Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Wannacrypt Ransomware?
Readers recently started to report the following message being displayed when they boot their computer:
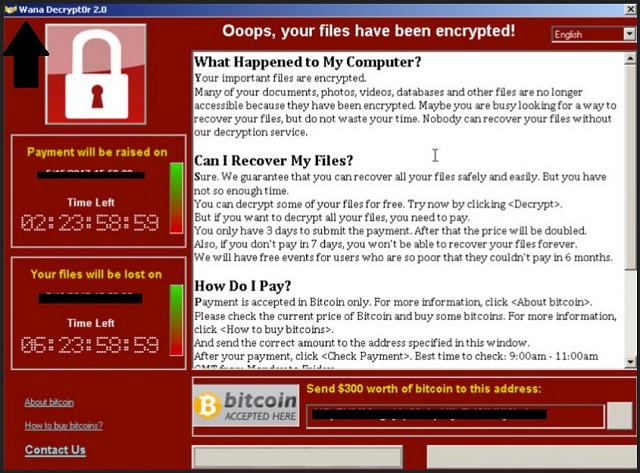
What Happened to My Computer?
Your important files are encrypted.
Many of your documents, photos, videos, databases and other files are no longer accessible because they have been encrypted. Maybe you are busy looking for a way to recover your files, but do not waste your time. Nobody can recover your files without our decryption service.
Can I Recover My Files?
Sure. We guarantee that you can recover all your files safely and easily. But you have not so enough time.
You can decrypt some of your files for free. Try now by clicking .
But if you want to decrypt all your files, you need to pay.
You only have 3 days to submit the payment. After that the price will be doubled.
Also, if you don’t pay in 7 days, you won’t be able to recover your files forever.
We will have free events for users who are so poor that they couldn’t pay in 6 months.
How Do I Pay?
Payment is accepted in Bitcoin only. For more information, click .
Please check the current price of Bitcoin and buy some bitcoins. For more information, click .
And send the correct amount to the address specified in this window.
After your payment, click . Best time to check: 9:00am – 11:00am GMT from Monday to Friday.
Once the payment is checked, you can start decrypting your files immediately.
Unfortunately, Wannacrypt Ransomware does want to encrypt. This problematic infection is one of the newest members of the ransomware family. And ransomware is certainly not something you would want to deal with. File-encrypting parasites are on the rise right now but they are popular for all the wrong reasons. You see, hackers always try to gain profit online. Ransomware provides them a quick and effortless way to scam innocent PC users. Eventually, such an infection helps cyber criminals make money online. Crooks constantly keep on developing ransomware parasites. We see quite an impressive variety of file-encrypting infections. However, it’s safe to say most programs of the kind follow the same pattern. So does the Wannacrypt Ransomware that you’re stuck with. As mentioned already, ransomware is a particularly dreaded type of virus. Immediately after it gets installed, the parasite performs a scan of your device. As a result, Wannacrypt Ransomware locates every single file you have. Yes, ransomware attacks your private data. Hackers are perfectly aware that this would create the biggest confusion and panic. It is quite an effective trick. Your information gets encrypted all of a sudden and you’re being denied access to your files. That includes your music, photos, videos, documents, etc. Do you store important data on your PC system? Probably. It is your own computer, after all. What you should consider is keeping backup copies of your files in case another ransomware gets to you. Think in advance in order to save yourself the headache. Don’t put all your eggs in just one basket. Wannacrypt Ransomware uses a complicated encrypting algorithm to lock your files. It renames them and changes the format of your data. As you could imagine, that means your information is turned into unreadable gibberish. You’re now unable to use any of your very own, precious files. The virus also drops detailed payment instructions while encrypting your data. As we mentioned, ransomware aims at your bank account. It adds these ransom notes to all folders that contain encrypted files. Your desktop wallpaper might be modified as well. Crooks are trying to force their messages on you as much as possible. They rely on the fact you’d give into your anxiety and, ultimately, pay the ransom demanded. Paying is the very last thing you should do, though.
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How did I get infected with?
The Internet is full of potential infections. In addition to that, hackers are full of ideas when it comes to spreading malware online. Make sure you always keep an eye out for parasites. You only need one single moment of haste on the Web to compromise your safety. Ransomware uses some of the most popular infiltration tactics. The number one method involves spam emails. These corrupted emails often appear to be legitimate in order to trick you into opening them. Any random message or email-attachment from an unknown sender is potentially dangerous. Stay away from weird-looking job applications, for example. Ransomware might use fake logos or fake names to make the email more believable. Delete anything you don’t trust instead of taking risks. Ransomware-type viruses also get distributed online via bogus program updates and exploit kits. Do not download unverified software either. We would recommend that you avoid freeware/shareware bundles as those could turn out to be malicious. Last but not least, the virus could have used some help from another infection. That’s usually a stealthy Trojan horse so check out your computer for more viruses. The Wannacrypt Ransomware may not be alone.
Why is Wannacrypt dangerous?
Your files are being held hostage. The ransomware is using its cheap trickery to blackmail you so ignore its ransom notes. Remember, you would be negotiating with cyber criminals. Giving hackers money would be a terrible idea as it guarantees you nothing. Wannacrypt Ransomware was solely developed to cause you financial damage. Its creators have no reason whatsoever to set your data free. According to the ransom messages, you would receive a unique decryption key once you complete the payment. You need this decryptor to unlock your unreadable files. The problem is, you may end up with your data still encrypted AND your money gone. You’d even disclose some sensitive data that way so hackers could cause you privacy issues too. Do not get tempted to follow crooks’ instructions. Tackle the parasite. To delete it manually, please follow our detailed manual removal guide down below.
Wannacrypt Removal Instructions
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Wannacrypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Wannacrypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Wannacrypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



