Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
How to Remove Thunder Crypt Ransomware?
Thunder Crypt is the name of a vicious ransomware parasite. In other words, the most aggressive kind of cyber virus you could have downloaded. Take immediate measures and get rid of this pest as soon as possible. Thunder Crypt was discovered just a couple of days ago so it’s one of the newest threats online. However, it works as a typical ransomware program. That means you’re in for trouble and you have to be careful. Check out today’s article; you will also find a detailed removal guide down below. Such parasites get installed in silence. Furthermore, they get activated in silence and leave you oblivious to their presence. It could take you a while before you even realize something is off with your device. And the virus uses all that time to cause you damage. How can you tell whether your computer has fallen victim to ransomware? Pay attention to the PC speed. If there is a file-encrypting virus on board, the speed will be slowed down significantly. This could be a sign that a malicious infection is wreaking havoc. Once Thunder Crypt gets downloaded, it scans your device. As a result, the virus finds all your private information. Ransomware is so notoriously dreaded for a reason. The Thunder Crypt infection locates every single bit of data you’ve stored on your machine. Do you keep important files there? Most PC users do. Unfortunately, that is exactly what the creators of this program aim for. As mentioned, the parasite doesn’t manifest its presence. It relies on the element of surprise and it’s not difficult to see why. After the scan is complete, the ransomware starts locking your files. By using a complicated encrypting algorithm, this parasite locks everything. That includes the most popular file formats out there. For instance, photos, music, videos, MS Office documents. Ransomware modifies the format of the target files and renames them. And, there you go – all your precious files get encrypted out of the blue. Do you now see why ransomware is so effective? It plays mind games with you and attacks when you least expect it. While encrypting your data, the virus also drops payment instructions in attempts to convince you to give away your Bitcoins. Hackers offer you a deal – you either pay for a decryptor or your files remain encrypted. Needless to say, trusting cyber crooks would be a terrible mistake and you know it.
How did I get infected with?
Chances are, the ransomware was presented as something else. As something harmless. Instead of waiting for you to download the virus, ransomware usually gets disguised. Have you recently received some random email-attachments or a message? This is one incredibly popular malware infiltration method right now. Avoid questionable job applications/emails from shipping companies. More often than not, these hide a whole bunch of cyber infections. Be careful what you click open in the future. You might accidentally download malware and compromise your own PC. In addition, stay away from unverified torrents and suspicious programs updates. This is yet another effortless way for crooks to spread infections online. Remember that protecting your safety is entirely up to you. Now that you know for experience how problematic ransomware is, are you willing to deal with it again? Avoid illegitimate websites and always be cautious when installing bundled programs. Last but not least, ransomware could travel the Web with some help from Trojan horses. Check out your computer system to make sure you don’t have any more malicious intruders. If you’re especially unlucky, Thunder Crypt might be having company.
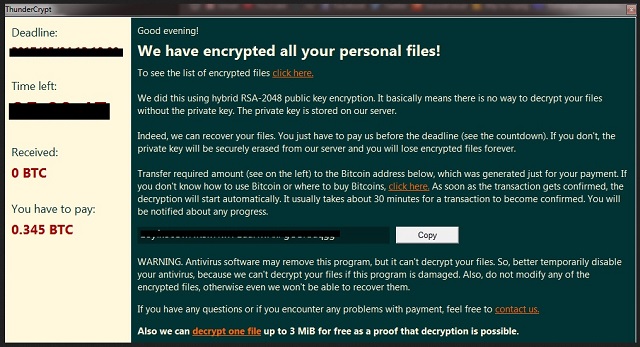
Why is Thunder Crypt dangerous?
Ransomware causes a mess. It denies you access to your very own personal files. Then it has the impudence to blackmail you. As you can see, file-encrypting programs are nothing but nasty attempts for cyber frauds. In order not to fall straight into the trap, you have to ignore the parasite’s ransom notes. Thunder Crypt drops its ransom messages and claims you need to make a payment. The sum demanded is not a small one and it’s supposed to guarantee you a decryption key. However, you should know that paying guarantees you NOTHING. Even if pay the entire ransom right away, your files might still remain locked. Hackers don’t tend to follow the rules as they are only concerned about your money. Yes, crooks are trying to gain illegal profit by scamming you. Ignore their promises for a decryption key and get rid of the virus instead. To do so manually, please follow our comprehensive removal guide down below.
Thunder Crypt Removal Instructions
Please, have in mind that SpyHunter offers a free 7-day Trial version with full functionality. Credit card is required, no charge upfront.
STEP 1: Kill the Malicious Process
STEP 3: Locate Startup Location
STEP 4: Recover Thunder Crypt Encrypted Files
STEP 1: Stop the malicious process using Windows Task Manager
- Open your task Manager by pressing CTRL+SHIFT+ESC keys simultaneously
- Locate the process of the ransomware. Have in mind that this is usually a random generated file.
- Before you kill the process, type the name on a text document for later reference.

- Locate any suspicious processes associated with Thunder Crypt encryption Virus.
- Right click on the process
- Open File Location
- End Process
- Delete the directories with the suspicious files.
- Have in mind that the process can be hiding and very difficult to detect
STEP 2: Reveal Hidden Files
- Open any folder
- Click on “Organize” button
- Choose “Folder and Search Options”
- Select the “View” tab
- Select “Show hidden files and folders” option
- Uncheck “Hide protected operating system files”
- Click “Apply” and “OK” button
STEP 3: Locate Thunder Crypt encryption Virus startup location
- Once the operating system loads press simultaneously the Windows Logo Button and the R key.
- A dialog box should open. Type “Regedit”
- WARNING! be very careful when editing the Microsoft Windows Registry as this may render the system broken.
Depending on your OS (x86 or x64) navigate to:
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run] or
[HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run]
- and delete the display Name: [RANDOM]

- Then open your explorer and navigate to:
Navigate to your %appdata% folder and delete the executable.
You can alternatively use your msconfig windows program to double check the execution point of the virus. Please, have in mind that the names in your machine might be different as they might be generated randomly, that’s why you should run any professional scanner to identify malicious files.
STEP 4: How to recover encrypted files?
- Method 1: The first and best method is to restore your data from a recent backup, in case that you have one.

- Method 2: File Recovery Software – Usually when the ransomware encrypts a file it first makes a copy of it, encrypts the copy, and then deletes the original. Due to this you may try to use file recovery software to recover some of your original files.
- Method 3: Shadow Volume Copies – As a last resort, you can try to restore your files via Shadow Volume Copies. Open the Shadow Explorer part of the package and choose the Drive you want to recover. Right click on any file you want to restore and click Export on it.



