Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wannasmile Ransomware?
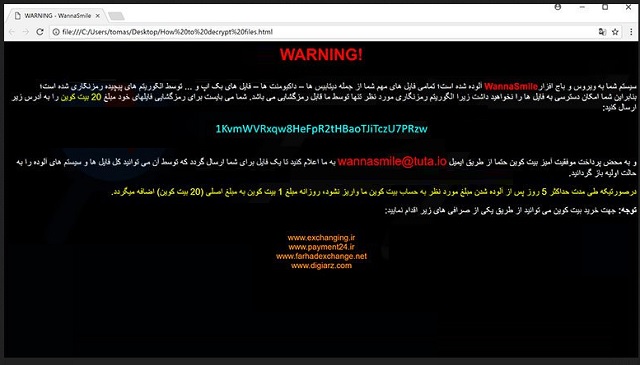
Readers recently started to report the following message being displayed when they boot their computer:
WARNING!
سیستم شما به ویروس و باج افزارWannaSmile آلوده شده است؛ تمامی فایل های مهم شما از جمله دیتابیس ها – داکیومنت ها – فایل های بک آپ و … توسط الگوریتم های پیچیده رمزنگاری شده است؛
بنابراین شما امکان دسترسی به فایل ها را نخواهید داشت زیرا الگوریتم رمزنگاری مورد نظر تنها توسط ما قابل رمزگشایی می باشد. شما می بایست برای رمزگشایی فایلهای خود مبلغ 20 بیت کوین را به آدرس زیر ارسال کنید:
1KvmWVRxqw8HeFpR2tHBaoTJiTczU7PRzw
و به محض پرداخت موفقیت آمیز بیت کوین حتما از طریق ایمیل wannasmile@tuta.io به ما اعلام کنید تا یک فایل برای شما ارسال گردد که توسط آن می توانید کل فایل ها و سیستم های آلوده را به حالت اولیه باز گردانید.
درصورتیکه طی مدت حداکثر 5 روز پس از آلوده شدن مبلغ مورد نظر به حساب بیت کوین ما واریز نشود، روزانه مبلغ 1 بیت کوین به مبلغ اصلی (20 بیت کوین) اضافه میگردد.
توجه: جهت خرید بیت کوین می توانید از طریق یکی از صرافی های زیر اقدام نمایید:
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
Wannasmile is the newest member of the ransomware family. This virus is a deadly infection. It sneaks into your computer unnoticed and locks your personal files. You can still see the icons of your pictures, videos, databases, music, office files, etc., but you cannot open or use them. Well, there is a slight difference in the name of the files. The Wannasmile Ransomware ads the “.WSmile” extension at the end of each encrypted file. Thus, if you have a file named example.txt, the virus will rename it to example.txt.WSmile. Following a successful installation, the ransomware scans your HDD your target files. It uses a combination of AES and RSA algorithms to lock these files. Once the encryption process is complete, the virus changes your desktop background with a black wallpaper. Your new background is the actual ransom note. Wannasmile also drops a file named “How to decrypt files.html.” It contains the same information as the wallpaper. Now, what is interesting about the note is that it is written in Persian. Basically, it explains what has happened to your files and what the demanded ransom is. The hackers ask for 20 Bitcoin (about $165164.5USD) in exchange for a decryption tool. Just for a comparison, most ransomware viruses demand about 0.5 Bitcoin. Wannasmile demands an astonishing amount of money. We must specify that this ransomware targets the business. Yet, there are also private computers which got infected with it. According to the ransom note, the victims are supposed to transfer the ransom, then to contact the crooks via email (wannasmile@tuta.io) and to wait for a reply. We recommend against such actions. The hackers are known to ignore the victims once the ransom is paid. You are dealing with cyber criminals after all. You cannot expect them to play fair. Your best course of action is the immediate removal of the virus. We recommend you to use a powerful anti-virus program. We have also provided a manual removal below this article. However, be advised. Wannasmile Ransomware is a sophisticated infection. Its removal is a bit complicated. Using an automated solution is the easiest and safest way to clean your device.
How did I get infected with?
Wannasmile Ransomware is mainly distributed via spam emails. You know how it works. You receive an email from a stranger. It looks interesting. Quite often, the scammers write on behalf of local organizations, banks, post offices and police departments. You are tempted by the received email and you open it. It states that something urgent must be done. Of course, the message contains an attached file. You, however, have heard about too many viruses to know better. Luckily, the email also contains a hyperlink which is supposed to give you more information on the matter. You click on it. Unfortunately, what you don’t know is that the hyperlinks can also be corrupted. By clicking on this link, you’ve infected your device. The crooks are imaginative. They know how to push you into impulsive actions. Before you even open an email, verify the sender. You can simply enter the questionable email address into some search engine. If it was used for shady business, someone might have complained online. Don’t stop here. When you receive letters from organizations or companies, go to their official websites. Compare the email addresses listed there with the one you have received a message from. If they don’t match, you are definitely dealing with a pretender. Delete this imposter immediately. Wannasmile Ransomware can also be distributed via torrents, bogus software updates, and malvertising. The key to a secure and infection-free computer is caution. Always do your due diligence.
Why is Wannasmile dangerous?
Wannasmile Ransomware has entered your device uninvited and locked your files. The virus is blackmailing you. It is also making your computer useless. If you create new files, the virus will encrypt them too. This infection is a dead end. There is nothing you can do to recover your files for free. There are no alternative decryptors. Even if you pay the ransom, the positive outcome is not guaranteed. Don’t negotiate with criminals. You cannot win. Do not contact the hackers, they may use this opportunity to track you down and blackmail you. Whatever you do, don’t pay the ransom. Also, avoid using your computer for online purchases and banking. The ransomware is probably spying on you. Your best course of action is the immediate removal of the infection. Use an anti-virus app to clean your machine as soon as possible.
Wannasmile Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Wannasmile Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wannasmile encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wannasmile encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



