure their sneaky access. Don’t grant them. Don’t ease the ransomware’s infiltration. Always be on your guard when allowing anything, off the web, into your PC. It’s a dangerous place, after all. Be extra vigilant when opening files right after having downloaded them. That’s particularly important when it comes to anything you get off of suspicious emails or links. As stated, the infection has an entire array of ways to use to invade. One such way, is to turn to file-sharing networks. As well as, to spread via payload file on social media sites. Remember! Caution is your best friend. Always take the time to do your due diligence. It can save you a ton of troubles. Double-check everything. Look for the fine print. A little extra attention can’t hurt, but it can help you. ‘Better safe than sorry’ is the way to go.

Why is Wyvern dangerous?
The infection doesn’t waste time, and acts up not long after invasion. It targets every file, you have on your computer. Documents, music, photos, videos, nothing is beyond its reach. The Wyvern tool earns its name from the extension it appends to your files. At the end of each one, you find “.wyvern.” For example, the picture “summer.jpg” becomes “summer.jpg.wyvern.” That extension renders the file unusable. You cannot open it anymore. And, moving or renaming it, does nothing. The only way to access it again, is to pay the ransom. Once you do that, the data kidnappers send you a decryption key. Apply it, and voila! Your files are locked no more. But, there’s a catch, of course. The key, you pay for, only removes the encryption. It does nothing for the infection itself. The Wyvern plague remains. It’s free to strike again at any given moment. It could be a minute after decryption, a week, a month. There’s no way to tell. But even that uncertainty and danger is nothing compared to the bigger threat. By paying these people, you expose yourself to them. You provide personal and financial details when transferring the money. Information, which you leave for the extortionists to find. And, once they get a hold of it, they can use it as they see fit. Do you think your data is worth that exposure? Don’t forget. Data is replaceable. Privacy is not. Don’t pay these people. Pick the lesser evil, and forsake your files. Yes, it’s a tough call to make. But, it’s the right one.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Wyvern Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Wyvern Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wyvern encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wyvern encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.